- How to use ChatGPT to write code - and my top trick for debugging what it generates
- The Samsung Galaxy Ring comes with a free $100 gift card - here's where to get it
- My favorite DeWalt cordless power tool set is 43% off right now
- My favorite MagSafe wallet stand is the ideal iPhone companion, and it just got cheaper
- Sam Altman says the Singularity is imminent - here's why
Microsoft’s June 2025 Patch Tuesday Addresses 65 CVEs (CVE-2025-33053)

- 9Critical
- 56Important
- 0Moderate
- 0Low
Microsoft addresses 65 CVEs, including two zero-day vulnerabilities, with one being exploited in the wild.
Microsoft addresses 65 CVEs in its June 2025 Patch Tuesday release, with nine rated critical, and 56 rated as important. Our counts omitted one vulnerability reported by CERT CC.
This month’s update includes patches for:
- .NET and Visual Studio
- App Control for Business (WDAC)
- Microsoft AutoUpdate (MAU)
- Microsoft Local Security Authority Server (lsasrv)
- Microsoft Office
- Microsoft Office Excel
- Microsoft Office Outlook
- Microsoft Office PowerPoint
- Microsoft Office SharePoint
- Microsoft Office Word
- Nuance Digital Engagement Platform
- Power Automate
- Remote Desktop Client
- Visual Studio
- WebDAV
- Windows Common Log File System Driver
- Windows Cryptographic Services
- Windows DHCP Server
- Windows DWM Core Library
- Windows Hello
- Windows Installer
- Windows KDC Proxy Service (KPSSVC)
- Windows Kernel
- Windows Local Security Authority (LSA)
- Windows Local Security Authority Subsystem Service (LSASS)
- Windows Media
- Windows Netlogon
- Windows Recovery Driver
- Windows Remote Access Connection Manager
- Windows Remote Desktop Services
- Windows Routing and Remote Access Service (RRAS)
- Windows SDK
- Windows SMB
- Windows Security App
- Windows Shell
- Windows Standards-Based Storage Management Service
- Windows Storage Management Provider
- Windows Storage Port Driver
- Windows Win32K GRFX
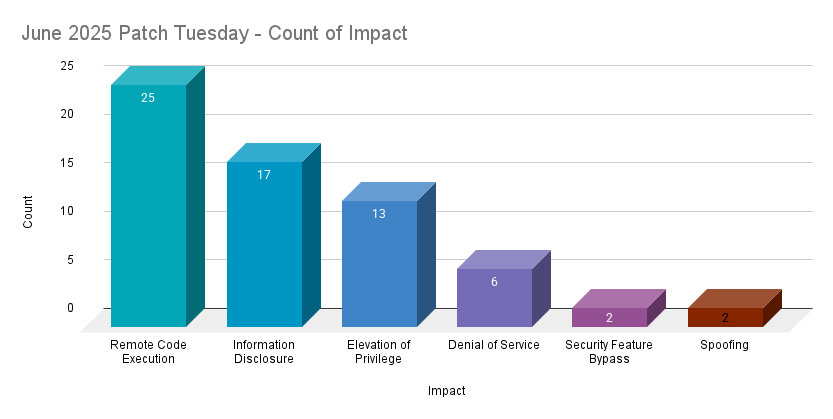
Remote code execution (RCE) vulnerabilities accounted for 38.5% of the vulnerabilities patched this month, followed by information disclosure vulnerabilities at 26.2%.
CVE-2025-33053 | Web Distributed Authoring and Versioning (WebDAV) Remote Code Execution Vulnerability
CVE-2025-33053 is a RCE in Web Distributed Authoring and Versioning (WebDAV). It was assigned a CVSSv3 score of 8.8 and is rated important. An attacker could exploit this vulnerability through social engineering, by convincing a target to open a malicious URL or file. Successful exploitation would give the attacker the ability to execute code on the victim’s network.
According to Microsoft, it was exploited in the wild as a zero-day. It was reported by researchers at Check Point Research, who have released a blog post discussing the discovery of this zero-day. According to the researchers, CVE-2025-33053 was exploited by Stealth Falcon, an APT group that has been observed using zero-day exploits in espionage attacks.
CVE-2025-33073 | Windows SMB Client Elevation of Privilege Vulnerability
CVE-2025-33073 is an EoP vulnerability affecting the Windows Server Message Block (SMB) client. It was assigned a CVSSv3 score of 8.8 and was publicly disclosed prior to a patch being made available. According to Microsoft, successful exploitation requires an attacker to execute a crafted script to force a target device to connect to an attacker-controlled machine using SMB credentials. If successful, the attacker could elevate their privileges to SYSTEM.
CVE-2025-33070 | Windows Netlogon Elevation of Privilege Vulnerability
CVE-2025-33070 is an EoP vulnerability in Windows Netlogon. It was assigned a CVSSv3 score of 8.1 and is rated as critical. An attacker could exploit this vulnerability to gain domain administrator privileges. According to Microsoft, a successful attack requires the attacker to take additional actions in order to prepare a target for exploitation. Despite these requirements, Microsoft has assessed this vulnerability as “Exploitation More Likely” according to Microsoft’s Exploitability Index.
CVE-2025-47162, CVE-2025-47164, CVE-2025-47167 and CVE-2025-47953 | Microsoft Office Remote Code Execution Vulnerability
CVE-2025-47162, CVE-2025-47164, CVE-2025-47167 and CVE-2025-47953 are RCE vulnerabilities affecting Microsoft Office. Each of these critical vulnerabilities were assigned CVSSv3 scores of 8.4 and all except CVE-2025-47953 were assessed as “Exploitation More Likely.” Microsoft notes that Preview Pane is an attack vector for exploitation of these vulnerabilities.
In addition, CVE-2025-47173, another RCE in Microsoft Office was patched this month. It received a CVSSv3 score of 7.8, was rated as important and assessed as “Exploitation Unlikely.” Unlike the other Office vulnerabilities, the preview pane is not an attack vector for CVE-2025-47173.
CVE-2025-33071 | Windows KDC Proxy Service (KPSSVC) Remote Code Execution Vulnerability
CVE-2025-33071 is a RCE vulnerability affecting Windows Kerberos Key Distribution Center (KDC) proxy service, an authentication mechanism used for KDC servers over HTTPS. It received a CVSSv3 score of 8.1 and is rated as critical. An unauthenticated attacker could exploit this vulnerability utilizing a crafted application to exploit a cryptographic protocol vulnerability in order to execute arbitrary code. According to the advisory, this only impacts Windows Servers that have been “configured as a [MS-KKDCP]: Kerberos Key Distribution Center (KDC) Proxy Protocol server.” While the advisory does mention that exploitation requires the attacker to win a race condition, this vulnerability was still assessed as “Exploitation More Likely.”
CVE-2025-32713 | Windows Common Log File System Driver Elevation of Privilege Vulnerability
CVE-2025-32713 is an EoP vulnerability in the Windows Common Log File System (CLFS) Driver. It was assigned a CVSSv3 score of 7.8 and is rated as important. CVE-2025-32713 was assessed as “Exploitation More Likely.” Successful exploitation would allow an attacker to elevate their privileges to SYSTEM.
Prior to this month’s release, Microsoft has patched five other EoP vulnerabilities in the Windows CLFS driver in 2025, three of which were exploited as zero-days. This includes CVE-2025-29824 from the April 2025 Patch Tuesday release and both CVE-2025-32701 and CVE-2025-32706, which were patched in the May 2025 Patch Tuesday release.
Tenable Solutions
A list of all the plugins released for Microsoft’s June 2025 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
For more specific guidance on best practices for vulnerability assessments, please refer to our blog post on How to Perform Efficient Vulnerability Assessments with Tenable.
Get more information
Join Tenable’s Research Special Operations (RSO) Team on the Tenable Community.
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.

