- Your password manager is under attack, and this new threat makes it worse: How to defend yourself
- EcoFlow's new backyard solar energy system starts at $599 - no installation crews or permits needed
- “현업에 스며들기, 생성형 AI로 가능했다” 지멘스 모빌리티의 IT 혁신 사례
- 휴먼컨설팅그룹, HR 솔루션 '휴넬' 업그레이드 발표
- Epicor expands AI offerings, launches new green initiative
Microsoft’s August 2023 Patch Tuesday Addresses 73 CVEs (CVE-2023-38180)

Microsoft addresses 73 CVEs, including one vulnerability exploited in the wild.
- 6Critical
- 67Important
- 0Moderate
- 0Low
Microsoft patched 73 CVEs in its August Patch Tuesday release, with six rated as critical and 67 rated as important. Microsoft also released two advisories (ADV230003 and ADV230004) this month as well as a patch for a vulnerability in AMD processors (CVE-2023-20569). These were omitted from our totals.
This month’s update includes patches for:
- .NET Core
- .NET Framework
- ASP.NET
- ASP.NET and Visual Studio
- Azure Arc
- Azure DevOps
- Azure HDInsights
- Dynamics Business Central Control
- Memory Integrity System Readiness Scan Tool
- Microsoft Dynamics
- Microsoft Exchange Server
- Microsoft Office
- Microsoft Office Excel
- Microsoft Office Outlook
- Microsoft Office SharePoint
- Microsoft Office Visio
- Microsoft Teams
- Microsoft WDAC OLE DB provider for SQL
- Microsoft Windows Codecs Library
- Reliability Analysis Metrics Calculation Engine
- Role: Windows Hyper-V
- SQL Server
- Tablet Windows User Interface
- Windows Bluetooth A2DP driver
- Windows Cloud Files Mini Filter Driver
- Windows Common Log File System Driver
- Windows Cryptographic Services
- Windows Defender
- Windows Fax and Scan Service
- Windows Group Policy
- Windows HTML Platform
- Windows Kernel
- Windows LDAP – Lightweight Directory Access Protocol
- Windows Message Queuing
- Windows Mobile Device Management
- Windows Projected File System
- Windows Reliability Analysis Metrics Calculation Engine
- Windows Smart Card
- Windows System Assessment Tool
- Windows Wireless Wide Area Network Service
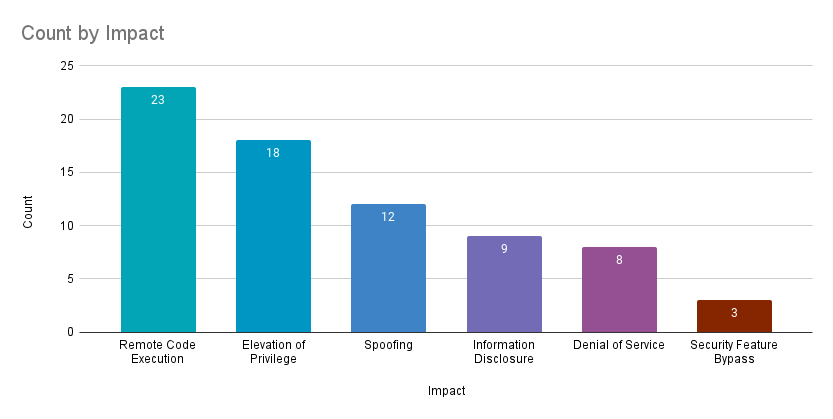
Remote code execution (RCE) vulnerabilities accounted for 31.5% of the vulnerabilities patched this month, followed by elevation of privilege (EoP) vulnerabilities at 24.7%.
CVE-2023-38180 |.NET and Visual Studio Denial of Service Vulnerability
CVE-2023-38180 is a Denial of Service (DoS) vulnerability in Microsoft Visual Studio,.NET versions 6.0 and 7.0, and ASP.NET Core 2.1. It is rated as “Important” and was assigned a CVSSv3 score of 7.5. According to Microsoft, this vulnerability was exploited in the wild as a zero-day. While details of its exploitation were not available at the time this blog post was published, an attacker that exploits this vulnerability would be able to create a DoS condition on a vulnerable server.
CVE-2023-35385, CVE-2023-36910 and CVE-2023-36911 | Microsoft Message Queuing Remote Code Execution Vulnerability
CVE-2023-35385, CVE-2023-36910 and CVE-2023-36911 are RCE vulnerabilities in the Microsoft Message Queuing (MSMQ) component of Windows operating systems that were each given a CVSSv3 score of 9.8 and a rating of critical. Microsoft rated these vulnerabilities as “Exploitation Less Likely” using the Microsoft Exploitability Index.
A remote unauthenticated attacker can exploit this vulnerability by sending malicious MSMQ packets to a vulnerable MSMQ server leading to arbitrary code execution. However, in order to exploit this flaw, the Message Queuing service needs to be enabled on the vulnerable server. Microsoft says if the service is enabled, it runs under the service name “Message Queuing” and is listening on TCP port 1801. Tenable customers can utilize Plugin ID 174933 to identify systems that have this service running.
Yuki Chen, a security researcher with Cyber KunLun, is credited with discovering a total of six vulnerabilities in Microsoft Message Queuing in August 2023, including the three above as well as two DoS vulnerabilities (CVE-2023-36912 and CVE-2023-38172) and CVE-2023-35383, an information disclosure vulnerability.
CVE-2023-21709 | Microsoft Exchange Server Elevation of Privilege Vulnerability
CVE-2023-21709 is an EoP vulnerability in Microsoft Exchange Server. It was assigned a CVSSv3 score of 9.8 and is rated as Exploitation Less Likely. An unauthenticated attacker could exploit this vulnerability by attempting to brute force the password for valid user accounts. Successful exploitation would allow an attacker to “login as another user.”
According to the advisory, additional steps are required in order to address this vulnerability. After applying the patch, a PowerShell script must be run. We recommend reviewing the advisory for the latest information from Microsoft to successfully remediate this vulnerability.
This is the third EoP vulnerability in Microsoft Exchange Server disclosed in 2023. The first two were disclosed as part of the January 2023 Patch Tuesday release (CVE-2023-21763, CVE-2023-21764).
CVE-2023-38181, CVE-2023-38185, CVE-2023-35368, CVE-2023-38182, CVE-2023-35388 | Additional Microsoft Exchange Server Vulnerabilities
In addition to CVE-2023-21709, Microsoft patched five other vulnerabilities in Microsoft Exchange Server:
| CVE | Title | CVSSv3 | Exploitability |
|---|---|---|---|
| CVE-2023-38181 | Microsoft Exchange Server Spoofing Vulnerability | 8.8 | Exploitation Less Likely |
| CVE-2023-38185 | Microsoft Exchange Server Remote Code Execution Vulnerability | 8.8 | Exploitation Less Likely |
| CVE-2023-35368 | Microsoft Exchange Server Remote Code Execution Vulnerability | 8.8 | Exploitation Less Likely |
| CVE-2023-38182 | Microsoft Exchange Server Remote Code Execution Vulnerability | 8.0 | Exploitation More Likely |
| CVE-2023-35388 | Microsoft Exchange Server Remote Code Execution Vulnerability | 8.0 | Exploitation More Likely |
Of the five other vulnerabilities patched this month, two (CVE-2023-38182, CVE-2023-35388) are rated as “Exploitation More Likely.” According to the advisories, exploitation of these vulnerabilities would allow an authenticated attacker to execute code using a PowerShell remoting session. In order to successfully exploit this flaw, the attacker would first need to have LAN access and valid credentials for an Exchange user.
As Microsoft Exchange Server is a popular target for attackers, organizations that use Exchange Server should apply these patches as soon as possible.
CVE-2023-35359, CVE-2023-35380, CVE-2023-35382, CVE-2023-35386 and CVE-2023-38154 | Windows Kernel Elevation of Privilege Vulnerability
CVE-2023-35359, CVE-2023-35380, CVE-2023-35382, CVE-2023-35386, and CVE-2023-38154 are EoP vulnerabilities in the Windows Kernel. All five vulnerabilities were assigned a CVSSv3 score of 7.8 and four are rated as “Exploitation More Likely,” with CVE-2023-38154 rated as “Exploitation Unlikely.” A local, authenticated attacker could exploit this vulnerability to obtain SYSTEM privileges. Four of the five vulnerabilities are attributed to researchers from Google Project Zero.
In 2023, including these five vulnerabilities, 33 EoP flaws were discovered in the Windows Kernel.
CVE-2023-36900 | Windows Common Log File System Driver Elevation of Privilege Vulnerability
CVE-2023-36900 is an EoP vulnerability in the Windows Common Log File System (CLFS) Driver. It was assigned a CVSSv3 score of 7.8 and is rated as “Exploitation More Likely.” An authenticated attacker could exploit this vulnerability to gain SYSTEM privileges.
This is the fifth EoP vulnerability discovered in the Windows CLFS Driver in 2023, two of which were exploited in the wild as zero-days (CVE-2023-23376, CVE-2023-28252).
ADV230003 | Microsoft Office Defense in Depth Update
Microsoft released security advisory ADV230003 as part of its August Patch Tuesday release to provide “enhanced security as a defense in depth measure.” This update is in response to the discovery of CVE-2023-36884, a security feature bypass vulnerability (previously categorized as RCE by Microsoft) affecting Windows and Windows Server installations that was disclosed as part of the July 2023 Patch Tuesday release. While ADV230003 does not directly address CVE-2023-36884, it was included as part of this month’s release as it “stops the attack chain” that leads to CVE-2023-36884. Organizations are encouraged to apply the Office updates listed in the advisory and apply the latest Windows updates for August.
Microsoft also updated its advisory page for CVE-2023-36884 as part of its August Patch Tuesday, including updating the title to a “Security Feature Bypass” in Windows Search, while the CVSSv3 score was reduced to 7.5 and the severity decreased from Critical to Important. Microsoft provided patching information to address the vulnerability.
Tenable Solutions
Users can create scans that focus specifically on our Patch Tuesday plugins. From a new advanced scan, in the plugins tab, set an advanced filter for Plugin Name contains August 2023.
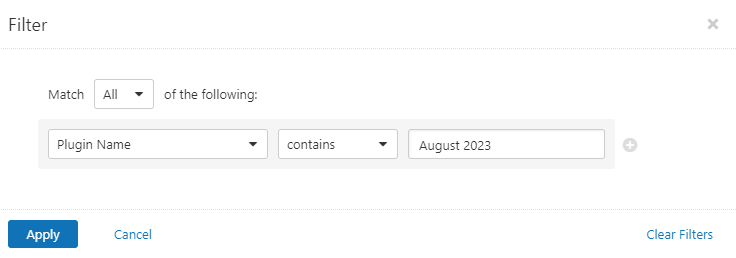
With that filter set, click the plugin families to the left and enable each plugin that appears on the right side. Note: If your families on the left say Enabled, then all the plugins in that family are set. Disable the whole family before selecting the individual plugins for this scan. Here’s an example from Tenable Vulnerability Management (formerly Tenable.io):
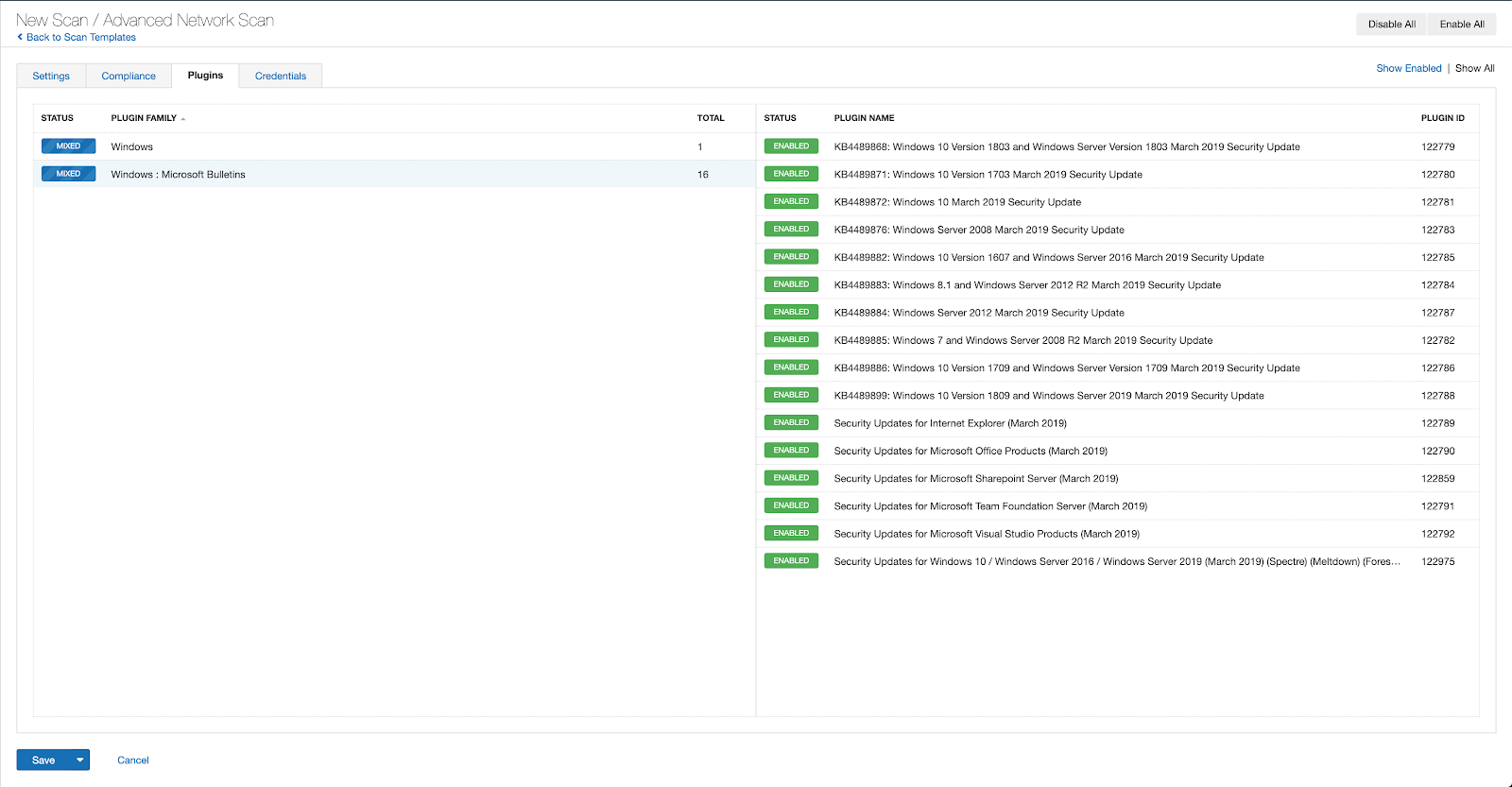
A list of all the plugins released for Tenable’s August 2023 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
Get more information
Join Tenable’s Security Response Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.

