- Sony will give you a free 55-inch 4K TV right now - but this is the last day to qualify
- I've used virtually every Linux distro, but this one has a fresh perspective
- I replaced my JBL speaker with this surprise alternative. Here's why it's my new top pick
- I replaced my JBL speaker with this surprise alternative. Here's why it's my new top pick
- Every dad should build their toolkit with theses 10 DIY gadgets
Microsoft Office 365 still the top target among phishing attacks

Most of the recent credential phishing attacks seen by Menlo Security served phony Outlook and Office 365 login pages.
Image: iStockphoto/weerapatkiatdumrong
Phishing attacks rely on exploiting popular brands, products and services in an attempt to trick anyone who uses those items. The more popular the subject, the better the odds of snagging enough people to make the campaign worth the effort. In a report published Wednesday, cloud security provider Menlo Security looks at the latest phishing campaigns and offers advice on how to avoid being a victim.
SEE: Social engineering: A cheat sheet for business professionals (free PDF) (TechRepublic)
In its report, the Menlo Tabs team said it discovered a rise in credential phishing attacks over the past month. In this popular type of campaign, the attackers create fake login pages or forms to steal credentials from corporate employees who use certain apps or services such as Office 365, Amazon Prime and Adobe.
The firm said it also found credential phishing attacks spoofing cryptocurrency wallets and popular software services from countries like South Korea.
Among the recent targets being exploited, Microsoft Office emerged at the top of the list due to the popularity of the product among organizations. The bulk of credential phishing attacks observed by Menlo Labs were trying to hoodwink users with phony login pages for Outlook and Office 365 login pages.
Some of the sectors targeted by these phishing campaigns have included travel, health and medicine, science and technology, energy and insurance. The travel industry was the hardest hit, accounting for more than half of the observed phishing attacks. Specifically, Menlo Labs found a series of attacks aimed at stealing credentials for airline duty-free accounts.

Image: Menlo Security
Cybercriminals are increasingly hosting their malicious landing pages on legitimate and popular cloud services. Such pages have been found on Microsoft Azure, OneDrive, Box, Firebase, Dropbox and even Evernote. Attackers also continually look for ways to sneak past traditional security methods. One specific page uncovered by Menlo Labs employed two tactics to evade detection:
- Hiding the actual JavaScript code that posts credentials to a remote URL.
- Encoding and embedding all custom CSS images on the page itself.
Another tactic seen in Office 365-related phishing campaigns appended the recipient’s email address to the URL. In this instance, the path for the phishing page gets generated dynamically, while the user’s email address is automatically filled in. Beyond helping the landing page skirt past traditional security, this tactic gives it a more personal touch.
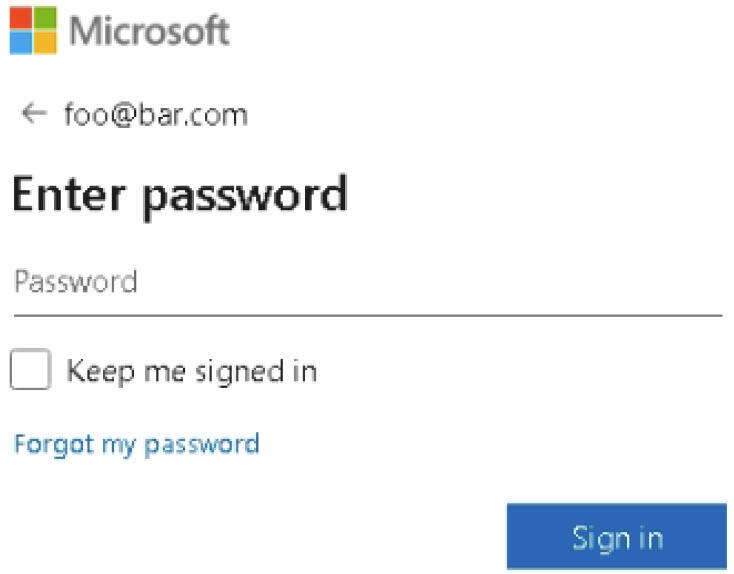
Image: Menlo Security
“Cybercriminals are trying to add complexity to carry out phishing campaigns to steal sensitive information,” the report said. “With free services like Let’s Encrypt, it is becoming increasingly easier for attackers to host phishing sites behind SSL with a relatively short TTL (time-to-live) for maximum hit rate. Increasing cybersecurity awareness through training and education initiatives is often helpful in reducing the impact of credential phishing attacks, but corporate users should be cautious when a site presents a form that asks for personal/sensitive information.”
To help your organization better defend itself against phishing attacks, Menlo Labs Researcher Krishnan Subramanian offers the following four tips:
- Be aware and attentive when typing sensitive information into a webpage. Look at the URL and address field closely to make sure it’s a trusted site.
- Follow standard security practices such as enabling multi-factor authentication and ensuring that a password rotation policy is in place.
- Have a response playbook in the event of credential theft. Make sure your playboard triggers specific actions, such as resetting a password, to reduce the risk of harvesting stolen credentials.
- Educate your users about phishing campaigns. GoPhish is a great open source tool to measure phishing exposure within an organization.


