- I recommend the Pixel 9 to most people looking to upgrade - especially while it's $250 off
- Google's viral research assistant just got its own app - here's how it can help you
- Sony will give you a free 55-inch 4K TV right now - but this is the last day to qualify
- I've used virtually every Linux distro, but this one has a fresh perspective
- The 7 gadgets I never travel without (and why they make such a big difference)
New Android SpyAgent Campaign Steals Crypto Credentials via Image Recognition | McAfee Blog

Authored by SangRyol Ryu
Recently, McAfee’s Mobile Research Team uncovered a new type of mobile malware that targets mnemonic keys by scanning for images on your device that might contain them. A mnemonic key is essentially a 12-word phrase that helps you recover your cryptocurrency wallets. It’s much simpler to remember than the typical complex “private key” it stands for.
This Android malware cleverly disguises itself as various trustworthy apps, ranging from banking and government services to TV streaming and utilities. However, once installed, these fake apps secretly gather and send your text messages, contacts, and all stored images to remote servers. They often distract users with endless loading screens, unexpected redirects, or brief blank screens to hide their true activities.
McAfee has identified over 280 fake applications involved in this scheme, which have been actively targeting users in Korea since January 2024. Thankfully, McAfee Mobile Security products are already on the lookout for this threat, known as SpyAgent, and are helping to keep your device safe from these deceptive tactics.
Figure 1 Timeline of this campaign
Distribution Mechanism
Mobile malware that targets users in Korea is mainly spread through clever phishing campaigns. These campaigns use text messages or direct messages on social media to send out harmful links. The attackers behind these messages often pretend to be organizations or people you trust, tricking you into clicking on their links. Once clicked, these links take you to fake websites that look incredibly real, mimicking the appearance of legitimate sites. These deceptive sites usually prompt you to download an app, which is how the malware gets installed on your device. Be cautious and always verify the authenticity of any message or link before clicking.
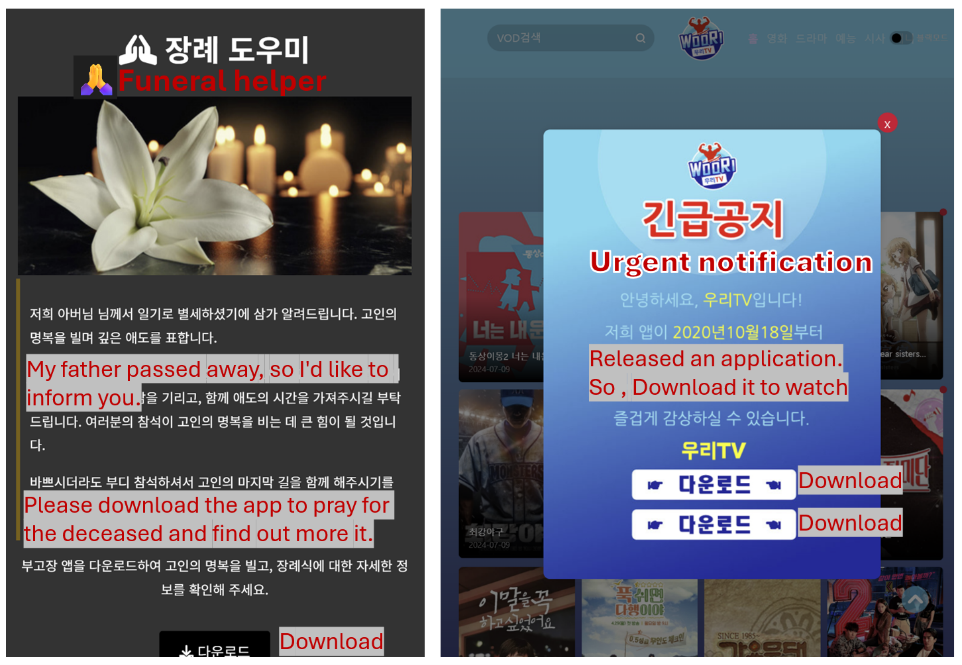
Figure 2 Fake Websites
When a user clicks on the download link, they are prompted to download an APK (Android Package Kit) file. Although this file appears to be a legitimate app, it is actually malicious software. Once the APK is downloaded, the user is asked to install the app. During installation, the app requests permission to access sensitive information such as SMS messages, contacts, and storage, and to run in the background. These permissions are often presented as necessary for the app to function properly, but in reality, they are used to compromise the user’s privacy and security.
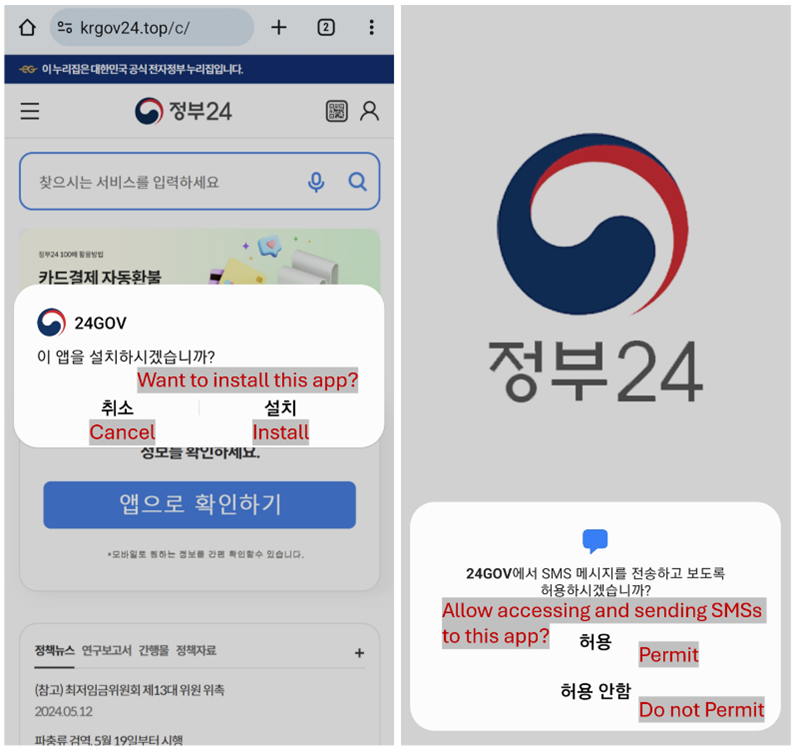
Figure 3 App installation and requesting permissions
Malware Capabilities and Behavior
Once the app is installed and launched, it begins its main function of stealing sensitive information from the user and sending it to a remote server controlled by the attackers. The types of data it targets include:
- Contacts: The malware pulls the user’s entire contact list, which could be used for further deceptive practices or to spread the malware even further.
- SMS Messages: It captures and sends out all incoming SMS messages, which might include private codes used for two-factor authentication or other important information.
- Photos: The app uploads any images stored on the device to the attackers’ server. These could be personal photos or other sensitive images.
- Device Information: It gathers details about the device itself, like the operating system version and phone numbers. This information helps the attackers customize their malicious activities to be more effective.
The malware functions like an agent, capable of receiving and carrying out instructions from the remote server. These commands include:
- ‘ack_contact’: A confirmation signal that the server has received the contacts list.
- ‘ack_sms’: A confirmation signal that the server has received SMS messages.
- ‘ack_image’: A confirmation signal that the server has received images.
- ‘sound_mode_update’: A command that changes the sound settings of the device.
- ‘send_sms’: A command that enables the malware to send SMS messages from the device, which could be used to distribute phishing texts.
Command and Control Servers Investigation
During the investigation, the team discovered several key insights:
Insecure Command and Control Server: Several C2 servers were found to have weak security configurations, which allowed unauthorized access to specific index pages and files without needing credentials. This security lapse provided a deeper insight into the server’s functions and the types of data being gathered.
Upon examination, it was noted that the server’s root directory included multiple folders, each organized for different facets of the operation, such as mimicking banking institutions or postal services.
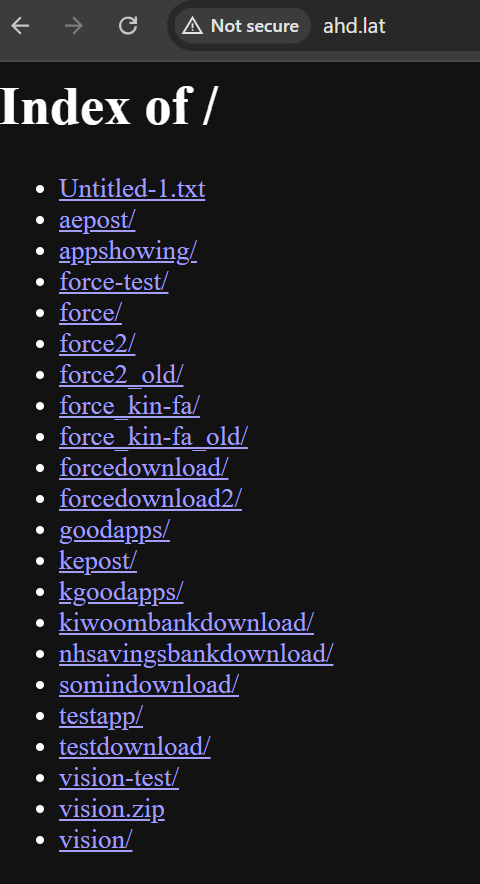
Figure 4 Exposed Indexing page of the root prior to the site being taken down
Due to the server’s misconfiguration, not only were its internal components unintentionally exposed, but the sensitive personal data of victims, which had been compromised, also became publicly accessible. In the ‘uploads’ directory, individual folders were found, each containing photos collected from the victims, highlighting the severity of the data breach.
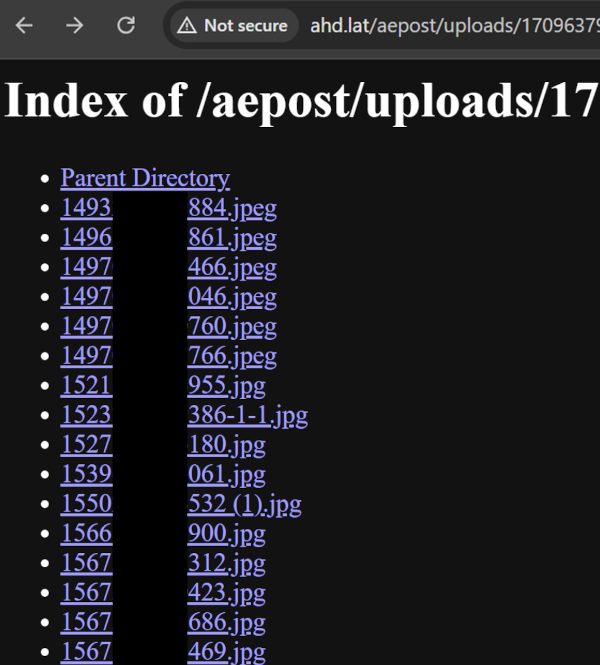
Figure 5 Leaked images list from one of the victims of the ‘aepost’ campaign prior to the site being taken down
Admin Pages: Navigating from the exposed index pages led to admin pages designed for managing victims. These pages displayed a list of devices, complete with device information and various controllable actions. As the number of victims rises, the list of devices on these pages will expand accordingly.
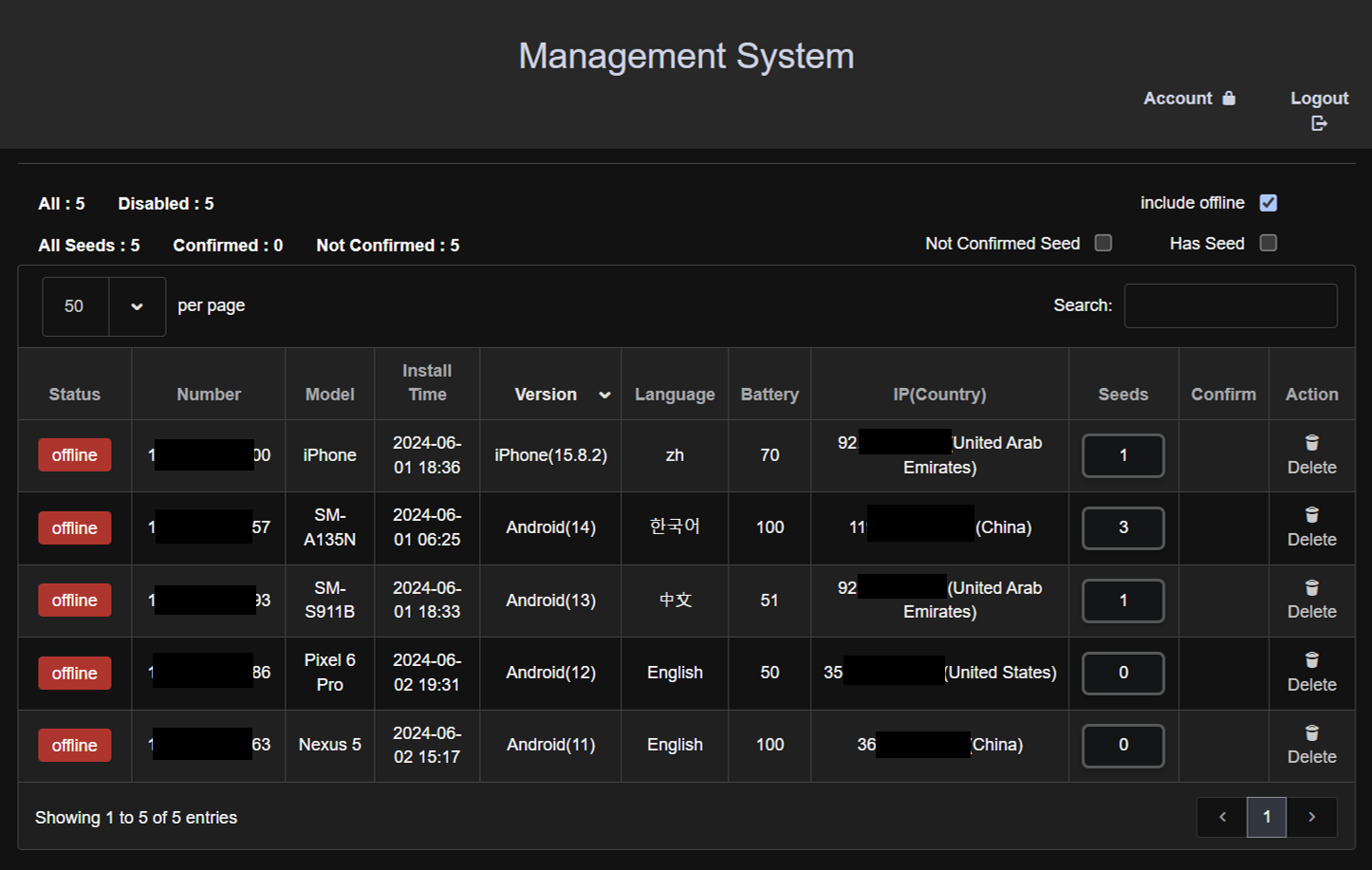
Figure 6 Admin control panel
Targeting Cryptocurrency Wallets: Upon examining the page, it became clear that a primary goal of the attackers was to obtain the mnemonic recovery phrases for cryptocurrency wallets. This suggests a major emphasis on gaining entry to and possibly depleting the crypto assets of victims.
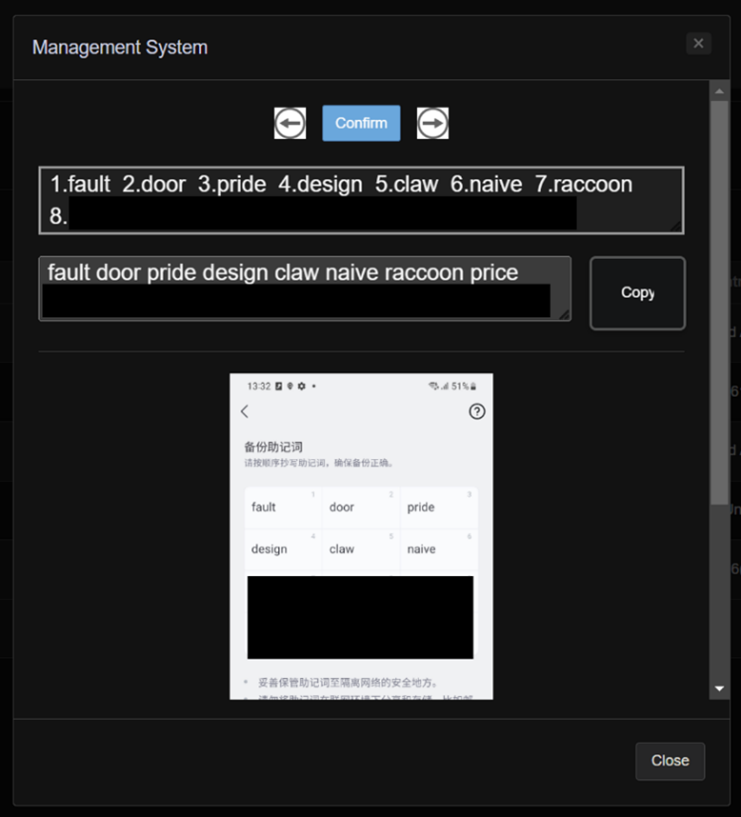
Figure 7 OCR details on Admin page
Data Processing and Management: This threat utilizes Python and Javascript on the server-side to process the stolen data. Specifically, images are converted to text using optical character recognition (OCR) techniques, which are then organized and managed through an administrative panel. This process suggests a high level of sophistication in handling and utilizing the stolen information.
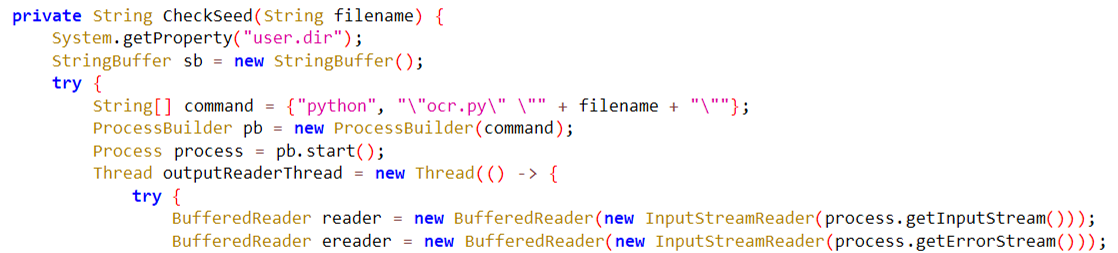
Figure 8 Server-side OCR code
Evolution
Originally, the malware communicated with its command and control (C2) server via simple HTTP requests. While this method was effective, it was also relatively easy for security tools to track and block. In a significant tactical shift, the malware has now adopted WebSocket connections for its communications. This upgrade allows for more efficient, real-time, two-way interactions with the C2 server and helps it avoid detection by traditional HTTP-based network monitoring tools. This change also makes it more challenging for security researchers to analyze traffic and intercept malicious communications.
The malware has also seen substantial improvements in its obfuscation techniques, which further complicates detection efforts by security software and researchers. APK obfuscation now conceals malicious code using strategies like string encoding, the insertion of irrelevant code, and the renaming of functions and variables to confuse analysts. These methods not only create confusion but also delay the detection process, effectively masking the malware’s true operations.
Moreover, the malware’s application and targeting strategies have evolved. Recent observations indicate that the malware has adapted and begun to spread within the UK. This development is significant as it shows that the threat actors are expanding their focus both demographically and geographically. The move into the UK points to a deliberate attempt by the attackers to broaden their operations, likely aiming at new user groups with localized versions of the malware.
Conclusion
The continuous evolution of this malware highlights the ever-changing and sophisticated nature of cyber threats today. Initially masquerading as apps for money loans or government services, it has now adapted to exploit personal emotions by mimicking obituary notices. The research team has discovered that the perpetrators are utilizing OCR technology to analyze and misuse the stolen data for financial benefits. As the malware advances, employing more intricate methods, forecasting its next moves becomes increasingly challenging. Cybercriminals are constantly enhancing their tactics to better infiltrate and manipulate user environments, escalating the danger posed by these threats over time.
Although this malware is not widely prevalent, its impact intensifies when it leverages a victim’s contacts to send deceptive SMS messages. These phishing messages, seemingly sent by a familiar contact, are more likely to be trusted and acted upon by recipients. For instance, an obituary notice appearing to come from a friend’s number could be perceived as authentic, greatly raising the likelihood of the recipient engaging with the scam, especially compared to phishing attempts from unknown sources. This strategy introduces a deceptive layer that significantly enhances the effectiveness and stealthiness of the attack. Early detection of such malware is critical to prevent its proliferation, minimize potential harm, and curb further escalation. In response, the team has taken proactive steps by reporting the active URLs to the relevant content providers, who have promptly removed them.
The discovery of an item labeled “iPhone” in the admin panel indicates that the next stage of this malware’s development might target iOS users. While no direct evidence of an iOS-compatible version has been found yet, the possibility of its existence is genuine. Our team has previously documented data-stealing activities affecting both Android and iOS platforms, suggesting that the threat actors might be working on an iOS variant. This is particularly alarming because, despite iOS’s reputation for security, there are still methods for installing malicious apps outside of the App Store, such as through enterprise certificates and tools like Scalet. This potential shift to iOS highlights the need for vigilance across all mobile platforms.
In such a landscape, it is crucial for users to be cautious about their actions, like installing apps and granting permissions. It is advisable to keep important information securely stored and isolated from devices. Security software has become not just a recommendation but a necessity for protecting devices. The McAfee Mobile Research team continues to stay alert, implementing robust security measures to counter these advanced threats. McAfee Mobile Security products are designed to detect and defend against not only malware but also other unwanted software. For further details, please visit our McAfee Mobile Security website.
Indicators of Compromise
SHA256 Hash(es):
- 5b634ac2eecc2bb83c0403edba30a42cc4b564a3b5f7777fe9dada3cd87fd761
- 4cf35835637e3a16da8e285c1b531b3f56e1cc1d8f6586a7e6d26dd333b89fcf
- 3d69eab1d8ce85d405c194b30ac9cc01f093a0d5a6098fe47e82ec99509f930d
- 789374c325b1c687c42c8a2ac64186c31755bfbdd2f247995d3aa2d4b6c1190a
- 34c2a314dcbb5230bf79e85beaf03c8cee1db2b784adf77237ec425a533ec634
- f7c4c6ecbad94af8638b0b350faff54cb7345cf06716797769c3c8da8babaaeb
- 94aea07f38e5dfe861c28d005d019edd69887bc30dcc3387b7ded76938827528
- 1d9afa23f9d2ab95e3c2aecbb6ce431980da50ab9dea0d7698799b177192c798
- 19060263a9d3401e6f537b5d9e6991af637e1acb5684dbb9e55d2d9de66450f2
- 0ca26d6ed1505712b454719cb062c7fbdc5ae626191112eb306240d705e9ed23
- d340829ed4fe3c5b9e0b998b8a1afda92ca257732266e3ca91ef4f4b4dc719f8
- 149bd232175659434bbeed9f12c8dd369d888b22afaf2faabc684c8ff2096f8c
- f9509e5e48744ccef5bfd805938bf900128af4e03aeb7ec21c1e5a78943c72e7
- 26d761fac1bd819a609654910bfe6537f42f646df5fc9a06a186bbf685eef05b
- 0e778b6d334e8d114e959227b4424efe5bc7ffe5e943c71bce8aa577e2ab7cdb
- 8bbcfe8555d61a9c033811892c563f250480ee6809856933121a3e475dd50c18
- 373e5a2ee916a13ff3fc192fb59dcd1d4e84567475311f05f83ad6d0313c1b3b
- 7d346bc965d45764a95c43e616658d487a042d4573b2fdae2be32a0b114ecee6
- 1bff1823805d95a517863854dd26bbeaa7f7f83c423454e9abd74612899c4484
- 020c51ca238439080ec12f7d4bc4ddbdcf79664428cd0fb5e7f75337eff11d8a
Domain(s):


