- This video doorbell camera has just as many features are my Ring - and no subscription required
- LG is giving away free 27-inch gaming monitors, but this is the last day to grab one
- I tested this Eufy security camera and can't go back to grainy night vision
- I replaced my iPhone with a premium dumbphone - here's my verdict after a month
- Build your toolkit with the 10 DIY gadgets every dad should have
Microsoft’s November 2023 Patch Tuesday Addresses 57 CVEs (CVE-2023-36025)

Microsoft addresses 57 CVEs, including three zero-day vulnerabilities that were exploited in the wild.
- 3Critical
- 54Important
- 0Moderate
- 0Low
Microsoft patched 57 CVEs in its November 2023 Patch Tuesday release, with three rated critical and 54 rated important. We omitted one vulnerability from our counts this month, CVE-2023-24023, a Bluetooth Vulnerability as this flaw was reported through MITRE.
This month’s update includes patches for:
- .NET Framework
- ASP.NET
- Azure
- Azure DevOps
- Microsoft Bluetooth Driver
- Microsoft Dynamics
- Microsoft Dynamics 365 Sales
- Microsoft Exchange Server
- Microsoft Office
- Microsoft Office Excel
- Microsoft Office SharePoint
- Microsoft Remote Registry Service
- Microsoft WDAC OLE DB provider for SQL
- Microsoft Windows Search Component
- Microsoft Windows Speech
- Open Management Infrastructure
- Tablet Windows User Interface
- Visual Studio
- Visual Studio Code
- Windows Authentication Methods
- Windows Cloud Files Mini Filter Driver
- Windows Common Log File System Driver
- Windows Compressed Folder
- Windows Defender
- Windows Deployment Services
- Windows DHCP Server
- Windows Distributed File System (DFS)
- Windows DWM Core Library
- Windows HMAC Key Derivation
- Windows Hyper-V
- Windows Installer
- Windows Internet Connection Sharing (ICS)
- Windows Kernel
- Windows NTFS
- Windows Protected EAP (PEAP)
- Windows Scripting
- Windows SmartScreen
- Windows Storage
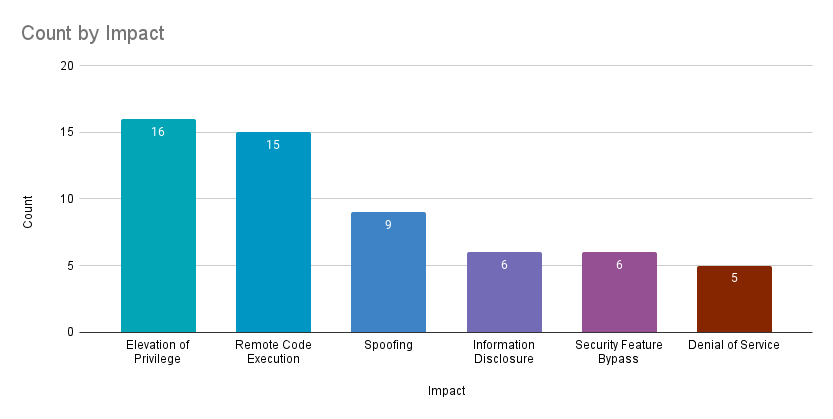
Elevation of privilege (EoP) vulnerabilities accounted for 28.1% of the vulnerabilities patched this month, followed by remote code execution (RCE) vulnerabilities at 26.3%.
CVE-2023-36025 | Windows SmartScreen Security Feature Bypass Vulnerability
CVE-2023-36025 is a security feature bypass vulnerability in Windows SmartScreen. It was assigned a CVSSv3 score of 8.8 and is rated important. According to Microsoft, it was exploited in the wild as a zero-day. An attacker could exploit this flaw by crafting a malicious Internet Shortcut (.URL) file and convincing a target to click on the file or a hyperlink pointing to a.URL file. Successful exploitation would result in a bypass of the security checks in Windows Defender SmartScreen.
This is the third Windows SmartScreen zero-day vulnerability exploited in the wild in 2023 and the fourth in the last two years:
CVE-2023-36033 | Windows DWM Core Library Elevation of Privilege Vulnerability
CVE-2023-36033 is an EoP vulnerability in the DWM Core Library in Microsoft Windows. It was assigned a CVSSv3 score of 7.8 and is rated as important. Microsoft noted that it was exploited in the wild as a zero-day and was publicly disclosed prior to a patch being available. A local attacker with a presence on a vulnerable system could exploit it to gain SYSTEM privileges. It was disclosed to Microsoft by security researcher Quan Jin of DBAPPSecurity WeBin Lab, who is credited with discovering two other EoP zero-day vulnerabilities in 2023:
| CVE | Description | CVSSv3 | Severity | Patch Tuesday |
|---|---|---|---|---|
| CVE-2023-28252 | Windows Common Log File System Driver Elevation of Privilege Vulnerability | 7.8 | Important | April 2023 |
| CVE-2023-36802 | Microsoft Streaming Service Proxy Elevation of Privilege Vulnerability | 7.8 | Important | September 2023 |
This is the 12th EoP vulnerability patched in the DWM Core Library in the last two years, with 10 patched in 2022 and one patched earlier this year in the January 2023 Patch Tuesday release (CVE-2023-21724). However, this is the first DWM Core Library EoP vulnerability that was exploited in the wild as a zero-day in the last two years.
CVE-2023-36038 | ASP.NET Core Denial of Service Vulnerability
CVE-2023-36038 is a denial of service (DoS) vulnerability in the open-source web application framework, ASP.NET. It was assigned a CVSSv3 score of 8.2 and rated as important. Microsoft rates it as Exploitation Less Likely according to the Microsoft Exploitability Index. An attacker that could successfully exploit this vulnerability could trigger an OutOfMemoryException, resulting in a DoS condition. Microsoft notes that this vulnerability was publicly disclosed, however no in-the-wild exploitation has been observed.
CVE-2023-36036 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability
CVE-2023-36036 is an EoP vulnerability in Microsoft Windows Cloud Files Mini Filter Driver (cldflt.sys). It was assigned a CVSSv3 score of 7.8 and is rated as important. Microsoft says it has been exploited in the wild and is credited to both the Microsoft Threat Intelligence Center (MSTIC) and Microsoft Security Response Center (MSRC). While Microsoft did not provide specific details around this vulnerability, like most EoP flaws, if a local attacker exploits this flaw, they would be able to elevate privileges to SYSTEM.
CVE-2023-36413 | Microsoft Office Security Feature Bypass Vulnerability
CVE-2023-36413 is a security feature bypass vulnerability in Microsoft Office. It was assigned a CVSSv3 score of 6.5 and is rated as important. An attacker could exploit this vulnerability using social engineering tactics to convince a target to open a malicious Microsoft Office file on a vulnerable system. Successful exploitation would result in a bypass of security features of Microsoft Office designed to protect users including Protected View and the file would be opened in editing mode instead of protected mode. Microsoft says details about this flaw have been publicly disclosed prior to a patch being available.
Disclosure of these flaws to Microsoft is credited to security researcher Eduardo Braun Prado and Will Dormann.
CVE-2023-36439 | Microsoft Exchange Server Remote Code Execution Vulnerability
CVE-2023-36439 is an RCE vulnerability in Microsoft Exchange Server. It was assigned a CVSSv3 score of 8.0 and rated as important. An attacker authenticated to a vulnerable Exchange Server as a valid user could exploit this vulnerability to gain RCE as NT AUTHORITYSYSTEM on the backend of the server mailbox. Microsoft rates this vulnerability as Exploitation More Likely. It is one of four vulnerabilities in Microsoft Exchange Server patched in this month’s Patch Tuesday release. With the significant historical exploitation of Microsoft Exchange Server by attackers, we continue to monitor for and highlight flaws in Exchange Server in each Patch Tuesday release.
CVE-2023-36035, CVE-2023-36039, CVE-2023-36050 | Microsoft Exchange Server Spoofing Vulnerability
CVE-2023-36035, CVE-2023-36039 and CVE-2023-36050 are spoofing vulnerabilities in Microsoft Exchange Server. All three vulnerabilities were assigned a CVSSv3 score of 8.0 and are rated as important. An attacker could exploit these flaws by possessing valid credentials for an Exchange user on a vulnerable Exchange Server instance. Exploitation of CVE-2023-36035 and CVE-2023-36039 would allow an attacker to access the Net-NTLMv2 hash of the user account which could be utilized in NTLM Relay attacks against other services.
Tenable Solutions
A list of all the plugins released for Tenable’s November 2023 Patch Tuesday update can be found here. As always, we recommend patching systems as soon as possible and regularly scanning your environment to identify those systems yet to be patched.
For more specific guidance on best practices for vulnerability assessments, please refer to our blog post on How to Perform Efficient Vulnerability Assessments with Tenable.
Get more information
Join Tenable’s Security Response Team on the Tenable Community
Learn more about Tenable One, the Exposure Management Platform for the modern attack surface.

