- The Apple Watch Ultra 2 is a near-perfect smartwatch and it's $70 off now
- These mainline OnePlus earbuds are a great buy at full price - but now they're $40 off
- These are the Memorial Day sales fitness enthusiasts should pick up
- This tiny 2-in-1 charger solved my biggest problem with traveling - and it's on sale
- Finally, a budget smartwatch that's just as durable as my Garmin (and it's on sale)
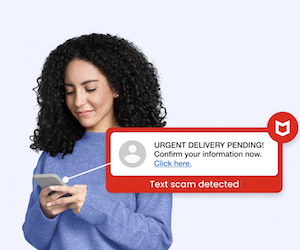
Introducing McAfee's Scam Detector – Now Included in All Core Plans | McAfee Blog
In today’s online world, scams are everywhere—and they’re harder to spot than ever. From sophisticated phishing texts and deepfake videos to emails that look just like messages from your bank or delivery provider, scammers are constantly evolving. And so are we. Introducing McAfee’s Scam Detector: advanced scam detection technology built to spot and stop scams across text messages, emails, and videos. It’s included at no extra cost in all core McAfee plans for customers in…
Read More