Pay2Key hackers stole data from Intel’s Habana Labs – Cyber Defense Magazine

Pay2Key ransomware operators claim to have compromised the network of the Intel-owned chipmaker Habana Labs and have stolen data.
Intel-owned AI chipmaker Habana Labs was hacked by Pay2key ransomware operators who claim to have stolen from the company.
The group announced the hack on Twitter, they claim to have stolen sensitive data, including information about a new artificial intelligence chip code named Gaudi.
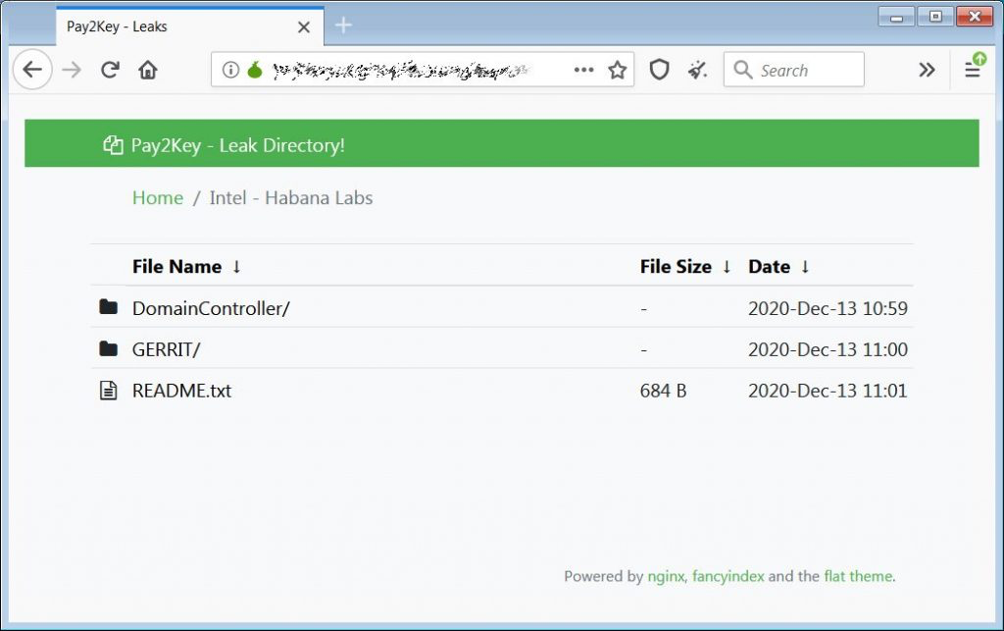
The hacked shared a link to a leak directory and images of the source code and internal processes belonging to the hacked company.
The Pay2Key leak directory includes Windows domain controller data and a file listing from the Gerrit development code review system.
Source Bleeping Computer
“The hackers also claim to have gained access to the company’s Domain Controller, which if true, would indicate they were able to breach all its organizational network. If it is linked to that of Intel, the hackers may have gained access to the American organization too.” reads the post published by Calcalistech.
The Pay2key operators have also blackmailed several Israeli companies throughout November.
At the time of this writing, it is not clear the ransom demands, it is only known that the gang gave to Habana Labs “72hrs to stop leaking process.”
Researchers from Profero speculate that the Pay2Key gang was an Iran-based crew because they used ransom payment wallets operated by Iranian bitcoin exchanges.
This week @_CPResearch_ released an analysis of ransomware targeting Israeli SME dubbed “Pay2Key”. Using intelligence sources and our latest CryptoCurrency monitoring capabilities, we have been able to track the exit strategy of the threat actors leading to Iranian exchange. pic.twitter.com/64WzsonAjQ
— Profero (@ProferoSec) November 11, 2020