- Your iPhone is getting these useful features with iOS 19 - including a big one for multitaskers
- LastPass can now monitor employees' rogue reliance on shadow SaaS - including AI tools
- HPE 'morphs' private cloud portfolio with improved virtualization, storage and data protection
- Believe it or not, Microsoft just announced a Linux distribution service - here's why
- How to Stay Compliant with the New HIPAA Security Rule Updates
Mobile App APIs Are Crucial to Businesses – But Are Under-Protected

The State of Mobile Security in 2022” Underscores Both the Importance of Mobile Apps and the Relative Lack of Resources Being Allocated to Runtime App and Data Protection.
By David Stewart, CEO, Approov
Over the last two years, mobile apps have emerged as key tools for businesses to communicate with and serve customers, earn revenue, and enable remote work by employees, and their importance is expected to grow further over the next two years.
A new report from Approov and Osterman Research codifies the growing importance of business apps to organizations. It also illustrates several jarring disconnects between the strategically important role that apps now serve, and the comparatively lower level of focus and resources applied to the cybersecurity practices that are necessary protect those apps against runtime threats vs. cybersecurity resources applied elsewhere in the development cycle.
The findings in “The State of Mobile App Security in 2022” demonstrate that mobile apps are key channels through which businesses serve their customers, and their importance to organizations has tripled in the last two years.
The report also reveals a relative lack of resources being applied to protecting mobile apps and their APIs at runtime.
Michael Sampson, a Senior Analyst with Osterman Research, noted that while enterprise app development and deployment are among an organization’s highest priorities, unfortunately, the runtime security of the app, its API secrets and the user data collected do not receive similarly high prioritization and budget.
“These findings raise serious questions, given that so many recent breaches have highlighted the risk of stolen keys and secrets being exploited by threat actors,” Sampson said.
The report underscores that run-time security threats against mobile apps and APIs evolve and continue to inflict damage on organizations, and that damage cannot be prevented simply through adopting more secure “shift left” development practices. Runtime security threats are different than development threats and urgently require a separate set of security strategies.
Among key findings:
- 75% of companies say mobile apps are now “essential” or “absolutely core” to their success, up from 25% two years ago.
- 75% Would Face Substantial Consequences from a Successful Attack on Their Mobile App: An attack against APIs that rendered a mobile app non-functional would have a significant effect on 45 percent of businesses and a major impact on an additional 30 percent.
- 78% Have Low Confidence in Mitigation Against Specific Threats: Seventy-eight percent of respondents are not highly confident that their organizations have the appropriate level of security defenses and protections in place to protect against specific threats posed by mobile apps.
- Most Organizations Have Poor Visibility into Security Threats Against Mobile Apps:
- 60% lack visibility into credit fraud attempts
- 59 % lack visibility into the creation of fake accounts
- 56% lack visibility into data stolen from PIs by scripts
- 54 % cannot detect the use of stolen API keys being used to mimic genuine requests
- 53% percent lack visibility into credential stuffing attacks
- 51% lack visibility into secrets exposed on mobile platforms,
- 50 % cannot detect access by cloned, fake or tampered apps.
- Third-Party APIs Create Pathways for Threat Actors:
- On average, mobile apps depend on more than 30 third-party APIs, and half of the mobile developers surveyed are still storing API keys in the app code – a massive attack surface for bad actors to exploit.
- 42% of organizations don’t require third-party developers to attest to following required standards, and 38% do not pen test the security of third-party code.
- Runtime Threats Receive Lower Priority and Funding: The report finds that although protecting mobile apps and APIs at runtime is an enduring requirement, spending is still skewed towards “shift-left” efforts.
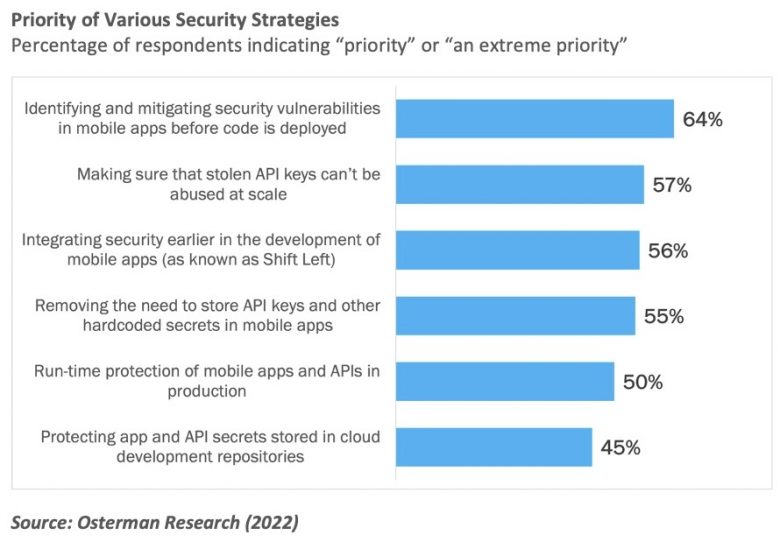
Given that mobile apps and APIs are increasingly the lifeblood of organizations, the practices and resource allocation towards runtime threats must be reconsidered – and quickly – before yet another wave of major mobile app breaches exposes both organizations and their customers to the damage and continual loss that inevitably result.
This research reflects the overarching fact that although mobile apps are an increasingly critical conduit for both commerce and communications, investment in runtime protection of apps and APIs continues to take a back seat. Moreover, poor practices continue unabated, such as the storing of hard-coded keys in a mobile app or device, which exposes app secrets to increasingly clever threat actors.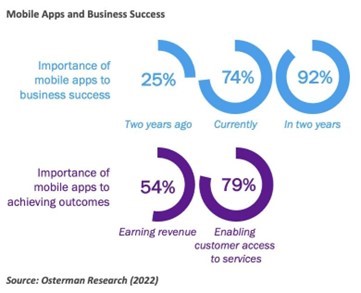
Among the most jarring of disclosures was the admission that speeding time-to-market for new features is more highly prioritized than is security. Fully one half of all respondents reported that for competitive reasons, their organizations might ship apps with known insecurities in order to meet corporate goals. Many also shared that they consider their organization’s security processes for both third-party and in-house developers to be weak and insufficient.
Osterman Research and Approov reached out during Q2:2022 to 302 security directors and mobile application development professionals across the U.S. and U.K. It found that issues affecting mobile app security and mobile app APIs affected organizations of all sizes: forty-eight percent of respondents were from companies of up to 500 employees, 42 percent were in companies of 501 to 4,999 employees, and 10 percent were in companies of more than 5,000 employees.
To download “The State of Mobile App Security in 2022” or view the July 26 webinar with Michael Sampson, visit https://approov.io/for/state-of-mobile-app-security-2022/
About the Author
 David Stewart is CEO of Approov. He has 30+ years’ experience in software security, mobile apps/APIs, embedded software tools, design services, chip design, design automation tools, technical support, marketing, sales, fundraising, executive management & board advisory roles. Current focus is growing a business delivering revenue assurance for enterprises reliant on mobile channels to reach their customers. Approov is a SaaS security solution preventing APIs being accessed by anything other than genuine instances of your mobile apps running in a safe environment. David can be reached at @approov_io and https://approov.io/
David Stewart is CEO of Approov. He has 30+ years’ experience in software security, mobile apps/APIs, embedded software tools, design services, chip design, design automation tools, technical support, marketing, sales, fundraising, executive management & board advisory roles. Current focus is growing a business delivering revenue assurance for enterprises reliant on mobile channels to reach their customers. Approov is a SaaS security solution preventing APIs being accessed by anything other than genuine instances of your mobile apps running in a safe environment. David can be reached at @approov_io and https://approov.io/

