- You can buy the newest iPad Mini model for $100 off on Amazon - and I highly recommend it
- These are my 16 favorite Memorial Day lawn and outdoor deals right now
- These are the Memorial Day headphones deals I recommend most to family and friends
- 4 gadgets I'm bringing to the beach this summer - and why they make such a big difference
- I'm a laptop expert and these are the Memorial Day laptop deals I'd scoop up ASAP
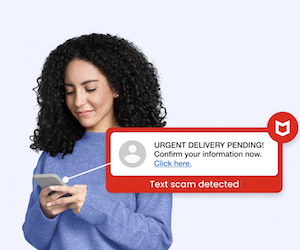
New Fortinet and Ivanti Zero Days Exploited in the Wild
Fortinet and Ivanti have warned customers that attackers are exploiting new zero day vulnerabilities affecting a range of products. The tech firms published separate advisories on the flaws, one of which is critical, on May 13, urging customers to apply fixes as soon as possible. Cybersecurity vendor Fortinet provided details on a stack-based overflow vulnerability, CVE-2025-32756. An exploit can enable a remote unauthenticated attacker to execute arbitrary code or commands via crafted HTTP requests. The…
Read More