Penetration Testing- Shielding the Web Content Against Hacking

Penetration Testing Market size worth over $5.5 Bn by 2031
By Aashi Mishra, Sr. Content Writer, Research Nester
In January 2023, a news surfaced the internet that 235 million twitter accounts were leaked in a massive breach. Later, the social media platform hit by a drop of approximately 40% drop in the revenue. This case is alarming and re-establishing the importance of shielding the businesses from the hacking through measures such as penetration testing.
This twitter attack is just the tip of the iceberg and it is estimated that 2023 will witness around 33 billion account breaches. Owing to exponential rise in the hacking cases, there has been escalating number of the bug hunters, penetration tester, and security engineers. Technologies such as penetration testing are extensively used by businesses to save the IT infrastructure. In this blog, we will understand the meaning, types, benefits and various other aspects of the penetration testing.
What is Pen Testing and Why is it Important to Perform?
The process of penetration testing, also called ethical hacking, refers to the imperative security process of assessing applications for susceptibility and vulnerabilities. With the help of penetration testing, a person can eschew the vulnerabilities of bugs or the design flaws.
These pentests are also called white hat attacks as there are benign attempts to break into the system. Nowadays, approximately 77% of the companies use penetration testing as a security testing method to evaluate the security measures.
Furthermore, the average cost of data breach has escalated 2.6% from USD 4.24 million in 2021 to USD 4.35 million in 2022. Hence, the penetration test prepares the organization for an attack or malicious entity. In fact, the penetration testing services that are offered by several penetration testing companies, render solutions which are known to help organizations to not only detect attackers but also debar such intruder. These pen tests render insights into the applications which are at extreme risk. Let us now understand the types and approaches of the physical penetration testing.
Types of Penetration Testing
- Network Penetration Testing
The certified pen tester inspects the network environment and undergoes security testing for the detection of any security vulnerabilities. This process can be further sub divided into 2 main categories:
- External tests: This involves testing of the public IP address
- Internal tests: This gives the tester network access to imitate the hacker
Furthermore, the network testers examine areas such as firewall bypass testing, intrusion prevention system deception, DNS level attacks, etc.
This web application test helps in recognizing the real-world attacks which could get success at accessing the systems. Also, website penetration testing identifies loopholes in the infrastructure before an attacker could harm it. Web application penetration testing focuses on websites, browsers, and web application.
- Client-Side Penetration Testing
This kind of testing is also called internal testing in which the certified penetration tester exploits the probable vulnerabilities in email clients, macromedia flash and other client-side application. Furthermore, on the client side, cyber security testing is performed to identify cyber-attacks including-
- Clickjacking attacks
- Cross site scripting attacks
- HTML Hijacking
- Open redirection
- Wireless Network Penetration Testing
The wireless network penetration test helps in identifying weaknesses in the wireless infrastructure which involves the following parameters-
- Recognizing vulnerabilities in the wireless infrastructure
- Safely using the identified vulnerabilities
- Fabricating the report which incorporates a list of various issues, risk and remedies.
- Social Engineering Penetration Testing
Social engineering attacks like phishing, vishing, smishing, impersonation, dumpster diving, USB drops, tailgating, etc. are threat to internet connectivity. It consists of the ethical hackers who conducts myriad of social engineering attacks. The goal of these tests is to recognize the threat and render proper remediation.
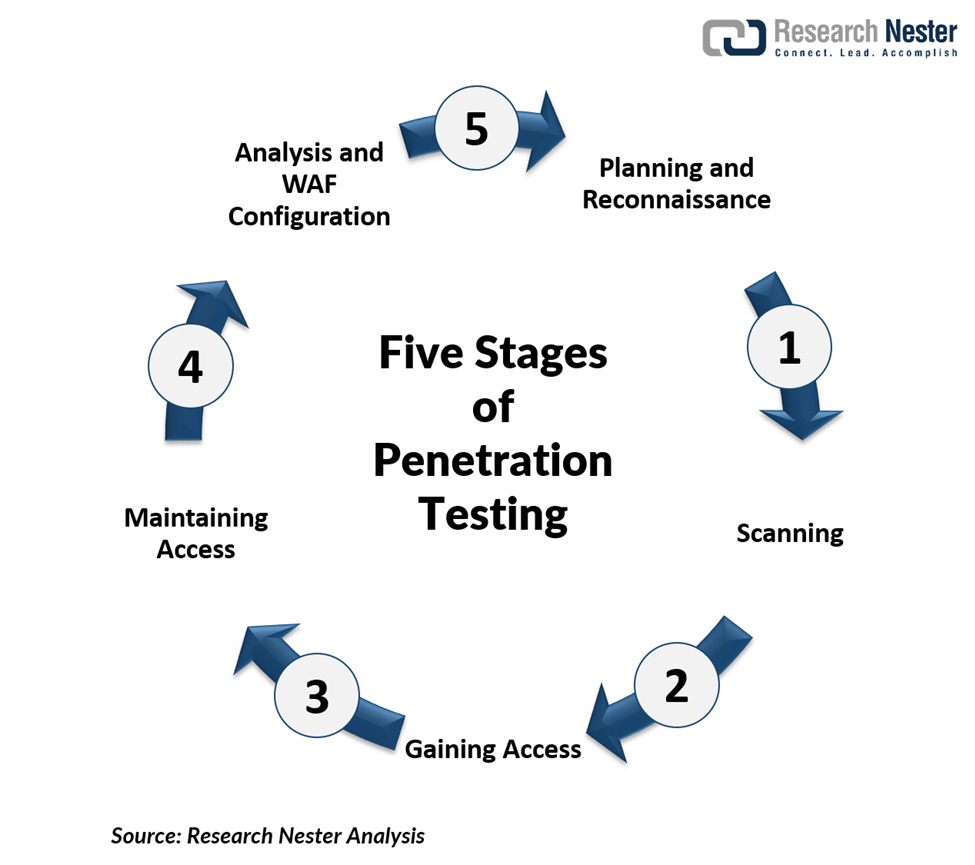
These kinds of tests are adequate for making the application system robust and shielded from attacks. The tests are executed in the following stages-
- Planning & reconnaissance
In this stage, test goals are defined and intelligence is gathered.
- Scanning
The scanning tools are utilized to understand how the target reverts to intrusions
- Gaining access
Web applications attacks are staged to reveal a target’s vulnerabilities
- Maintaining access
APTs are emulated to witness if a vulnerability can be utilized to maintain access
- Analysis & WAF configuration
The obtained results are utilized to configure WAF settings before testing runs again
It might sound absurd to hire a hacker to exploit your IT infrastructure but to protect the IT infrastructure penetration testing has now become an imperative tool.
Advantages of Penetration Testing
The process of physical penetration testing poses numerous advantages which are mentioned below-
- Getting a New Insight into Security System
The pen testing method renders unseen insights into the IT infrastructure by exploiting the hidden flaws and loopholes. Also, it is crucial for fabricating accurate report analysis and efficiently revamp the system. The pen testing allows an in-depth analysis of the IT infrastructure.
- Reveal the Hackers’ Methods
The primary goal implementing the pen testing is to imitate real attacks on the systems. After analyzing vulnerabilities, hackers exploit the applications to identify the parts which needs improvement.
- Protection from Financial Damage
A single breach of the security in any company lead to millions of dollars of loss. Penetration testing is extremely crucial for business as it render an efficient approach to combat cyber security issues. There is also reputational risk attached with the data breach.
A recent report published by Forbes found that 46% organization suffered massive reputational damage as the consequence of the data breach. This reputational damage also causes economical damage to the organization. A proper penetration testing leads to strengthening of customer loyalty and trust in the business.
- Compliance With Regulation and Security Certification
The IT departments address the auditing and compliance procedures such as HIPAA, PCI DSS, SARBANES, GLBA. The overall records of the pen tests can help in eluding the penalties for the non-compliance. The pen tests also allow the user to demonstrate current due diligence by sustaining the required security controls.
- Provides a Cyber Chain Map
The penetration test imitates the real hack where the user is able to see the direction a hacker might go through the system. This movement is usually known as the lateral movement. If the tester is conducting penetration test, he or she will be able to map full route through the security of system.
The procedure also gives a full map of how various connections are made amongst the layers in the system itself.
Also, sometimes penetration testing is confused for the same kind of service. Let us dive a little deeper into the difference between vulnerability scan and penetration scan.
Penetration Testing vs Vulnerability Assessment
- Penetration Testing – The penetration testing copies the actions of an internal or external cyber-attack which are intended to break the information security. It utilizes the advanced tools and techniques by making an effort to control critical systems.
- Vulnerability Assessment – It is the technique to discover and measure security vulnerability in the given environment. It identifies the probable weaknesses and provides impeccable mitigation measures.
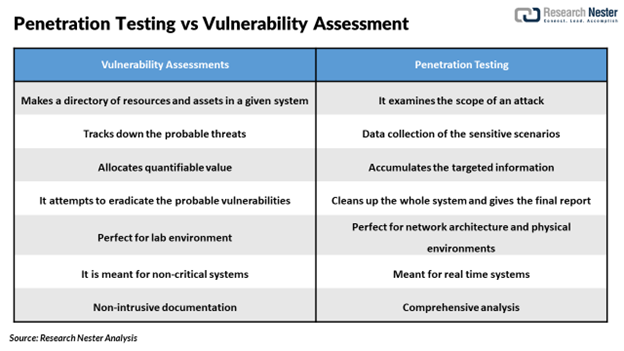
Both vulnerability assessments and penetration testing have different approach and functionality. Researchers suggest that both the techniques should be extensively used as security management systems and should be performed on regular basis.
What is Penetration Testing Quizlet?
The penetration testing quizlet will be giving ideas about the terminologies involved in the technologies such as passive reconnaissance, active reconnaissance, box testing, black box testing, gray box testing, etc.
Although, online penetration testing can be done by an expert pen tester in an efficient way to secure the IT infrastructure.
Why is it Important to Continuously Conduct Penetration Testing for a Strong Security System?
In order to shield the IT infrastructure, penetration testing has become the need of hour. According to Research Nester analysis, when pentest were performed for the repeat clients, the data came out to be like this-
- 1% of the targets had at least 1 critical vulnerability
- 9% had 1 or more important vulnerability
- 1% had medium, critical or important vulnerability
- 47% had 1 or more medium vulnerability
The data occupied of the pen testing is the testimony that there is a requirement of frequent testing to secure IT infrastructure.
Penetration testing should be performed at least once a year to ensure a robust IT and network security management. Although, the test frequency hugely depends in how alluring the business is for the hackers. Owing to the threats posed by malicious players there is a need to perform regular pen testing.
How can Businesses be Benefitted from Penetration Testing?
We have already read that data breach and malicious attacks can hamper the company in economic terms also. A prominent pen testing company, Tenendo claims that it has capability of reducing high vulnerability exposure by up to 97%. Let us see through a case study where Tenendo has resolved the challenge.
- What was the challenge which company was facing?
The Tenendo team was given task to execute an external black box engagement of a banking institution. The task was to perform without any restriction on the access. The test was conducted when there was no prior information was given. The only information given was rules of engagement and customer name.
- What was the solution to it?
The whole procedure had various constraints, but the team was able to intrude into personal information, achieve persistent internal access, and fabricate internal attack scenarios.
The second case handled by the Tenendo specialists was payment processing API penetration testing.
- What was the challenge which company was facing?
The team was given a task using external penetration test. The process was to done on an undisclosed payment processing company.
- What was the solution to it?
Tenendo specialists were able to discover an unattended staging environment. The team achieved complete compromise of the of the transaction processing API.
The case studies show that physical penetration testing can avoid attacks and probable threat to the company. Let us now see, how the penetration testing holds major importance in the future.
Future Scope of Penetration Testing
The pentesting amalgamated with the artificial intelligence is able to make impactful results in the future. Also, certified pen testers will be in demand for their knowledge and experience to decide the best course of action to perform assessment.
According to Research Nester analysis, in the future, the global penetration testing market is anticipated to grow with a CAGR of 14.9% from 2022 to 2031, and it is expected that its market size would increase from USD 1395.6 Million in 2021 to USD 5537.0 Million in 2031.
In a nutshell
From the above discussion, we can conclude that penetration testing has already become an imperative part of businesses. In future, as the threat of cyber-attack on businesses is rising, the need for testing is also becoming crucial. Almost, 2 in 3 businesses have online presence which equates to around 24 million online shops all across the world. The types of crimes that businesses could fall victim to are exponentially rising and penetration testing is no less than a silver bullet to shield the business.
About the Author
 Aashi Mishra – Sr. Content Writer. An experienced research writer, strategist, and marketer with a demonstrated history of research in a myriad of industries. I love to distill complex industrial terminologies of market space into simpler terms. https://www.researchnester.com/.
Aashi Mishra – Sr. Content Writer. An experienced research writer, strategist, and marketer with a demonstrated history of research in a myriad of industries. I love to distill complex industrial terminologies of market space into simpler terms. https://www.researchnester.com/.

