- Apple doesn't need better AI as much as AI needs Apple to bring its A-game
- I tested a Pixel Tablet without any Google apps, and it's more private than even my iPad
- My search for the best MacBook docking station is over. This one can power it all
- This $500 Motorola proves you don't need to spend more on flagship phones
- Finally, budget wireless earbuds that I wouldn't mind putting my AirPods away for
OneNote documents spread malware in several countries

A new phishing campaign abuses OneNote documents to infect computers with the infamous AsyncRAT malware, targeting users in the U.K., Canada and the U.S.
As Microsoft decided to change the default of its Office products to block macros on files downloaded from the internet, cybercriminals saw one of their favorite infection methods vanish.
Some cybercriminals have already found a workaround to keep using some Microsoft Office products, like abusing the XLL files from Excel. Some other cybercriminals have found a different way to keep abusing Microsoft products for infecting computers with malware: infected OneNote documents.
SEE: Mobile device security policy (TechRepublic Premium)
Phishing attacks deliver AsyncRAT malware
A new Bitdefender study exposes a phishing campaign abusing OneNote to infect computers with malware. In that attack campaign, cybercriminals impersonated Ultramar, a Canadian gas and home fuel retailer, sending phishing emails supposedly coming from the company (Figure A).
Figure A
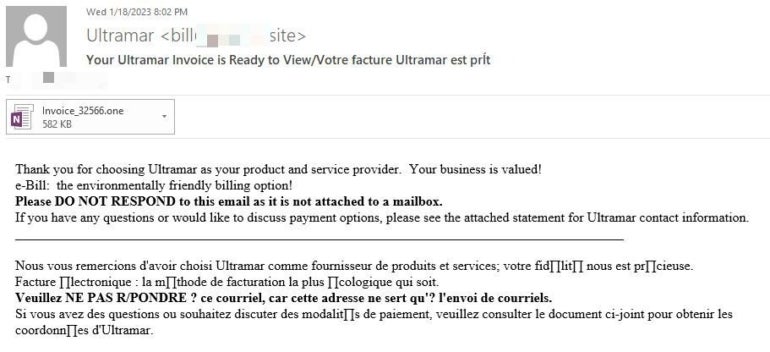
As can be seen in Figure A, the email contains text in both English and French language, but most importantly an attached file named Invoice_32566.one — the .one file extension indicating a OneNote file.
A second similar phishing campaign hit Canada, the U.K. and the U.S. with another filename for the attachment, Invoice_76562.one.
The payloads triggered by those OneNote documents, once opened, were downloaded from a Catholic Church in Canada and a Digital Service Provider in India. Both were compromised by the attackers or possibly brought to some initial access broker (IAB) online and used for hosting the malwares. This is a common technique used by cybercriminals to avoid detection for a longer period of time by using a legitimate website to host their malicious code.
In the end, users opening the OneNote documents were infected with AsyncRAT, which Bitdefender describes as “a nifty remote access tool designed to stealthily let an attacker infiltrate the devices of the target victim’s device.”
What is AsyncRAT?
AsyncRAT source code has been available for free on the internet since 2019, which means the original version is detected by most security solutions, if not all. Yet, it also means developers can use the source code of AsyncRAT and modify it to add or remove features or to render it less detectable.
Currently, that malware is capable of recording screens, capturing keystrokes, manipulating files on the system, executing code or launching distributed denial-of-service attacks. This means it can be used for a variety of purposes.
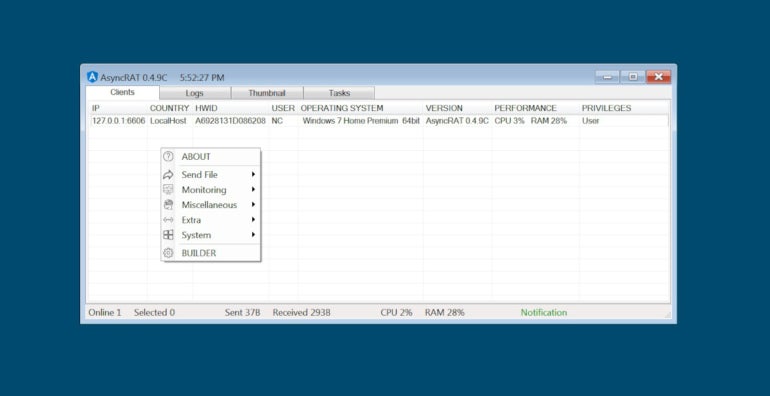
It has already been used by cyberespionage threat actors or for financially-oriented goals. Once a computer is infected with AsyncRAT, the attacker can see the machine in the tools administration panel and act on the machine as needed (Figure B). Several infected machines can be handled in the same interface.
Figure B
More attacks in the wild
Bitdefender researchers are not the only ones who have investigated the new threat AsyncRAT poses. December 2022, Trustwave also reported phishing attack campaigns, this time delivering the Formbook malware, a spread information stealer capable of stealing passwords, taking screen captures, executing code and more.
“It’s clear to see how cybercriminals leverage new attack vectors or less-detected means to compromise user devices,” declared Adrian Miron, manager at Bitdefender’s Cyber Threat Intelligence Lab. “These campaigns are likely to proliferate in coming months, with cybercrooks testing out better or improved angles to compromise victims.”
How to protect from this threat?
Companies that don’t use OneNote should block .one extensions in their email servers. This would prevent any internal users from accidentally opening infected files on company tools. Instead, employees should request files in another format like .doc or .xlsx to avoid potential exposure. As a more extreme step, these companies could prevent employees from downloading or using OneNote on company tools and systems, but this is not recommended as some employees might currently use the tool.
Malicious OneNote files mostly make use of attached files inside the document. When accessing those attachments, a warning is raised by the software to tell the user it might harm the computer and data. Yet, experience has shown that users often neglect those warnings and just click the validation button. Companies can work to prevent these threats by:
- Raising awareness on potentially harmful files and links to all employees.
- Building protocols and training on how to respond to warnings of malicious files or links.
- Deploying security solutions that detect malicious code when it is triggered from a OneNote file or other threats.
- Updating and patching all systems and software to avoid being compromised by a common vulnerability.
Disclosure: I work for Trend Micro, but the views expressed in this article are mine.

