- I found the best AirTag wallet alternative that also works with Android - and it's priced well
- The Rising Tide: Understanding the Surge in Cyber Attacks in India
- Yes, your internet provider can throttle your speed. Here's how to stop it (or at least try to)
- Half of Firms Suffer Two Supply Chain Incidents in Past Year
- Data strategy e qualità del dato: come gettare le basi per implementare l’AI
Microsoft’s January 2024 Patch Tuesday Addresses 48 CVEs (CVE-2024-20674)

- 2Critical
- 46Important
- 0Moderate
- 0Low
Microsoft addresses 48 CVEs in its January 2024 Patch Tuesday release with no zero-day or publicly disclosed vulnerabilities.
Microsoft patched 48 CVEs in its January 2024 Patch Tuesday release, with two rated critical and 46 rated as important. Our counts omitted CVE-2022-35737, a vulnerability in SQLite called “Stranger Strings” that was assigned by MITRE and patched in July 2022. For the second straight month, Microsoft did not patch any zero-day vulnerabilities that were exploited or publicly disclosed.
This month’s update includes patches for:
- .NET and Visual Studio
- .NET Core & Visual Studio
- .NET Framework
- Azure Storage Mover
- Microsoft Bluetooth Driver
- Microsoft Devices
- Microsoft Identity Services
- Microsoft Office
- Microsoft Office SharePoint
- Microsoft Virtual Hard Drive
- Remote Desktop Client
- SQL Server
- Unified Extensible Firmware Interface
- Visual Studio
- Windows AllJoyn API
- Windows Authentication Methods
- Windows BitLocker
- Windows Cloud Files Mini Filter Driver
- Windows Collaborative Translation Framework
- Windows Common Log File System Driver
- Windows Cryptographic Services
- Windows Group Policy
- Windows Hyper-V
- Windows Kernel
- Windows Kernel-Mode Drivers
- Windows Libarchive
- Windows Local Security Authority Subsystem Service (LSASS)
- Windows Message Queuing
- Windows Nearby Sharing
- Windows ODBC Driver
- Windows Online Certificate Status Protocol (OCSP) SnapIn
- Windows Scripting
- Windows Server Key Distribution Service
- Windows Subsystem for Linux
- Windows TCP/IP
- Windows Themes
- Windows Win32 Kernel Subsystem
- Windows Win32K
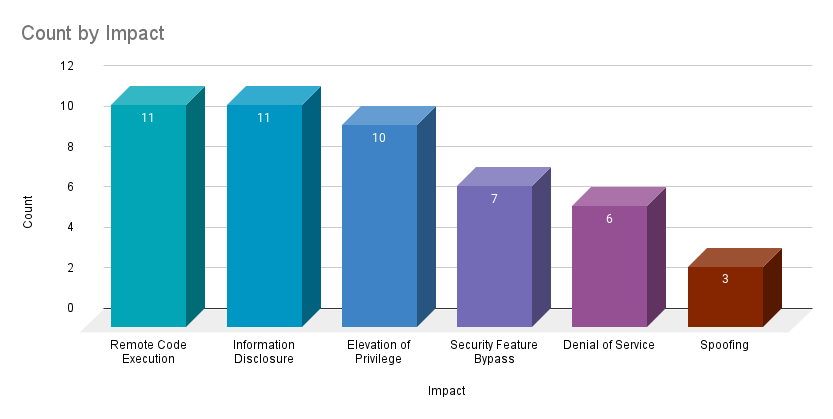
Remote code execution (RCE) and information disclosure vulnerabilities both accounted for 22.9% of the vulnerabilities patched this month, followed by elevation of privilege (EoP) vulnerabilities at 20.8%.
CVE-2024-20674 | Windows Kerberos Security Feature Bypass Vulnerability
CVE-2024-20674 is a critical security feature bypass vulnerability affecting Windows Kerberos, an authentication protocol designed to verify user or host identities. It was assigned a CVSSv3 score of 9.0 and is rated as “Exploitation More Likely” according to the Microsoft Exploitability Index.
To exploit this vulnerability, an attacker needs to have established access to a target network. From there, the attacker would attempt to spoof itself as a Kerberos authentication server by conducting a machine-in-the-middle (MITM) attack or by some other local network spoofing method and sending a malicious Kerberos message to a client machine. The attacker would then be able to bypass authentication via impersonation.
CVE-2024-20683 and CVE-2024-20686 | Win32k Elevation of Privilege Vulnerability
CVE-2024-20683 and CVE-2024-20686 are EoP vulnerabilities in Microsoft’s Win32k, a core kernel-side driver used in Windows. Both vulnerabilities received CVSSv3 scores of 7.8 and are rated “Exploitation More Likely.” Successful exploitation could allow an attacker to gain SYSTEM privileges on an affected host. EoP vulnerabilities are often abused by malicious actors after gaining initial access to a system and in 2023, 14 EoP vulnerabilities in Win32k were patched by Microsoft. While neither of these two vulnerabilities has been reported as exploited in the wild by Microsoft, one of the 14 patched in 2023 was exploited as a zero-day, CVE-2023-29336, which was patched in the May 2023 Patch Tuesday release.
CVE-2024-21318 | Microsoft SharePoint Server Remote Code Execution Vulnerability
CVE-2024-21318 is a RCE vulnerability affecting Microsoft SharePoint Server. With a CVSSv3 score of 8.8, this flaw can be exploited by an authenticated attacker with at least Site Owner privileges. While no active exploitation has been observed at the time the vulnerability was patched, Microsoft rates this vulnerability as “Exploitation More Likely.”
CVE-2024-21318 is credited to multiple researchers at STAR Labs, who in September, published a blog post outlining the successful chaining of two vulnerabilities affecting Microsoft SharePoint Server. The exploit chain consisted of an EoP vulnerability CVE-2023-29357 and a RCE vulnerability, CVE-2023-24955. While a proof-of-concept was released, it was not weaponizable as designed, and required additional work to achieve RCE. While that vulnerability chain does not appear to have been abused, we strongly recommend patching SharePoint servers as soon as possible. As demonstrated by the STAR Labs exploit chain, attackers seek out unpatched vulnerabilities as part of their attempts to exploit networks. Timely patching is a crucial defense step in securing your organization.
CVE-2024-21310 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability
CVE-2024-21310 is an EoP vulnerability in the Microsoft Windows Cloud Files Mini Filter Driver (cldflt.sys). It was assigned a CVSSv3 score of 7.8 and is rated as important and “Exploitation More Likely.” An attacker could exploit this vulnerability as part of post-compromise activity to elevate privileges to SYSTEM.
This is the third month in a row that Microsoft patched an EoP in the Microsoft Cloud Files Mini Filter Driver. In 2023, Microsoft patched six EoP vulnerabilities in the Cloud Files Mini Filter Driver, including CVE-2023-36036, which was the first to be exploited in the wild as a zero-day.
CVE-2024-20653 | Microsoft Common Log File System Elevation of Privilege Vulnerability
CVE-2024-20653 is an EoP vulnerability in the Microsoft Common Log File System (CLFS). It was assigned a CVSSv3 score of 7.8 and is rated as important and “Exploitation More Likely.” An attacker could exploit this vulnerability as part of post-compromise activity to elevate privileges to SYSTEM.
This is the 23rd EoP vulnerability in the Microsoft CLFS patched since 2022, with 10 patched in 2023 and 12 patched in 2022.
CVE-2024-20698 | Windows Kernel Elevation of Privilege Vulnerability
CVE-2024-20698 is an EoP vulnerability in the Microsoft Windows Kernel. It was assigned a CVSSv3 score of 7.8 and is rated as important and “Exploitation More Likely.” An attacker could exploit this vulnerability as part of post-compromise activity to elevate privileges to SYSTEM.
This is the 64th EoP vulnerability in the Microsoft Windows Kernel patched since 2022, with 43 patched in 2023 and 20 patched in 2022.
Tenable Solutions
A list of all the plugins released for Tenable’s January 2024 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
For more specific guidance on best practices for vulnerability assessments, please refer to our blog post on How to Perform Efficient Vulnerability Assessments with Tenable.
Get more information
Join Tenable’s Security Response Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.

