- Why I recommend this OnePlus phone over the S25 Ultra - especially at this new low price
- I replaced my laptop with Microsoft's 12-inch Surface Pro for weeks - here's my buying advice now
- This palm recognition smart lock doubles as a video doorbell (and has no monthly fees)
- Samsung is giving these Galaxy phones a big One UI upgrade - here's which models qualify
- 7 MagSafe accessories that I recommend every iPhone user should have
Novel Phishing Method Used in Android/iOS Financial Fraud Campaigns

A recently discovered sophisticated mobile phishing technique has been observed in financial fraud campaigns across the Czech Republic, Hungary and Georgia.
This phishing method leverages progressive web applications (PWA), these types of web applications offer a native-app-like experience and are gaining momentum on both Android and iOS devices.
This technique is noteworthy because it installs a phishing application from a third-party website without the user having to allow third-party app installation, said ESET, the cybersecurity firm which detected the campaigns.
Decoding PWA Phishing on iOS and Android
This new phishing technique is only possible because of how PWAs work, bypassing the need for the user to allow third-party installation on their mobile.
On iOS, phishing websites impersonating well-known applications’ landing pages and instruct victims to add a PWA to their home screens.
Before the landing pages are set up, the threat defined the target PWA as a standalone in a single file called the manifest that rules how the PWA will behave. This results in the PWA behaving like a regular mobile app.
On Android devices, the PWA is installed after confirming custom pop-ups in the browser, which results in the silent installation of a web Android Package Kit (WebAPK).
WebAPKs are a special kind of APK, the standard Android application file, that can be considered an upgraded version of PWAs, as the Chrome browser generates a native Android application from a PWA.
ESET added that WebAPKs installed as part of the detected phishing campaigns even appeared to be installed directly from the Google Play store.
This technique was first disclosed by CSIRT KNF, a computer security incident response team dedicated to Poland’s financial sector, in July 2023.
Financial Fraud Campaigns Targeted Banks in Czech Republic, Hungary and Georgia
In November 2023, ESET observed mobile phishing campaigns targeting several Czech banks, the Hungarian OTP Bank and the Georgian TBC Bank, using this same technique alongside standard phishing delivery techniques.
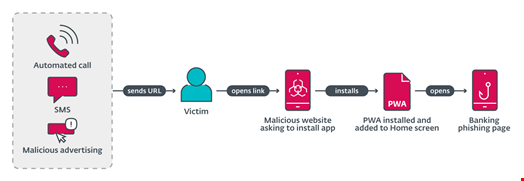
These phishing campaigns used three different URL delivery mechanisms:
- Voice call delivery: an automated call warns the user about an out-of-date banking app and asks the user to select an option on the numerical keyboard. After pressing the correct button, a phishing URL is sent via SMS
- SMS delivery: text messages with a phishing link were sent indiscriminately to Czech phone numbers
- Malvertising delivery: ads including a call to action, like a limited offer for users who “download an update below,” were registered on Meta platforms like Instagram and Facebook
All the malicious links led to phishing websites, encouraging victims to install a “new version” of the banking application.
“We discovered the first phishing-via-PWA case in early November 2023 and noticed the transition to WebAPKs in mid-November 2023,” the ESET researchers noted.
“Command and control (C2) servers that received information from phishing applications were first discovered in March 2024, with data in them confirming that they were probably not operational earlier.”
Based on these C2 servers and backend infrastructure, the researchers concluded that two different threat actors were operating the campaigns.
ESET has notified the targeted banks.

