- Better Together: How MFA and Strong Password Practices Can Help Bolster Security
- “美 CISO 평균 연봉 6억,상위 1%는 60억원 넘어···보안 예산은 여전히 부족” IANS 설문조사
- 아웃시스템즈, 매출 5억 유로 돌파 및 신임 CEO 선임 발표
- 정철환 칼럼 | 변화의 바람에 맞설 것인가? 따를 것인가?
- Best home automation systems 2025: I'm a smart home reviewer and these are the top ones
“Payzero” Scams and The Evolution of Asset Theft in Web3

Cyber Threats
In this entry, we discuss a Web3 fraud scenario where scammers target potential victims via fake smart contracts, and then take over their digital assets, such as NFT tokens, without paying. We named this scam “Payzero”.
Read time: ( words)
Web3 is a lucrative emerging technology where many participants seek quick profit via the different methods of monetization for their online assets. What makes Web3 different from what’s typically called Web2 is that its users are not only participants but are also the owners of digital assets. Web3 users no longer employ the traditional user and password method for authentication. Instead, the user owns a pair of cryptographic keys and sign the messages. The signature is then used to validate and authenticate user actions.
Compared to Web2, this adds a new layer of complexity as the new paradigm and authentication mechanism can be challenging to comprehend. In Web2, users can employ usernames and passwords for authentication with large online service providers. These companies can then cover the authentication process against third party applications, leaving users to be responsible for remembering the usernames and passwords they use for these service providers.
In Web3, the most import credential — the private key of the wallet address —is owned by the user. Users must handle these authentication scenarios on their own, which can be a complicated process, especially for newcomers. Figure 1 shows a comparison between Web2 and Web3 from an authentication standpoint.
It is difficult, or even nearly impossible for users to remember their cryptographic key, so seed phrases, which are somewhat easier to remember or write down accurately, are used to backup and recreate cryptographic keys.
What exactly are seed phrases? Seed phrases are typically a human-readable sequence of words that could be remembered or written down. Since cryptographic keys are difficult to remember, these seed phrases are used to recover the keys. There is even a saying in world of cryptocurrency — “not your keys, not your coins”, referring to the risks of custodial wallets (which are when private keys are managed by a third party). Seed phrases are as important as the keys themselves because they are sufficient enough to create a copy of the keys.
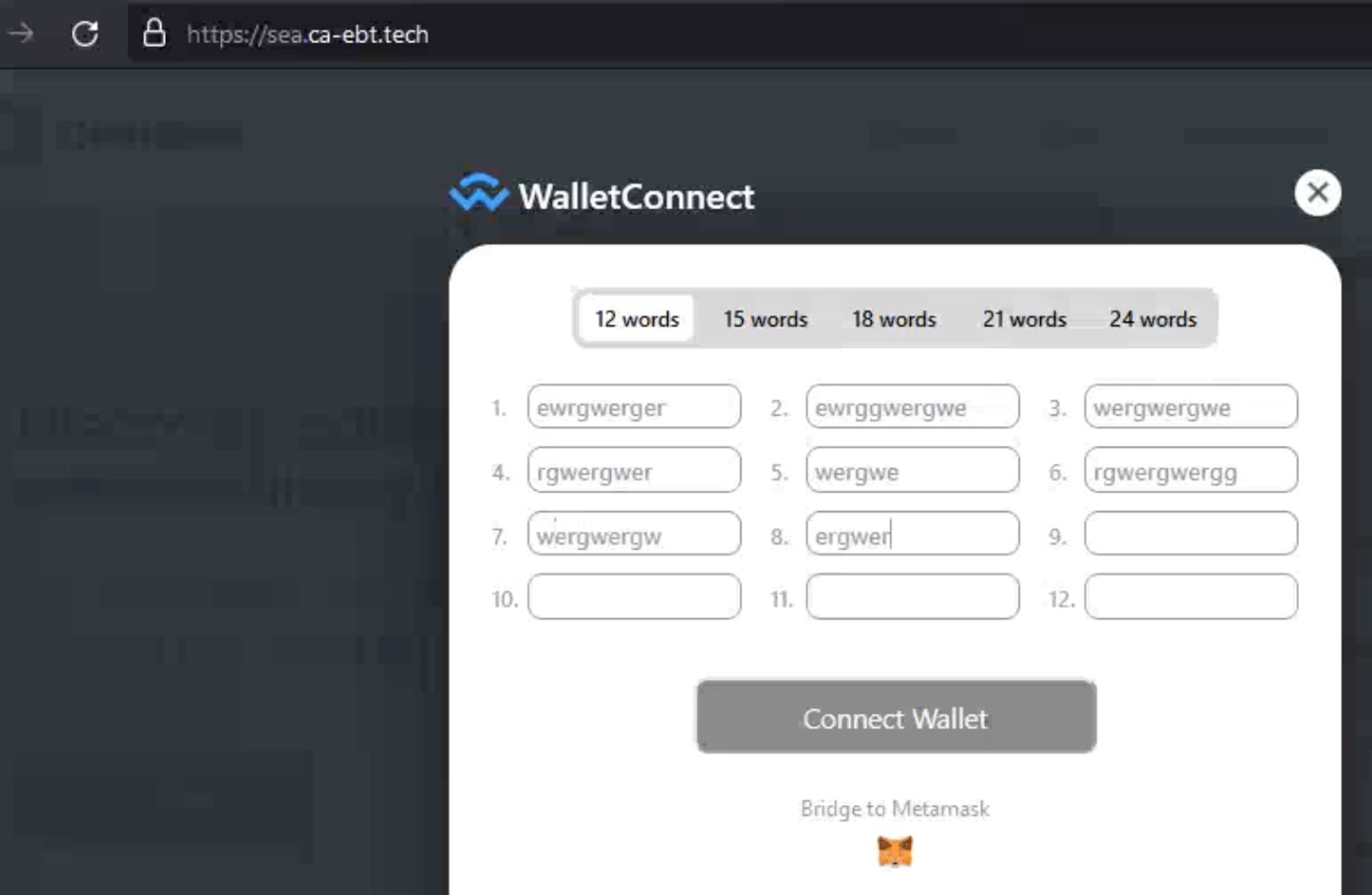
However, as with any new technology, its complexity may lead to several hidden traps. For example, phishing for seed phrases by providing fake WalletConnect interfaces have become very widespread. There are several scam schemes that have evolved around seed phrase manipulation. A basic example is the theft of wallets via seed phrase phishing or collection. Other examples include using multisignature wallets, wherein malicious actors post seed phrases on forums asking users for help. These seed phrases will act as a trap for online users, who naively think that they can simply take over the wallet of the poster by using those phrases. While they may try to wire money into this wallet for testing purposes, only the original owner of the multiple (thus multisignature) keys is able to control funds and wire money out, therefore trapping these “testing funds” inside the wallet.
The diversity and complexity of abuse in Web3 is significant, and as cybercriminals rapidly adapt to the fast-paced Web3 technology, defenders must keep up with evolving abuse scenarios.
In this entry we would like to discuss a Web3 fraud scenario where scammers target potential victims via fake smart contracts, and then take over their digital assets, such as NFT tokens, without paying. We named this scam “Payzero”.
In essence, Payzero is a fraudulent scheme where the attackers typically pay nothing to the victim for their digital assets and simply trick them into allowing the transfer of token ownership. Some variants of this scheme were already discussed in our previous publication but the volume of activity and associated monetary loss makes us believe that this needs to be explored further. We used datamining techniques to understand the scale of this growing problem.
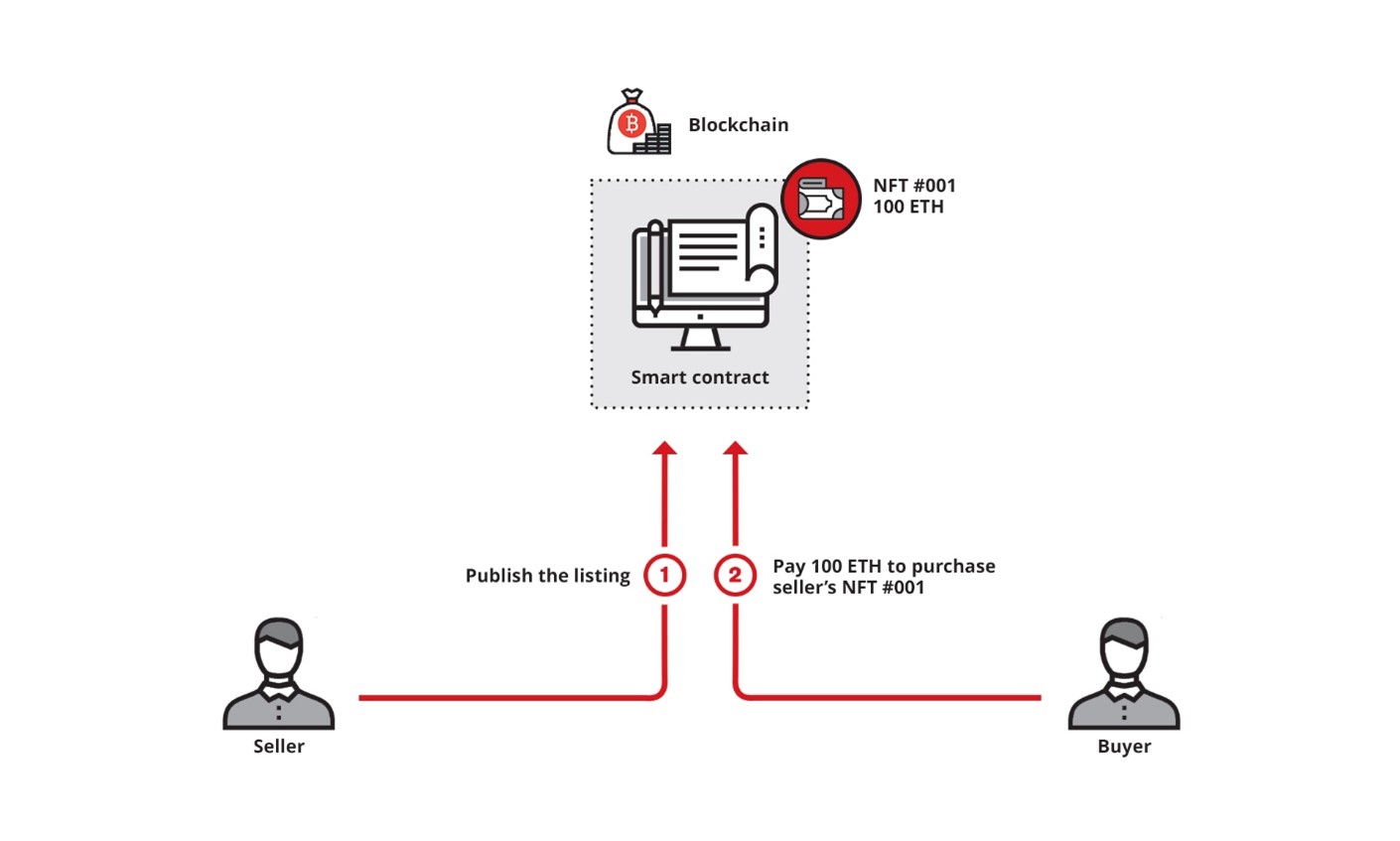
Before examining its scale, let’s look at a typical Payzero scam scenario. This involves several actors, with Figure 3 illustrating a simple example of this.
- A buyer: the scammer who intends to take over the tokens.
- A seller: the potential victim.
- A new token owner: it can either be the buyer or a third party designated by the scammer.
- A token: An NFT token. It can be any ERC721, ERC1155 and ERC20 token. One scam event can lead to the loss of multiple tokens.
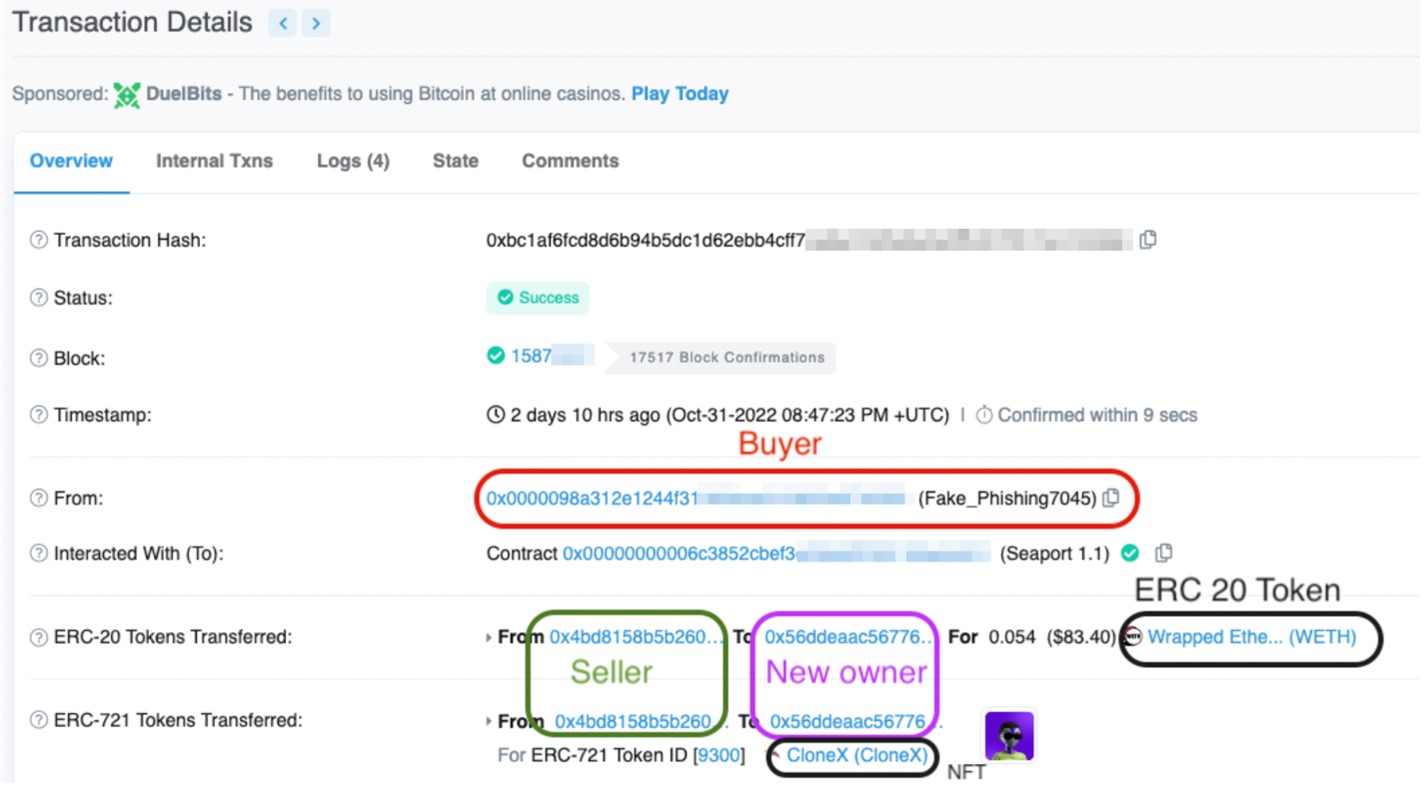
In a normal transaction, a seller places the token for sale in one of the various token marketplaces, such as Opensea. When the seller is approached by a buyer, the transaction takes place via the platform’s smart contract, transferring the funds and ownership of the token to the new owner.
On-chain vs off-chain marketplaces
With off-chain marketplaces, the owner of the NFT token holds the ownership of the token until the transaction to the owner takes place. Meanwhile, with on-chain marketplaces, the token owner transfers the ownership of the tokens to the marketplace’s smart contract and then trading takes place. The trade-off here is the transaction complexity vs. the cost-benefit on the transaction fees.
Scam Transaction scenarios
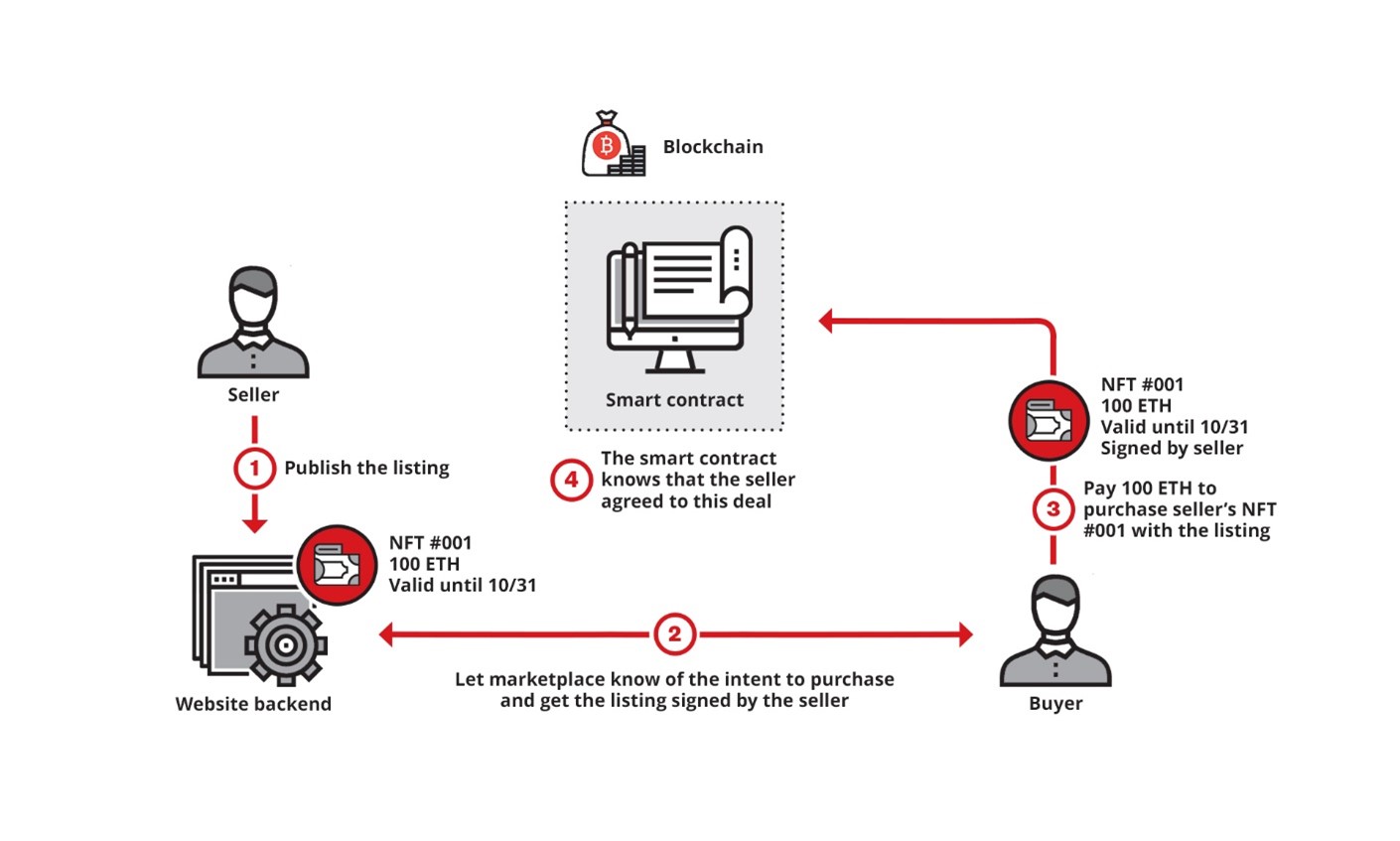
Imagine a scenario where a victim lists his tokens on a markerplace such as Opensea. In the scam transaction scenario, a buyer (the scammer) usually approaches the victim using a social media or communication platform such as Twitter or Discord and asks the seller to sell the tokens to the buyer.
In earlier versions of the scam (known as the “SetApprovalForAll scam), the scammer would propose to conduct a transaction via a third party site. When the victim agrees to the transaction, the scammer can take ownership of the NFT tokens because the victim calls a smart contract API and gives the scammer operation permission.
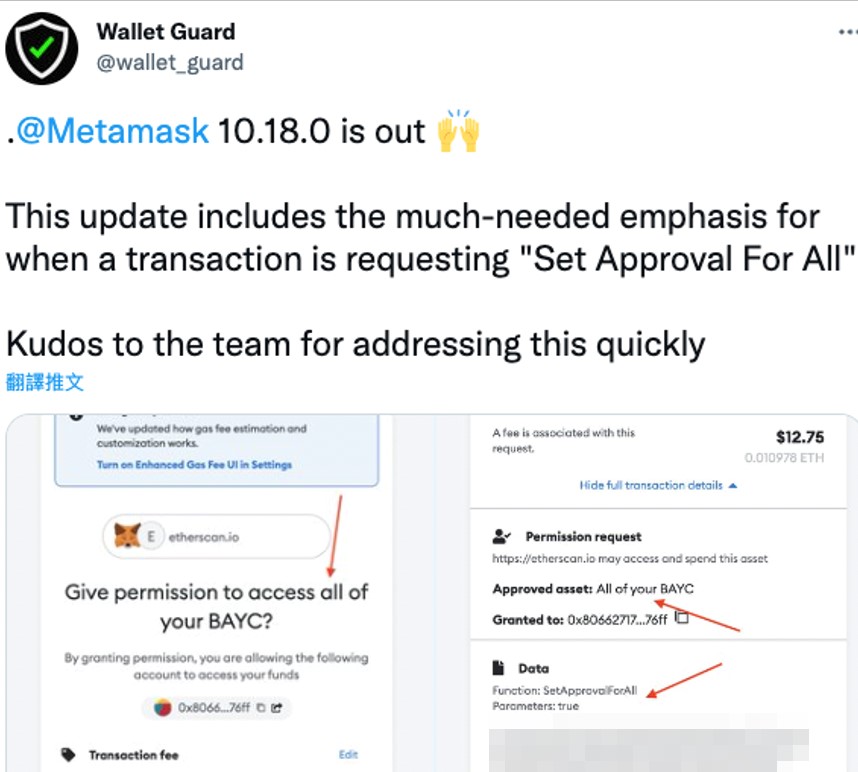
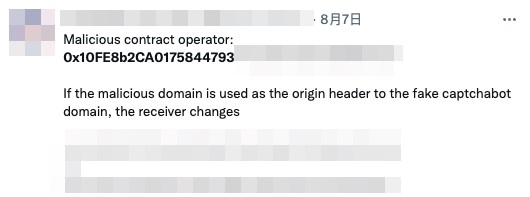
Since this has been happening for a while, many users have grown aware of this scam and have become cautious when they are offered to run transactions via a third party. Some wallets have also implemented measures to address the signature scam problem, as seen in Figure 6.
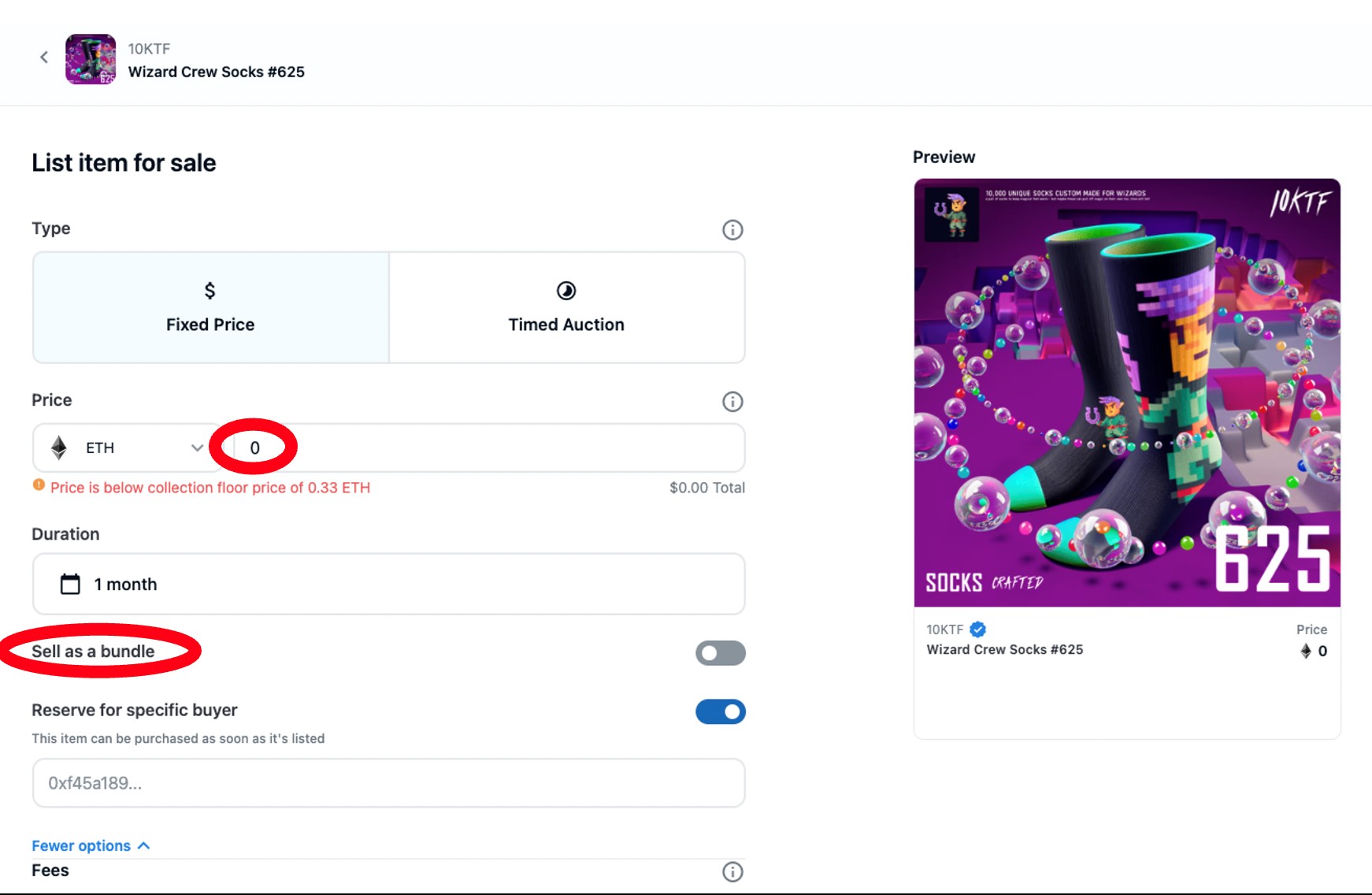
In the Payzero scam, the owner of the digital assets (NFT tokens) simply “agrees” to sell the digital assets to the new owner at zero cost. By agreeing to this transaction, the user will sign off the transfer of token ownership for free.
The scale of the problem
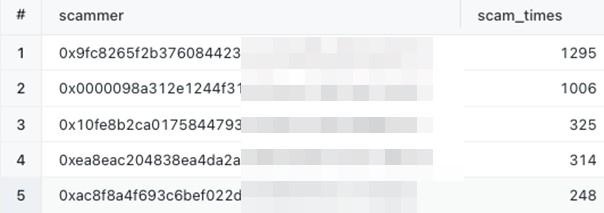
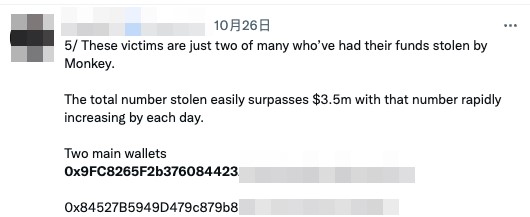
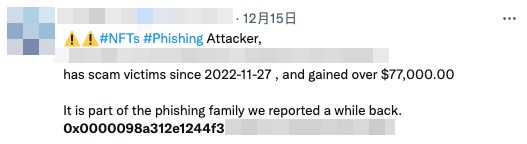
By using a heuristic rule on the blockchain, we were able to record the number of potential token theft incidents from August to December 2022. Figure 8 shows the addresses that have performed the highest number of Payzero scams. We found internet sleuths and victims discussing these scammers on Twitter.
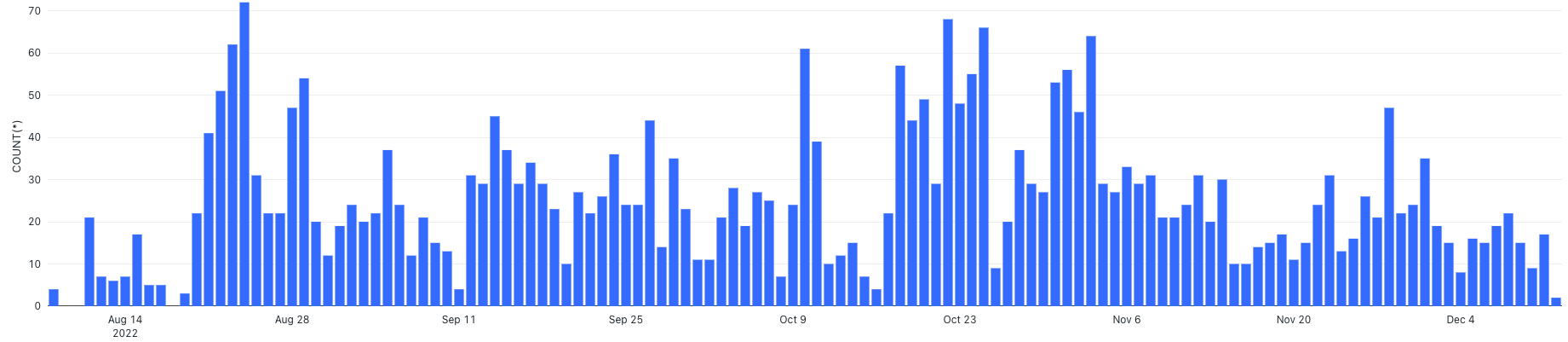
Figure 10 shows the scam events triggered by these five addresses. More than 3,000 Payzero scam events occurred from August to December 2022, with over 5,000 NFTs being involved (with the total price of the NFTs being around 3,000 ETH or approximately US$3.6 million)
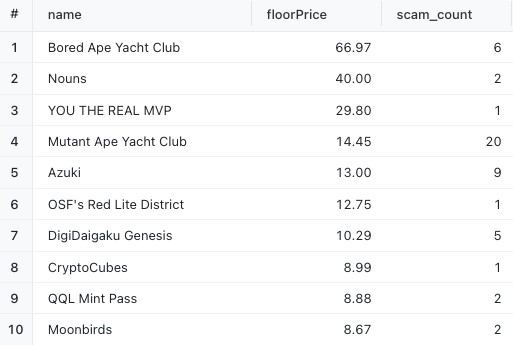
Meanwhile, Figure 11 shows the top ten high-value NFT collections that were involved in these scams and how much was stolen.
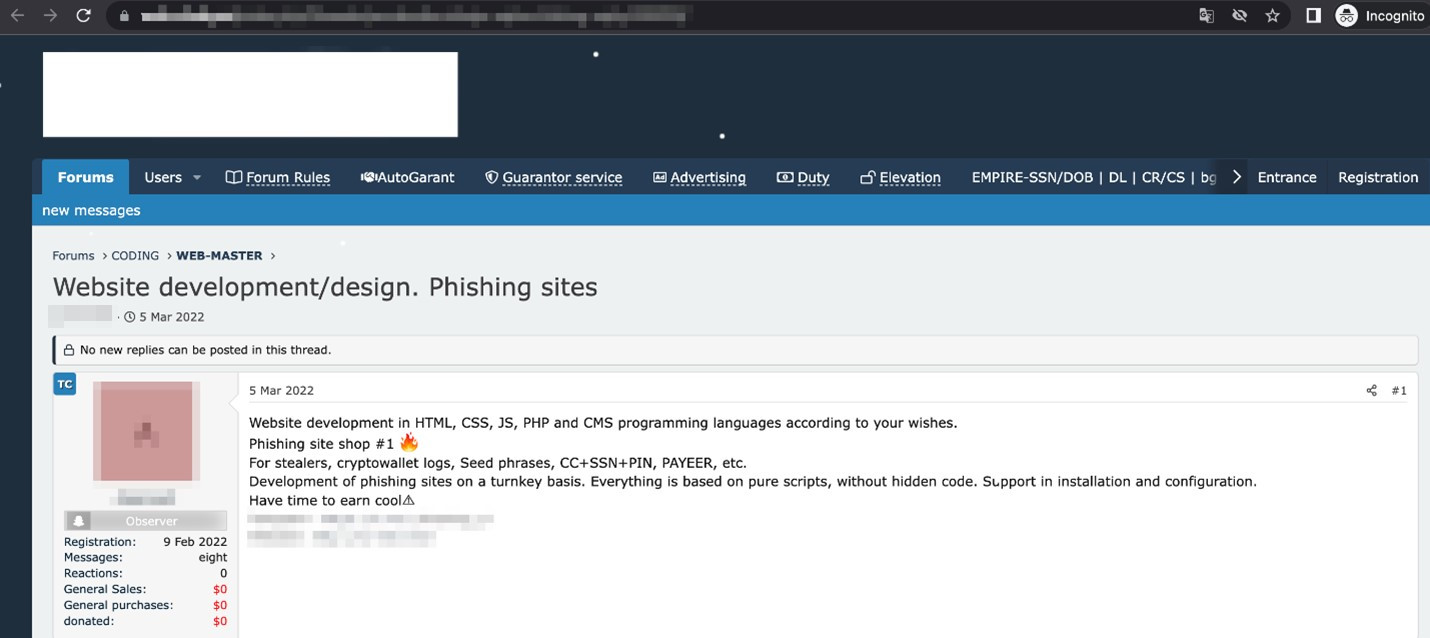
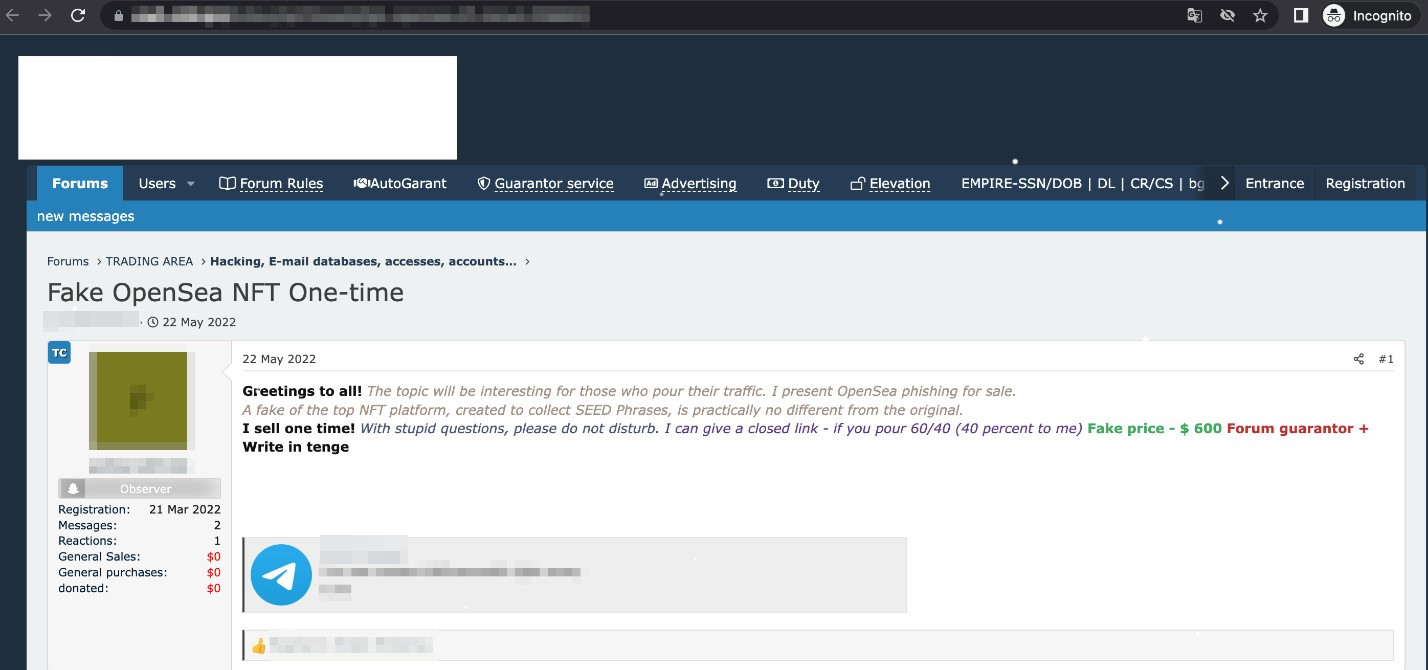
Cybercriminals have been following Web3 trends and have been rapidly adapting to the changes in technology. Many underground forums sell services that can tailor new technologies to the customer’s needs and can even automate nearly every part of the abuse process. Since massive amounts of money are involved, the tools for the theft of cryptographic keys and seed phrases are widely traded in the underground. Furthermore, specific malware variants are being developed to harvest crypto assets.
The underground service offerings, which have been rapidly evolving, offer anything from phishing kits and analysis tools for stolen data designed to search for cryptocurrency assets, to the automated verification of available digital assets.
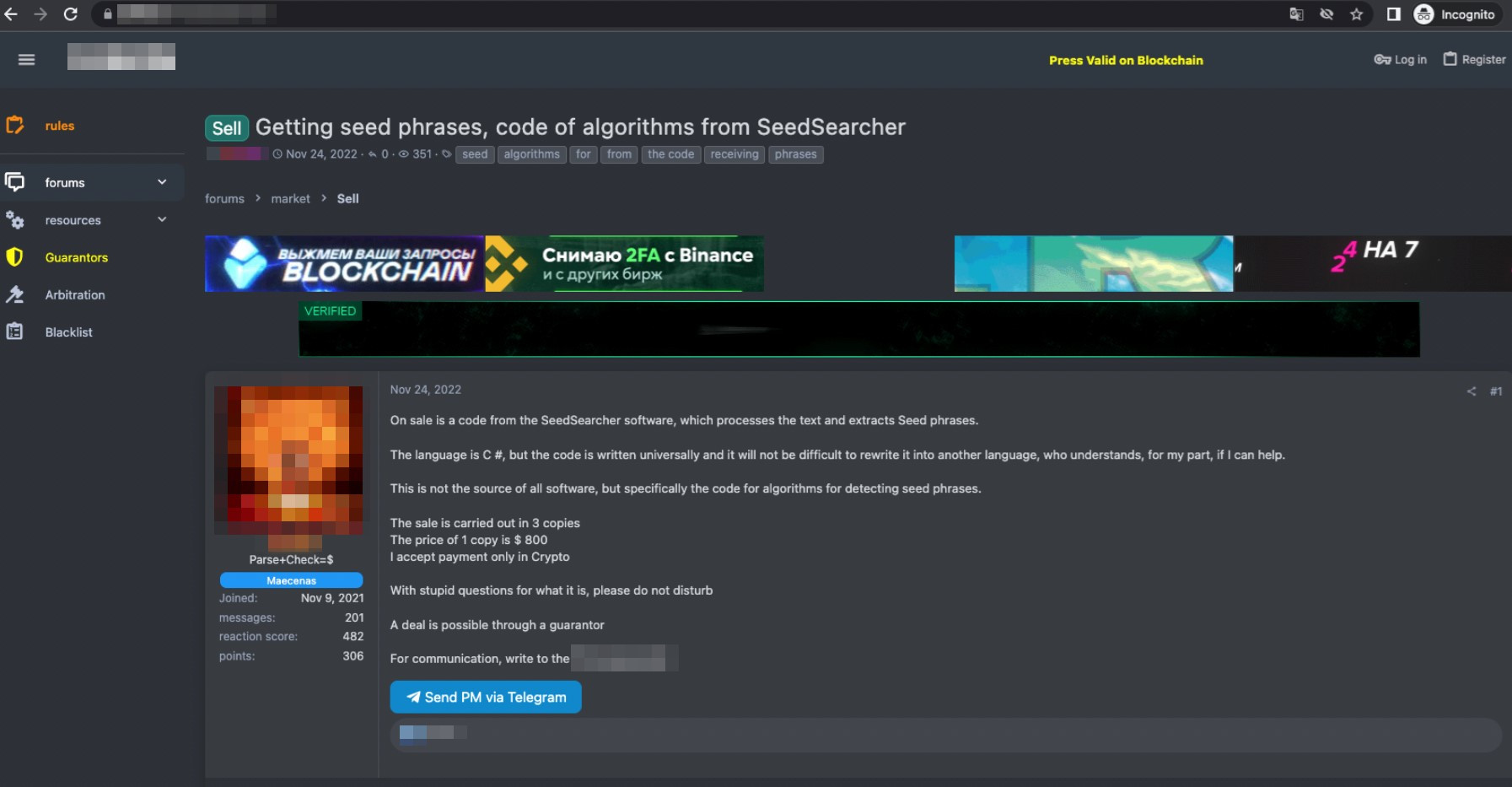
The seed phrases themselves are a tradeable product in underground forums, with many services being structured around the collection or analysis of seed phrases. For example, we found code that is capable of extracting seed phrases from different text sources being sold for US$800.
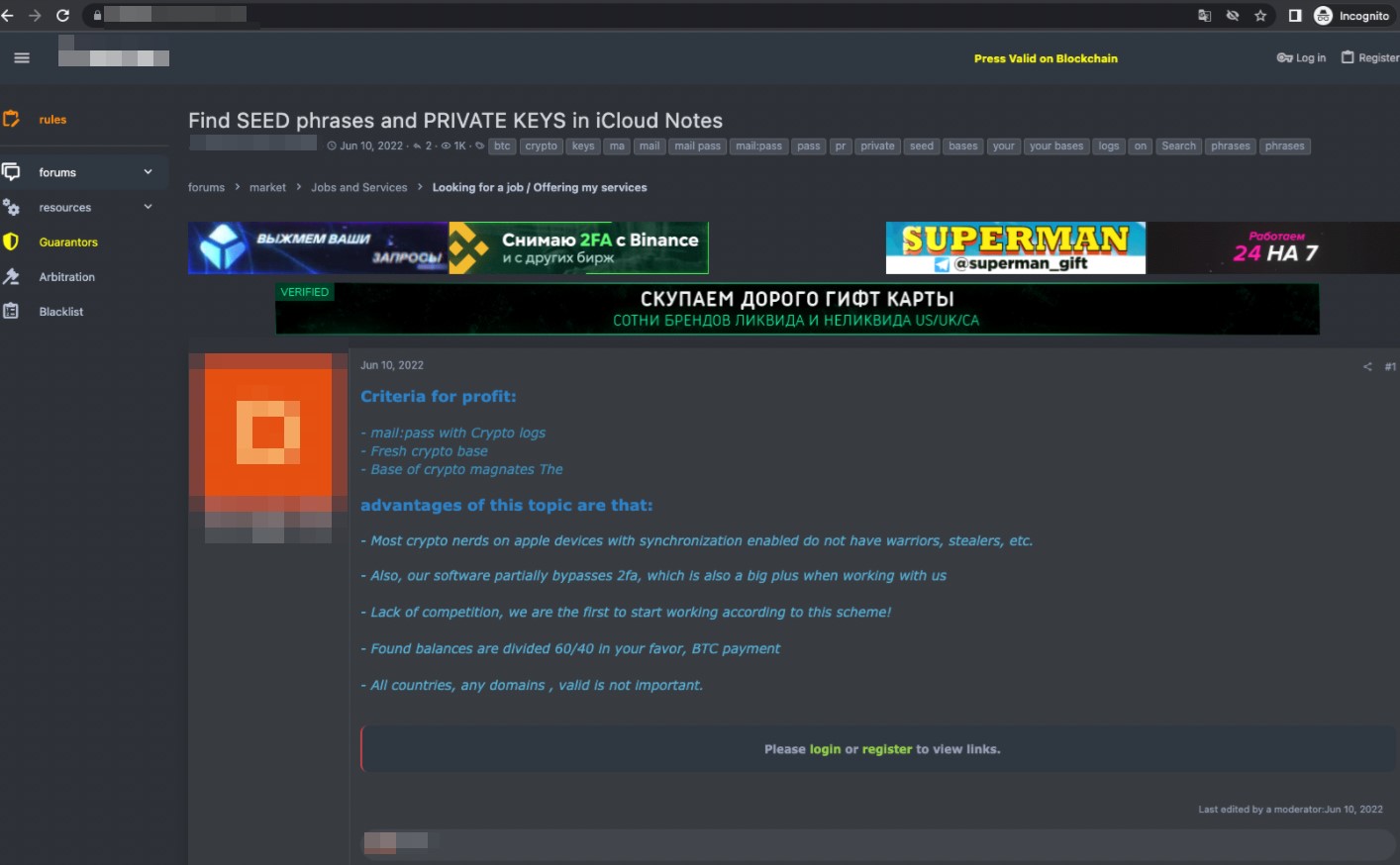
There are also services that provide users the ability to search for seed phrases via the traditional abuse of stolen credentials. This information is then harvested from various apps (for example, from iCloud Notes).
There is even a full-blown service, called Deepchecker, that is tailored to automate the verification of Web3 credentials. This service allows users to check and monitor the wallet balance using the provided seed phrases. It verifies over 1,000 different sources related to cryptocurrency assets.
Users of Web3 technologies must take personal responsibility regarding the security of their assets when they interact with it. It’s very easy to sign off transactions on Web3 —with the downside being that a single sign off without careful validation may lead to catastrophic consequences and significant financial loss.
Scammers often target potential victims by offering off-chain transactions via a third party website, where they can trick users into signing contracts that allow these scammers to take over the digital assets of the victims. Since the SetApprovalForAll permission issue has been technically addressed by the MetaMask wallet, scammers have been employing new methods of tricking users into giving up ownership of their assets, such as the PayZero scheme discussed in this article.
Fortunately, there have been developments to better protect wallets, for example, multisignature wallets (which require two or more signatures to sign the transactions) can potentially minimize the impact of leaked seed phrases. However, it is still important for users to understand that the key risk with Web3 is that in non-custodial wallet ownership, the asset owners are fully responsible for the security of their assets during its full lifecycle unlike in custodial assets where the users do not simply own their assets and are exposed to more traditional risks such as hacking attacks, scams, and even the collapse of the custodial organizations themselves, among others.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk