- 2025 Cyber Security Predictions: Navigating the Ever-Evolving Threat Landscape
- Not Just Another List of Top 10 Metrics You Should Measure
- My new favorite headphones for swimming come bundled in a unique charging accessory
- Why I recommend this Windows laptop to creatives and professionals - even if it's meant for gamers
- This HP laptop may be the closest thing to a MacBook Pro for Windows users - and I don't mind it
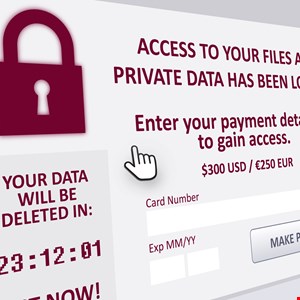
Apple releases emergency patch to protect all devices against Pegasus spyware
Designed to combat zero-day flaws exploited in Apple’s operating systems, the patch applies to the iPhone, iPad, Apple Watch and Mac. Image: Apple Apple has pushed out an update for most of its major products to protect them from a strain of spyware that has already targeted a number of people. On Tuesday, the company rolled out the emergency patch to squash a bug that impacted the iMessage app built into iOS, iPadOS, watchOS and…
Read More