- Learn with Cisco at Cisco Live 2025 in San Diego
- This Eufy robot vacuum has a built-in handheld vac - and just hit its lowest price
- I highly recommend this Lenovo laptop, and it's nearly 50% off
- Disney+ and Hulu now offer prizes, freebies, and other perks to keep you subscribed
- This new YouTube Shorts feature lets you circle to search videos more easily
Oracle October 2022 Critical Patch Update Addresses 179 CVEs

Oracle addresses 179 CVEs in its fourth and final quarterly update of 2022 with 370 patches, including 56 critical updates.
Background
On October 18, Oracle released its Critical Patch Update (CPU) for October 2022, the fourth and final quarterly update of the year. This CPU contains fixes for 179 CVEs in 370 security updates across 27 Oracle product families. Out of the 370 security updates published this quarter, 56 patches were assigned a critical severity. Medium severity patches accounted for the bulk of security patches at 163, followed by high severity patches at 144.
This quarter’s update includes 83 medium severity CVEs, followed by 57 high severity CVEs and 7 low severity CVEs.
| Severity | Issues Patched | CVEs |
|---|---|---|
| Critical | 56 | 32 |
| High | 144 | 57 |
| Medium | 163 | 83 |
| Low | 7 | 7 |
| Total | 370 | 179 |
Analysis
This quarter, the Oracle Communications product family contained the highest number of patches at 74, accounting for 20% of the total patches, followed by Oracle Fusion Middleware with 56 patches, which accounted for 15.14% of the total patches.
Oracle did not include security patches for five product families:
- Oracle Airlines Data Model
- Oracle Big Data Graph
- Oracle NoSQL Database
- Oracle SQL Developer
- Oracle TimesTen In-Memory Database
While these five product families did not receive security patches, Oracle notes that there are third-party patches included as part of its CPU release that affect them:
| Oracle Product Family | Component | CVE |
|---|---|---|
| Oracle Airlines Data Model | Installation (Apache Commons BeanUtils) | CVE-2019-10086 |
| Oracle Airlines Data Model | Installation (Apache Commons IO) | CVE-2021-29425 |
| Oracle Airlines Data Model | Installation (Apache Groovy) | CVE-2020-17521 |
| Oracle Airlines Data Model | Installation (Apache Log4j) | CVE-2021-4104 |
| Oracle Airlines Data Model | Installation (Nimbus JOSE+JWT) | CVE-2019-17195 |
| Oracle Airlines Data Model | Installation (Spring Framework) | CVE-2021-22118 |
| Oracle Airlines Data Model | Installation (Spring Framework) | CVE-2020-5421 |
| Oracle Airlines Data Model | Installation (jackson-databind) | CVE-2020-9546 |
| Oracle Airlines Data Model | Installation (jackson-databind) | CVE-2020-10650 |
| Oracle Airlines Data Model | Installation (jackson-databind) | CVE-2020-10672 |
| Oracle Airlines Data Model | Installation (jackson-databind) | CVE-2020-10673 |
| Oracle Airlines Data Model | Installation (jackson-databind) | CVE-2020-10968 |
| Oracle Airlines Data Model | Installation (jackson-databind) | CVE-2020-10969 |
| Oracle Airlines Data Model | Installation (jackson-databind) | CVE-2020-11111 |
| Oracle Airlines Data Model | Installation (jackson-databind) | CVE-2020-11112 |
| Oracle Airlines Data Model | Installation (jackson-databind) | CVE-2020-11113 |
| Oracle Airlines Data Model | Installation (jackson-databind) | CVE-2020-14195 |
| Oracle Airlines Data Model | Installation (jackson-databind) | CVE-2020-25649 |
| Oracle Airlines Data Model | Installation (jackson-databind) | CVE-2020-36189 |
| Oracle Airlines Data Model | Installation (jackson-databind) | CVE-2020-9547 |
| Oracle Airlines Data Model | Installation (jackson-databind) | CVE-2020-9548 |
| Oracle Big Data Spatial and Graph | Big Data Graph (Apache Tomcat) | CVE-2022-34305 |
| Oracle NoSQL Database | Administration (Google Gson) | CVE-2022-25647 |
| Oracle NoSQL Database | Administration (jackson-databind) | CVE-2020-36518 |
| Oracle SQL Developer | Install (Apache Batik) | CVE-2020-11987 |
| Oracle SQL Developer | Install (Apache Kafka) | CVE-2021-38153 |
| Oracle SQL Developer | Install (Apache Kafka) | CVE-2021-26291 |
| Oracle TimesTen In-Memory Database | Kubernetes Operator (Golang Go) | CVE-2022-28327 |
| Oracle TimesTen In-Memory Database | Kubernetes Operator (Golang Go) | CVE-2022-24675 |
A full breakdown of the patches for this quarter can be seen in the following table, which also includes a count of vulnerabilities that can be exploited over a network without authentication.
| Oracle Product Family | Number of Patches | Remote Exploit without Authentication |
|---|---|---|
| Oracle Communications | 74 | 64 |
| Oracle Fusion Middleware | 56 | 43 |
| Oracle MySQL | 37 | 11 |
| Oracle Communications Applications | 27 | 21 |
| Oracle Retail Applications | 27 | 21 |
| Oracle Financial Services Applications | 24 | 16 |
| Oracle Siebel CRM | 14 | 12 |
| Oracle Supply Chain | 13 | 9 |
| Oracle JD Edwards | 10 | 9 |
| Oracle Virtualization | 10 | 3 |
| Oracle Java SE | 9 | 9 |
| Oracle Database Server | 8 | 1 |
| Oracle PeopleSoft | 8 | 4 |
| Oracle Systems | 8 | 4 |
| Oracle Utilities Applications | 6 | 4 |
| Oracle Construction and Engineering | 5 | 2 |
| Oracle E-Business Suite | 5 | 4 |
| Oracle Enterprise Manager | 5 | 4 |
| Oracle HealthCare Applications | 5 | 4 |
| Oracle Insurance Applications | 5 | 3 |
| Oracle Hospitality Applications | 4 | 2 |
| Oracle Commerce | 3 | 2 |
| Oracle Essbase | 2 | 1 |
| Oracle GoldenGate | 2 | 1 |
| Oracle Communications Data Model | 1 | 0 |
| Oracle Secure Backup | 1 | 1 |
| Oracle Hyperion | 1 | 1 |
| Oracle Airlines Data Model | 0 | 0 |
| Oracle Big Data Graph | 0 | 0 |
| Oracle NoSQL Database | 0 | 0 |
| Oracle SQL Developer | 0 | 0 |
| Oracle TimesTen In-Memory Database | 0 | 0 |
2021 Critical Patch Update totals: 854 CVEs patched
The combined total of CVEs patched in this year’s CPUs was 854. This year saw a 7.27% decrease in the number of CVEs patched compared to 2021, when Oracle patched a total of 921 CVEs.
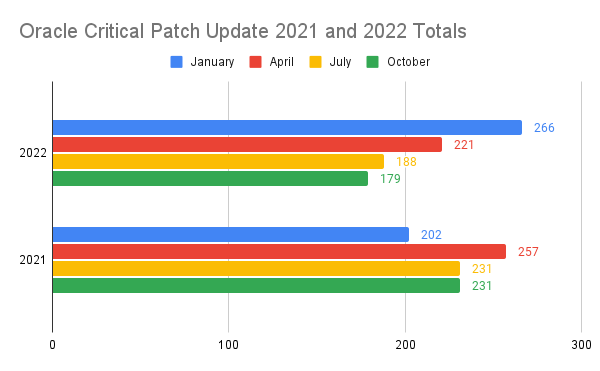
The first two quarters in both 2021 and 2022 saw the most patches released, 487 in 2022 and 459 in 2021. In 2021, Q3 and Q4 had an equal number of patches (231), whereas Q3 and Q4 of 2022 saw a marked decrease in patches (188 and 179 respectively).
Schedule for quarterly patch updates for 2023
Looking ahead to 2023, Oracle has specified the dates for upcoming Oracle CPUs:
- January 17, 2023
- April 18, 2023
- July 18, 2023
- October 17, 2023
Identifying affected systems
A list of Tenable plugins to identify these vulnerabilities will appear here as they’re released. This link uses a search filter to ensure that all matching plugin coverage will appear as it is released.
Get more information
Join Tenable’s Security Response Team on the Tenable Community.
Learn more about Tenable, the first Cyber Exposure platform for holistic management of your modern attack surface.
Get a free 30-day trial of Tenable.io Vulnerability Management.

