- I ditched my daily driver Bose headphones for the XM6 - and I'm hesitant to go back
- This Lenovo ThinkPad is my top pick for remote work - and it's nearly 50% off now
- I invested in this 3-in-1 robot vacuum, and it's paying off for my home
- I've tested the Meta Ray-Bans for months, and these 5 features still amaze me
- My new favorite iPhone portable charger has a magnetic superpower - and it's cheap
N-Day Exploit Protection Strategies

Risk Management
Over two years, Trend Micro Research scoured the underground forums for insight into the N-day exploit market. Discover their findings and how you can secure your organization against exploits.
Read time: ( words)
The cybercriminal underground is host to a thriving and vast market of zero-day and N-day exploits being sold to malicious actors. Trend Micro Research presents two years of research into the trends of the exploit market, the most prevalent and preferred exploit types, and how to secure against such attacks, enabling security decision makers to enhance their defenses.
N-day exploits overview
An N-day exploit is an exploited vulnerability that has a patch available. This differs from zero-day exploits, which are new and awaiting patches from the compromised vendor. Understandably, newer exploits are more sought after and expensive, but these seemingly “outdated” exploits continue to circulate and grow in popularity. Our research found forum posts mentioning exploits for 20-year-old vulnerabilities and we discovered that older exploits are offered for free or bundled with newer ones.
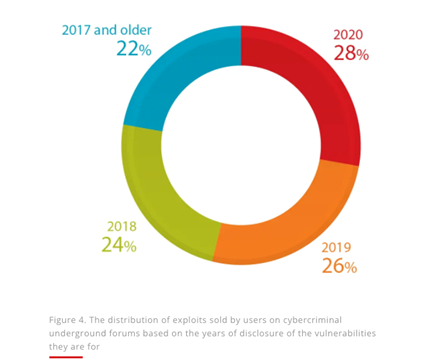
Additionally, old exploits can be just as effective and dangerous as newer ones. You’re most likely familiar with the infamous WannaCry ransomware outbreak of 2017, which used the N-day exploit EternalBlue to attack unpatched computers. Interestingly, 3 years after the first outbreak, WannaCry was still the most detected malware family in our 2020 research, and according to Shodan, more than 650,000 internet-facing devices remain vulnerable to it. EternalBlue was also the driving force behind the NotPetya cyberattacks across the world, which caused more than US$10 billion in damage.
Trends in the exploit market
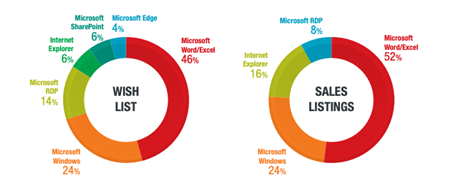
Microsoft remains in-demand
Our research found that exploits for Microsoft had both the highest demand and the highest supply. At least 47% of exploits requested were for Microsoft products, and they accounted for 51% of all sales advertisements.
Exploit subscription services
Like Netflix, but for the bad guys, some cybercriminals offer exploit tools for a monthly fee, enabling malicious actors to launch attacks easily and with painful regularity. One seller even promised that the exploits were “FUD” (fully undetectable). Even more concerning, these subscriptions are often reasonably priced, starting at US$60. While relatively cheap for the threat actors, such exploits can be very costly for organizations.
Exploit subscriptions have also led to the rise of access-as-a-service. These are individuals or groups who use exploits to gain access to a target’s network, and then sell their residence to those looking to launch an attack from within. This new service also increases the number of potential attackers, as customers no longer have to set up complicated infrastructure, and can now easily gain access to a network without being detected.
Next steps
As you look at your strategy for lowering risk and increasing security, we have two words for you: virtual patching. This capability is a great way to shield vulnerabilities from exploit until a patch can be applied, which can often be difficult due to lack of resources and time. While organizations may use a patch prioritization approach for vulnerability management, they also need to factor in the exploits that cybercriminals wish to use and can purchase. Still, this remains an arduous process, and unsurprisingly it takes organizations an average of 69 days to patch a critical vulnerability.
This is where virtual patching comes into play, by implementing layers of security to prevent an exploit from taking advantage of the vulnerability. A cybersecurity solution with virtual patching should include capabilities that inspect ingress and egress traffic and block any suspicious activities. Other than stopping the attack in its tracks, the benefits of virtual patching also include:
- Saves security teams time, allowing developers and programmers to fix flaws in their code while lowering the risk of compromise
- Avoids unnecessary downtime and allows patches to be applied in a structured, regular timeline, mitigating potential revenue loss and risk
- Improves regulatory compliance, helping organization meet timeline requirements imposed by the GDPR, PCI, and many other global regulations
- Provides an additional layer of security, protecting legacy systems and end-of-support operating systems, which are often exposed by N-day exploits
For more of our findings from two years of extensive underground research, read The Rise and Imminent Fall of the N-Day Exploit Market in the Criminal Underground.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk

