- This iOS 18.4 feature gives robot vacuum users a major connectivity upgrade
- This tablet replaced my Kindle and iPad within hours of testing - and it's on sale
- These XR glasses gave me a 200-inch screen to work with - and they're well worth it
- Government Backs Britain’s First Cyber Seed Fund, Worth £50m
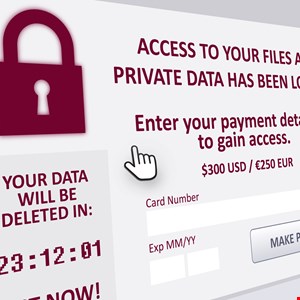
- 8 simple ways to teach your friends and family about cybersecurity - before it's too late
Observe, Engage and Act AIOps with vRealize (Part 1) – Cloud Blog – VMware
The Need for Intelligence In today’s age of mass digital transformation, it’s not always the strongest, or largest businesses that survive and thrive. It’s often the ones who can adapt the quickest to the change in markets. If you were running a bricks-and-mortar only store pre-COVID, when lock-down hit, you needed to either adopt technology very quickly, or risk obsolescence. It didn’t matter if you were large and established or not. Not even your most loyal customers could wait for you, they had to go elsewhere. This is happening in every industry and even goes beyond COVID. Agility and speed are…
Read More