- I tested a Pixel Tablet without any Google apps, and it's more private than even my iPad
- My search for the best MacBook docking station is over. This one can power it all
- This $500 Motorola proves you don't need to spend more on flagship phones
- Finally, budget wireless earbuds that I wouldn't mind putting my AirPods away for
- I replaced my Linux system with this $200 Windows mini PC - and it left me impressed
New Malicious Clicker found in apps installed by 20M+ users | McAfee Blog

Authored by SangRyol Ryu
Cybercriminals are always after illegal advertising revenue. As we have previously reported, we have seen many mobile malwares masquerading as a useful tool or utility, and automatically crawling ads in the background. Recently the McAfee Mobile Research Team has identified new Clicker malware that sneaked into Google Play. In total 16 applications that were previously on Google Play have been confirmed to have the malicious payload with an assumed 20 million installations.
McAfee security researchers notified Google and all of the identified apps are no longer available on Google Play. Users are also protected by Google Play Protect, which blocks these apps on Android. McAfee Mobile Security products detect this threat as Android/Clicker and protect you from malware. For more information, to get fully protected, visit McAfee Mobile Security.
The malicious code was found on useful utility applications like Flashlight (Torch), QR readers, Camara, Unit converters, and Task managers:

Once the application is opened, it downloads its remote configuration by executing an HTTP request. After the configuration is downloaded, it registers the FCM (Firebase Cloud Messaging) listener to receive push messages. At first glance, it seems like well-made android software. However, it is hiding ad fraud features behind, armed with remote configuration and FCM techniques.
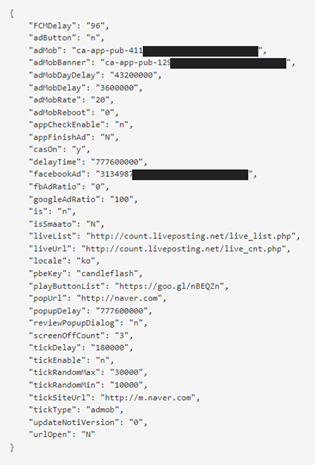
| Attribute name | Known meaning of the value |
| FCMDelay | Initial start hours after first installation |
| adButton | Visivility of a button of Advertisement |
| adMob | AdMob unit ID |
| adMobBanner | AdMob unit ID |
| casOn | Whether CAS library works or not |
| facebookAd | FaceBook Ad ID |
| fbAdRatio | Ratio of FB AD |
| googleAdRatio | Ratio of AdMob |
| is | Decide BootService to run or not |
| urlOpen | to open popup or not when starts PowerService |
| popUrl | URL for PowerService |
| popUpDelay | Delay time for PowerService |
| liveUrl | URL for livecheck service |
| pbeKey | Key for making unique string |
| playButtonList | URL for other service |
| reviewPopupDialog | ‘y’ it shows review dialog |
| tickDelay | Delay time for TickService |
| tickEnable | Value of TickService enabled |
| tickRandomMax | Value of TickService random delay |
| tickRandomMin | Value of TickService random delay |
| tickType | Set the type of TickService |
| updateNotiVersion | Value for showing update activity |
The FCM message has various types of information and that includes which function to call and its parameters. The picture below shows some of FCM message history:
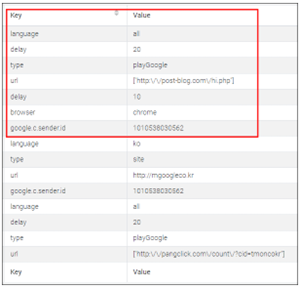
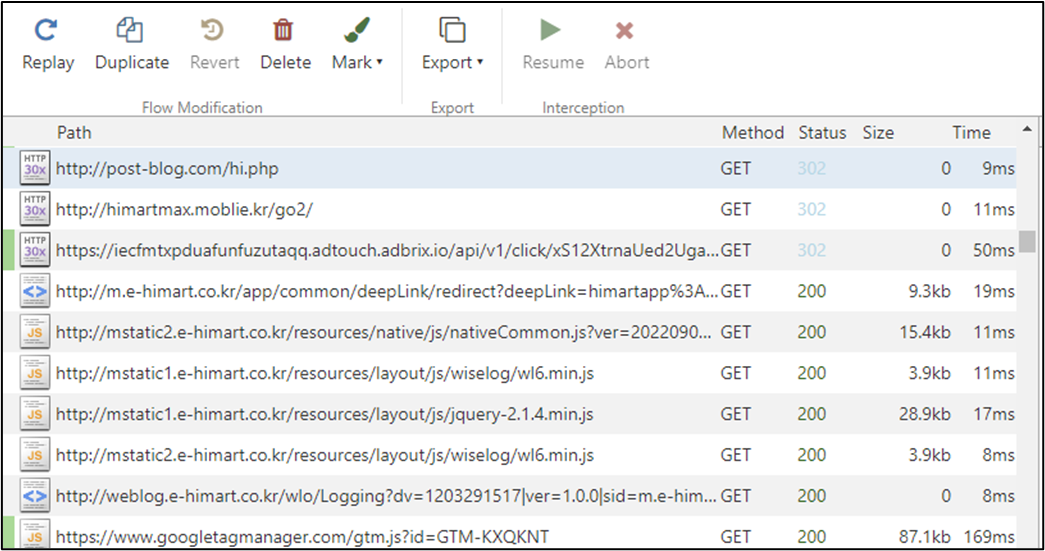
When an FCM message receives and meets some condition, the latent function starts working. Mainly, it is visiting websites which are delivered by FCM message and browsing them successively in the background while mimicking user’s behavior. This may cause heavy network traffic and consume power without user awareness during the time it generates profit for the threat actor behind this malware. In the picture below there is an example of the network traffic generated to get the information required to generate fake clicks and the websites visited without user’s consent or interaction:
So far, we have identified two pieces of code related to this threat. One is “com.click.cas” library which focuses on the automated clicking functionality while “com.liveposting” library works as an agent and runs hidden adware services:
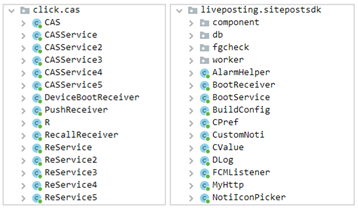
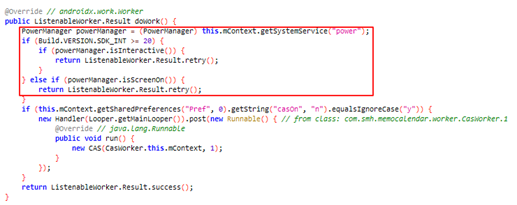
Depending on the version of the applications, some have both libraries working together while other applications only have “com.liveposting” library. The malware is using installation time, random delay and user presence to avoid the users from noticing these malicious acts. The malicious behavior won’t start if the installation time is within an hour and during the time the user is using the device, probably to stay under the radar and avoid being detected right away:
Clicker malware targets illicit advertising revenue and can disrupt the mobile advertising ecosystem. Malicious behavior is cleverly hidden from detection. Malicious actions such as retrieving crawl URL information via FCM messages start in the background after a certain period of time and are not visible to the user.
McAfee Mobile Security detects and removes malicious applications like this one that may run in the background without user’s knowledge. Also, we recommend having a security software installed and activated so you will be notified of any mobile threats present on your device in a timely manner. Once you remove this and other malicious applications, you can expect an extended battery time and you will notice reduced mobile data usage while ensuring that your sensitive and personal data is protected from this and other types of threats.
liveposting[.]net
sideup[.]co[.]kr
msideup[.]co[.]kr
post-blog[.]com
pangclick[.]com
modooalba[.]net
| SHA256 | Package name | Name | Downloaded |
| a84d51b9d7ae675c38e260b293498db071b1dfb08400b4f65ae51bcda94b253e | com.hantor.CozyCamera | High-Speed Camera | 10,000,000+ |
| 00c0164d787db2ad6ff4eeebbc0752fcd773e7bf016ea74886da3eeceaefcf76 | com.james.SmartTaskManager | Smart Task Manager | 5,000,000+ |
| b675404c7e835febe7c6c703b238fb23d67e9bd0df1af0d6d2ff5ddf35923fb3 | kr.caramel.flash_plus | Flashlight+ | 1,000,000+ |
| 65794d45aa5c486029593a2d12580746582b47f0725f2f002f0f9c4fd1faf92c | com.smh.memocalendar | 달력메모장 | 1,000,000+ |
| 82723816760f762b18179f3c500c70f210bbad712b0a6dfbfba8d0d77753db8d | com.joysoft.wordBook | K-Dictionary | 1,000,000+ |
| b252f742b8b7ba2fa7a7aa78206271747bcf046817a553e82bd999dc580beabb | com.kmshack.BusanBus | BusanBus | 1,000,000+ |
| a2447364d1338b73a6272ba8028e2524a8f54897ad5495521e4fab9c0fd4df6d | com.candlencom.candleprotest | Flashlight+ | 500,000+ |
| a3f484c7aad0c49e50f52d24d3456298e01cd51595c693e0545a7c6c42e460a6 | com.movinapp.quicknote | Quick Note | 500,000+ |
| a8a744c6aa9443bd5e00f81a504efad3b76841bbb33c40933c2d72423d5da19c | com.smartwho.SmartCurrencyConverter | Currency Converter | 500,000+ |
| 809752e24aa08f74fce52368c05b082fe2198a291b4c765669b2266105a33c94 | com.joysoft.barcode | Joycode | 100,000+ |
| 262ad45c077902d603d88d3f6a44fced9905df501e529adc8f57a1358b454040 | com.joysoft.ezdica | EzDica | 100,000+ |
| 1caf0f6ca01dd36ba44c9e53879238cb46ebb525cb91f7e6c34275c4490b86d7 | com.schedulezero.instapp | Instagram Profile Downloader | 100,000+ |
| 78351c605cfd02e1e5066834755d5a57505ce69ca7d5a1995db5f7d5e47c9da1 | com.meek.tingboard | Ez Notes | 100,000+ |
| 4dd39479dd98124fd126d5abac9d0a751bd942b541b4df40cb70088c3f3d49f8 | com.candlencom.flashlite | 손전등 | 1,000+ |
| 309db11c2977988a1961f8a8dbfc892cf668d7a4c2b52d45d77862adbb1fd3eb | com.doubleline.calcul | 계산기 | 100+ |
| bf1d8ce2deda2e598ee808ded71c3b804704ab6262ab8e2f2e20e6c89c1b3143 | com.dev.imagevault | Flashlight+ | 100+ |

