- Your Apple CarPlay is getting a big update: 3 useful features coming with iOS 26
- I changed 8 settings on my Motorola phone for an instant battery boost
- Your car's USB port is more useful than you think. 5 features you're missing out on
- Anubis Ransomware Adds File-Wiping Capability
- Liderar en la era de los algoritmos: un desafío para el CIO actual
Microsoft’s new security tool will discover firmware vulnerabilities, and more, in PCs and IoT devices

Devices have multiple OSs and firmware running, and most organisations don’t know what they have or if it’s secure. Microsoft will use ReFirm to make it easier to find out without being an expert.
ReFirm fits in with Azure services to scan and update IoT devices.
Image: Microsoft
As operating systems become more secure, attackers are increasingly shifting their attention to firmware, which is less visible, more fundamental and rarely well protected.
Vulnerabilities in firmware are a steadily growing percentage of the new issues added to the NIST National Vulnerability Database: five times as many attacks are happening as only four years ago. Many organizations are experiencing attacks on firmware (83% in a recent Microsoft survey, and that’s only the organisations that know they’ve been attacked), but protecting firmware gets only a small share of the security budget.
SEE: Hardware inventory policy (TechRepublic Premium)
Part of the problem is the lack of usable tools for scanning to see what firmware is in use across your network and what vulnerabilities are present. There is a lot of poorly written and reused code in firmware, and few devices ship with a software ‘bill of materials’ to tell you what’s inside the case. If you do spot an issue, updating firmware is a fragmented and low-level process, and there are no ways to apply vulnerability mitigations below the OS layer.
All that is why Microsoft is buying ReFirm Labs, home of the open-source Binwalk tool, whose Centrifuge firmware platform automates the process of running static analysis to discover what firmware vulnerabilities you’re already exposed to.
“The basic security tools you have in the desktop world, that would be their bread-and-butter for the CISO, just aren’t there for IoT,” partner director of enterprise and OS security at Microsoft, David Weston, told TechRepublic. “There’s no way we’re going to get 50 billion devices connected to the cloud and move out of this air-gapped operational technology world to the AI-connected cloud world without solving these basic problems.”
“It’s very difficult for me to say Windows is secure or Linux is secure without saying the firmware is secure, and it’s the place with the least attention. It’s the most privileged code on the platform, it can even modify the hypervisor, it is the least looked-at and the least updatable. It’s invisible to most security technology today.”

Centrifuge, also known as Binwalk Enterprise, automates firmwre scans to help you understand the state of IoT devices.
Image: Microsoft
In fact, most security technology depends on firmware to securely store credentials; if the firmware is compromised, so is the endpoint protection tool. “I pay people to be the most efficient attackers possible,” Weston noted (one of his roles is running a red team to attack Windows). “And nine times out of 10, they’re going to pick a firmware vector.”
Firmware is a potential security issue on PCs, servers, IoT devices, network routers and a lot of other equipment. “Every modern computing device is usually composed of six to seven — if not more on a server — different operating systems, one of which we have visibility into. Take a Surface laptop: you’ve got a Wi-Fi chip in there, running something like ThreadX, a real-time operating system that [Microsoft] bought [in 2019], you’ve got an SSD, with a separate embedded controller with a separate version of Linux: what’s in that SSD?”
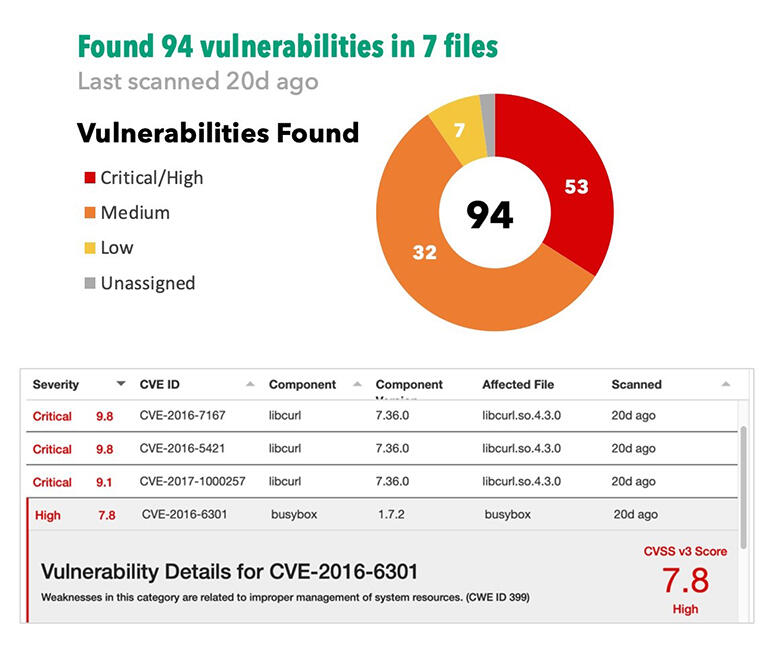
Binwalk shows which firmware on your devices has known vulnerabilities.
Image: Microsoft
Some IoT devices are well designed with good security options like secure boot and address space layout randomisation; others have open ports and absurdly vulnerable default passwords. “They could have done a great job or it could be terrible; you just can’t know,” Weston warned. “Just the ability to determine what good is and bad is, is a fundamental thing we need.”
An experienced security researcher like Weston can use tools like BinWalk to investigate, but even getting to the point where you can perform static analysis to look for vulnerabilities in firmware has been a manual process involving a lot of scripting and unpacking that ReFirm makes faster and simpler.
“I have an IoT lab. I can always reverse this stuff, but who has time for that? And I have the luxury of being my own security engineer; how about everyone else? With ReFirm, in 10 minutes I was able to take a whole bunch of different laptops in my house and get a perspective, and my mind was blown. I was finding serious security issues that freaked me out.”
The strength of ReFirm isn’t just the quality of scanning and static analysis; it’s that it’s designed to be usable.
“It’s drag and drop. You go to your router manufacturer’s website, you download the firmware flash file, you drag it over and you get a pentest report of impressive quality from an automation tool. It spits out a PDF that says ‘you have these CVEs, here are the configuration issues, and here’s how far it is off of very common compliance and certification regimes’. It’s really useful, and it will get better by taking technologies that Microsoft already has across the company, and starting to integrate them into this platform.”
This simplicity is key to helping organisations get a handle on firmware threats, Weston suggested.
“The security community is always focused on what’s cool and what’s next, and the actual enterprise security community is struggling with the basics,” Weston pointed out. “They’re looking at me to make things easy. It’s not so much about adding new capabilities, although they want that too: it’s about taking things that are hard today and making them easier so that folks get time back to spend on more strategic issues.”
Getting visibility
Microsoft’s CEO Satya Nadella is fond of predicting that there will be 50 billion connected devices by 2030; that’s a lot of potential vulnerabilities in critical systems that today’s security software doesn’t usually address.
“A tiny fraction of those will be things that are capable to be analysed by current tools, and something like ReFirm can grow to do everything else,” Weston says. “These are appliance-like devices where you can’t just instal a vulnerability analysis package, or even log into it. You’ve got to have alternative means, and this kind of static analysis of firmware makes a tonne of sense.”
It fits well alongside the CyberX asset discovery tool Microsoft acquired that’s now part of Azure Defender for IoT, which finds what devices are connected and what protocols they use. Simple as that sounds, it’s rare for organisations to know that.
“The first thing it tells you is the most important thing in security, which is what is on my network? Don’t underestimate how hard that is in your average enterprise network,” Weston pointed out. “Just knowing ‘oh, my elevator is talking SNMP in the clear’ — that’s something that is difficult for most companies to catalogue.”
That gives you a baseline so you know when unusual behaviour is happening that might mean you’re under attack. “If some weird-looking Modbus protocol starts to shoot across your network that wasn’t there before, you could be looking at a piece of ransomware.”
What ReFirm adds is knowing whether you should be comfortable with the devices CyberX discovers being connected to your network, says Weston. “Should I have plugged in any of these devices to begin with? If they have OpenSSH to root with password 123, as good as CyberX is, you just shouldn’t have that on your network.”
Microsoft’s ReFirm plans
Today, ReFirm needs you to provide the firmware files, but Microsoft plans to create a database of device information, Weston says. “You plug in CyberX and it discovers the devices, it monitors them and it asks ReFirm ‘do you know anything about IoT device X or Y’. Hopefully we’ve pre-scanned most of those devices and we can propagate the information — and for anything we don’t have, there’s the drag-and-drop interface to do a custom analysis.”
Having that visibility of what’s on your network and whether it’s safe to have on your network is a good first step. The Azure Device Updates service can already push IoT firmware updates out through Windows Update. Microsoft’s bigger vision is to create a service based on Windows Update that can handle a much wider range of third-party devices, says Weston.
“We’re going to take Windows Update, which people already at least know and trust on Patch Tuesdays, and we want to push the IoT and edge devices into that model. Microsoft’s update system is a pretty known commodity — just about every government regulator out there looked at it in one form or another — and so we feel good about being able to move customers towards it.”
Smaller manufacturers usually don’t have the expertise to build and secure their own update mechanisms, Weston pointed out. “And I don’t think customers want them to, because it’s not going to have [options like] ‘I only want this at 2am, I only want to stage this level of criticality’. They already have a process set up for that. They have Qualys and Nessus on the desktop, but they don’t have the equivalent for IoT. What I think ReFirm is going to allow enterprises to do is fill that gap, and then allow folks to use Azure Device Update to schedule that.”
SEE: The future of work: Tools and strategies for the digital workplace (free PDF) (TechRepublic)
ReFirm will be useful even with hardware security for firmware, like Secured-core devices. As well as being available on PCs and servers, Secured-core is available as a certification for IoT devices, which have to have the Azure Defender for IoT agent installed and do log collection, telemetry and device updates.
In the future, Weston would like to see ReFirm become part of the certification. “To not only make sure that you’re shipping the device secure, but that it’s being scanned regularly by this ReFirm firmware technology and you’re keeping the firmware up to date.”
Despite the name, ReFirm might not stay restricted to firmware. Microsoft has static and dynamic analysis tools it can add to the product, which Weston compared to VirusTotal‘s frequent updates with new analysis options. “I can keep putting layers of tools in that analysis pipeline. I think this has the opportunity to be a VirusTotal-like product that, rather than looking for malware, is looking for vulnerabilities in an arbitrary object. We’re focused on firmware because that seems like the right application, but it could be VM snapshots or many, many other things.”
There’s good news for fans of the open-source Binwalk tool, too. Microsoft will be investing heavily in that, because it’s already widely used by multiple teams across the company who have feature requests, says Weston: “I think we probably have a few years’ worth of backlog ideas already!”


