- Why I recommend this OnePlus phone over the S25 Ultra - especially at this new low price
- I replaced my laptop with Microsoft's 12-inch Surface Pro for weeks - here's my buying advice now
- This palm recognition smart lock doubles as a video doorbell (and has no monthly fees)
- Samsung is giving these Galaxy phones a big One UI upgrade - here's which models qualify
- 7 MagSafe accessories that I recommend every iPhone user should have
New HiddenAds malware affects 1M+ users and hides on the Google Play Store | McAfee Blog

Authored by Dexter Shin
McAfee’s Mobile Research Team has identified new malware on the Google Play Store. Most of them are disguising themselves as cleaner apps that delete junk files or help optimize their batteries for device management. However, this malware hides and continuously show advertisements to victims. In addition, they run malicious services automatically upon installation without executing the app.
HiddenAds functions and promotion
They exist on Google Play even though they have malicious activities, so the victim can search for the following apps to optimize their device.
Users may generally think installing the app without executing it is safe. But you may have to change your mind because of this malware. When you install this malware on your device, it is executed without interaction and executes a malicious service.
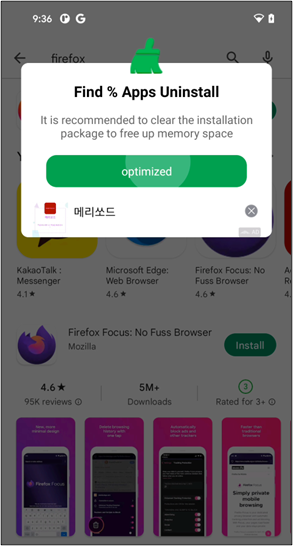
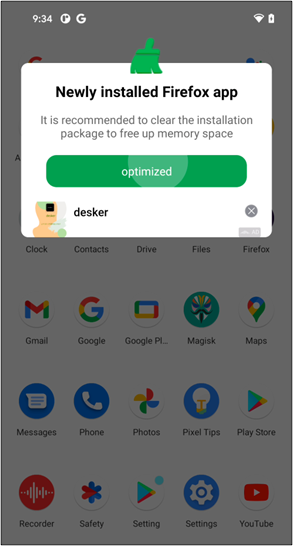
In addition, they try to hide themselves to prevent users from noticing and deleting apps. Change their icon to a Google Play icon that users are familiar with and change its name to ‘Google Play’ or ‘Setting.’

Automatically executed services constantly display advertisements to victims in a variety of ways.

These services also induce users to run an app when they install, uninstall, or update apps on their devices.
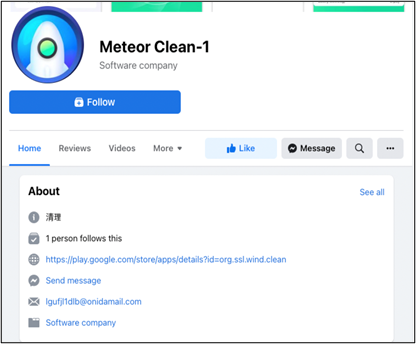
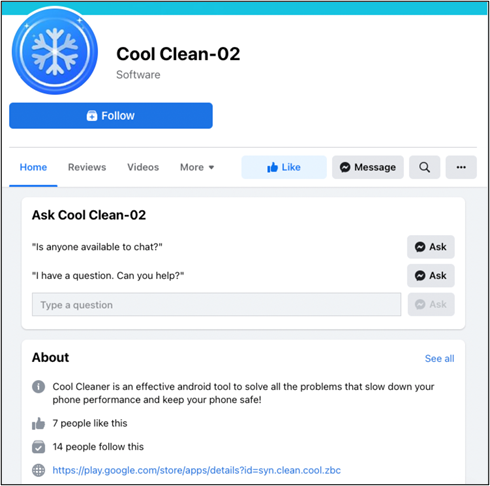
To promote these apps to new users, the malware authors created advertising pages on Facebook. Because it is the link to Google Play distributed through legitimate social media, users will download it without a doubt.

How it works
This malware uses the Contact Provider. The Contact Provider is the source of data you see in the device’s contacts application, and you can also access its data in your own application and transfer data between the device and online services. For this, Google provides ContactsContract class. ContactsContract is the contract between the Contacts Provider and applications. In ContactsContract, there is a class called Directory. A Directory represents a contacts corpus and is implemented as a Content Provider with its unique authority. So, developers can use it if they want to implement a custom directory. The Contact Provider can recognize that the app is using a custom directory by checking special metadata in the manifest file.
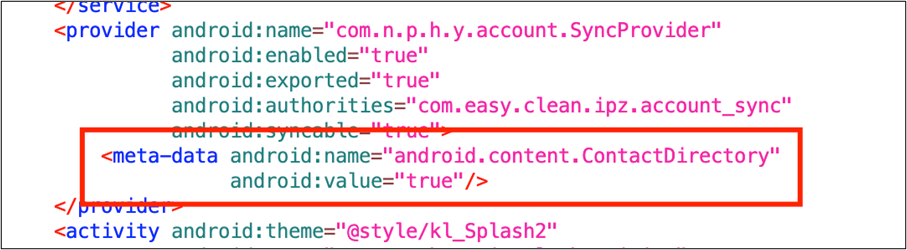
The important thing is the Contact Provider automatically interrogates newly installed or replaced packages. Thus, installing a package containing special metadata will always call the Contact Provider automatically.
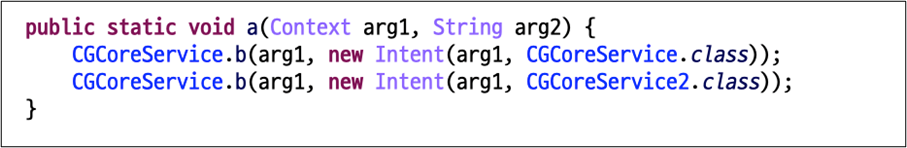
The first activity defined in the application tag in the manifest file is executed as soon as you install it just by declaring the metadata. The first activity of this malware will create a permanent malicious service for displaying advertisements.
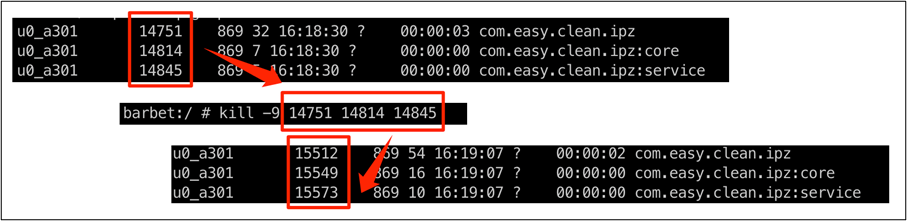
In addition, the service process will generate immediately even if it is forced to kill.
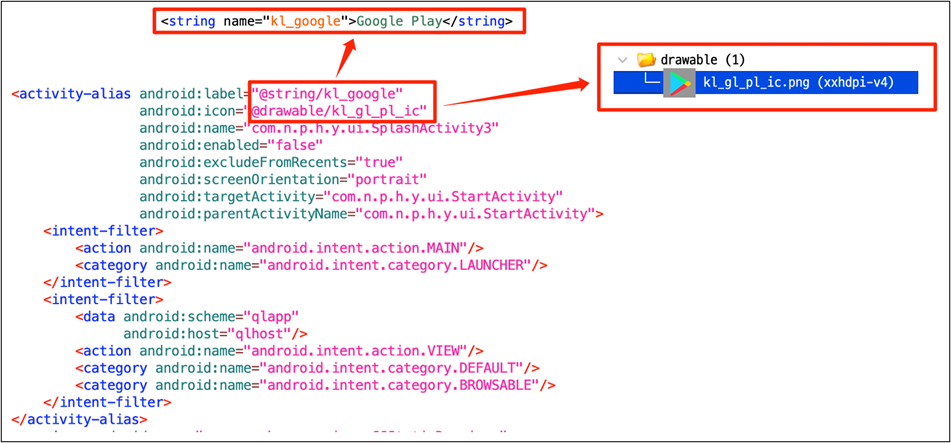
Next, they change their icons and names using the <activity-alias> tag to hide.
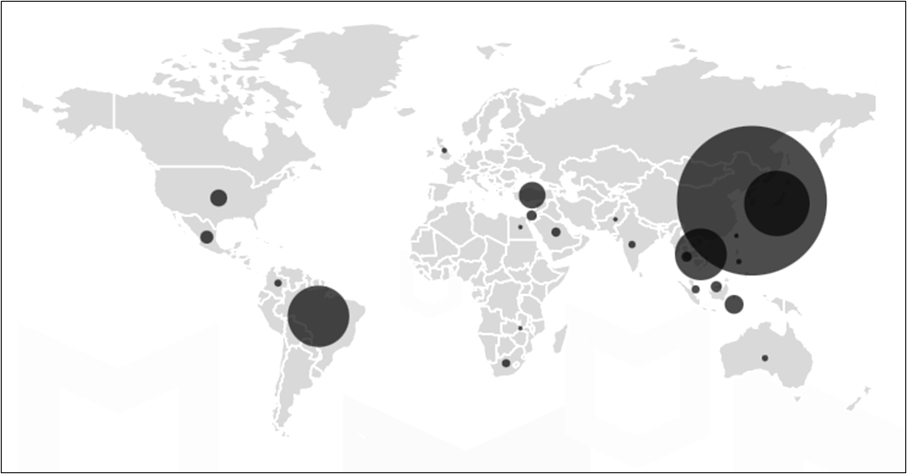
Users infected worldwide
It is confirmed that users have already installed these apps from 100K to 1M+. Considering that the malware works when it is installed, the installed number is reflected as the victim’s number. According to McAfee telemetry data, this malware and its variants affect a wide range of countries, including South Korea, Japan, and Brazil:
Conclusion
This malware is auto-starting malware, so as soon as the users download it from Google Play, they are infected immediately. And it is still constantly developing variants that are published by different developer accounts. Therefore, it is not easy for users to notice this type of malware.
We already disclosed this threat to Google and all reported applications were removed from the Play Store. Also, McAfee Mobile Security detects this threat as Android/HiddenAds and protects you from this type of malware. For more information about McAfee Mobile Security, visit https://www.mcafeemobilesecurity.com
Indicators of Compromise
Applications:
| App Name | Package Name | Downloads |
| Junk Cleaner | cn.junk.clean.plp | 1M+ |
| EasyCleaner | com.easy.clean.ipz | 100K+ |
| Power Doctor | com.power.doctor.mnb | 500K+ |
| Super Clean | com.super.clean.zaz | 500K+ |
| Full Clean -Clean Cache | org.stemp.fll.clean | 1M+ |
| Fingertip Cleaner | com.fingertip.clean.cvb | 500K+ |
| Quick Cleaner | org.qck.cle.oyo | 1M+ |
| Keep Clean | org.clean.sys.lunch | 1M+ |
| Windy Clean | in.phone.clean.www | 500K+ |
| Carpet Clean | og.crp.cln.zda | 100K+ |
| Cool Clean | syn.clean.cool.zbc | 500K+ |
| Strong Clean | in.memory.sys.clean | 500K+ |
| Meteor Clean | org.ssl.wind.clean | 100K+ |
SHA256:
- 4b9a5de6f8d919a6c534bc8595826b9948e555b12bc0e12bbcf0099069e7df90
- 4d8472f0f60d433ffa8e90cc42f642dcb6509166cfff94472a3c1d7dcc814227
- 5ca2004cfd2b3080ac4958185323573a391dafa75f77246a00f7d0f3b42a4ca3
- 5f54177a293f9678797e831e76fd0336b0c3a4154dd0b2175f46c5a6f5782e24
- 7a502695e1cab885aee1a452cd29ce67bb1a92b37eed53d4f2f77de0ab93df9b
- 64d8bd033b4fc7e4f7fd747b2e35bce83527aa5d6396aab49c37f1ac238af4bd
- 97bd1c98ddf5b59a765ba662d72e933baab0a3310c4cdbc50791a9fe9881c775
- 268a98f359f2d56497be63a31b172bfbdc599316fb7dec086a937765af42176f
- 690d658acb9022765e1cf034306a1547847ca4adc0d48ac8a9bbdf1e6351c0f7
- 75259246f2b9f2d5b1da9e35cab254f71d82169809e5793ee9c0523f6fc19e4b
- a5cbead4c9868f83dd9b4dc49ca6baedffc841772e081a4334efc005d3a87314
- c75f99732d4e4a3ec8c19674e99d14722d8909c82830cd5ad399ce6695856666
Domains:
- http[://]hw.sdk.functionads.com:8100
!function(f,b,e,v,n,t,s)
{if(f.fbq)return;n=f.fbq=function(){n.callMethod?
n.callMethod.apply(n,arguments):n.queue.push(arguments)};
if(!f._fbq)f._fbq=n;n.push=n;n.loaded=!0;n.version=’2.0′;
n.queue=[];t=b.createElement(e);t.async=!0;
t.src=v;s=b.getElementsByTagName(e)[0];
s.parentNode.insertBefore(t,s)}(window, document,’script’,
‘https://connect.facebook.net/en_US/fbevents.js’);
fbq(‘init’, ‘448732493334171’);
fbq(‘track’, ‘PageView’);
!function(f,b,e,v,n,t,s)
{if(f.fbq)return;n=f.fbq=function(){n.callMethod?
n.callMethod.apply(n,arguments):n.queue.push(arguments)};
if(!f._fbq)f._fbq=n;n.push=n;n.loaded=!0;n.version=’2.0′;
n.queue=[];t=b.createElement(e);t.async=!0;
t.src=v;s=b.getElementsByTagName(e)[0];
s.parentNode.insertBefore(t,s)}(window, document,’script’,
‘https://connect.facebook.net/en_US/fbevents.js’);
fbq(‘init’, ‘187610925152304’);
fbq(‘track’, ‘PageView’);
// load Facebook
!function(f,b,e,v,n,t,s){if(f.fbq)return;n=f.fbq=function(){n.callMethod?
n.callMethod.apply(n,arguments):n.queue.push(arguments)};if(!f._fbq)f._fbq=n;
n.push=n;n.loaded=!0;n.version=’2.0′;n.queue=[];t=b.createElement(e);t.async=!0;
t.src=v;s=b.getElementsByTagName(e)[0];s.parentNode.insertBefore(t,s)}(window,
document,’script’,’https://connect.facebook.net/en_US/fbevents.js’);
fbq(‘init’, ‘766537420057144’);
fbq(‘track’, “PageView”);
//document.write(‘x3Cnoscript>x3Cimg height=”1″ width=”1″ style=”display:none” src=”https://www.facebook.com/tr?id=766537420057144&ev=PageView&noscript=1″ />x3C/noscript>’);

