- How global threat actors are weaponizing AI now, according to OpenAI
- The viral Air Purifier Table is my smart home's MVP (and it's on sale for $179)
- Grab the Galaxy S25 Edge for $170 off and get a free Amazon gift card - but act fast
- How I learned to stop worrying and love my health tracker
- I found a free iPhone 16 deal that doesn't require a trade-in (and applies to Pro models, too)
Phishing attacks target Chase Bank customers

Two email campaigns discovered by Armorblox impersonated Chase in an attempt to steal login credentials.
Image: Tim Clayton/Corbis Sport/Getty Images
Have you ever received an email apparently from your bank claiming that there was something wrong with your account? Even those of us savvy enough to watch for malicious messages and scams may pause for a moment, concerned that this warning just might be legitimate. And that’s when criminals hope you’ll take the bait.
SEE: Social engineering: A cheat sheet for business professionals (free PDF) (TechRepublic)
In a new report released Tuesday, email security provider Armorblox looked at two recent phishing campaigns aimed at Chase Bank customers and offered advice on how to protect yourself from such scams.
The first campaign claimed to include a credit card statement, while the second warned recipients that their account access had been restricted to unusual activity. In both cases, the goal was the same: obtain your account credentials.
Spoofed Chase credit card statement
In this attack, the spoofed email used a subject of “Your Credit Card Statement Is Ready” and a sender name of “Jp Morgan Chase.” The message itself adopted a look and layout similar to actual emails from Chase and included links to view your statement and to make payments. Clicking the primary link in the email took you to a spoofed Chase login portal that asked you to enter your bank account credentials, which the cybercriminals then naturally captured.
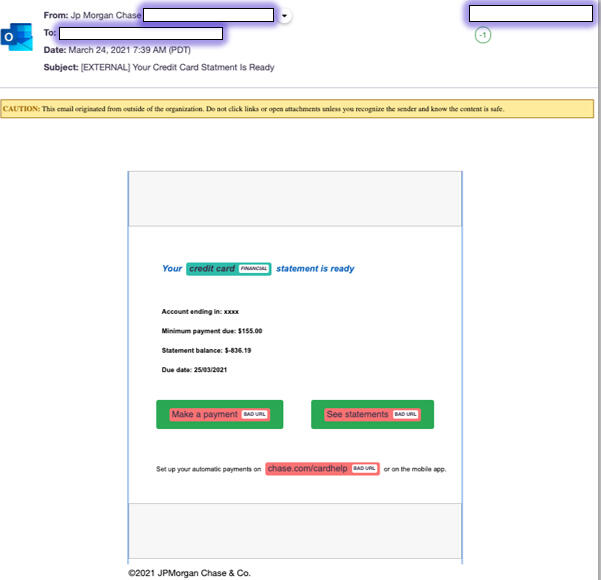
Image: Armorblox
The domain used for the landing page was hosted by NameSilo, a legitimate hosting company but one where cybercriminals can easily and cheaply set up shop to launch their malicious campaigns. The emails bypassed spam filtering from Microsoft Exchange Online Protection and Microsoft Defender for Office 365 after being assigned a Spam Confidence Level of -1. That grade is based on an analysis that the email came from a safe sender, was sent to a safe recipient or originated from an email server on the IP Allow list.
Spoofed Chase locked account workflow
In this campaign, the attackers impersonated the Chase fraud department and told recipients that their account access had been restricted due to unusual login activity. With a subject line of “URGENT: Unusual sign-in activity,” the emails used a sender name of “Chase Bank Customer Care.” The message itself contained a link for potential victims to click to confirm their account and restore normal access. Naturally, clicking the link takes the user to a landing page that asks for their login credentials.
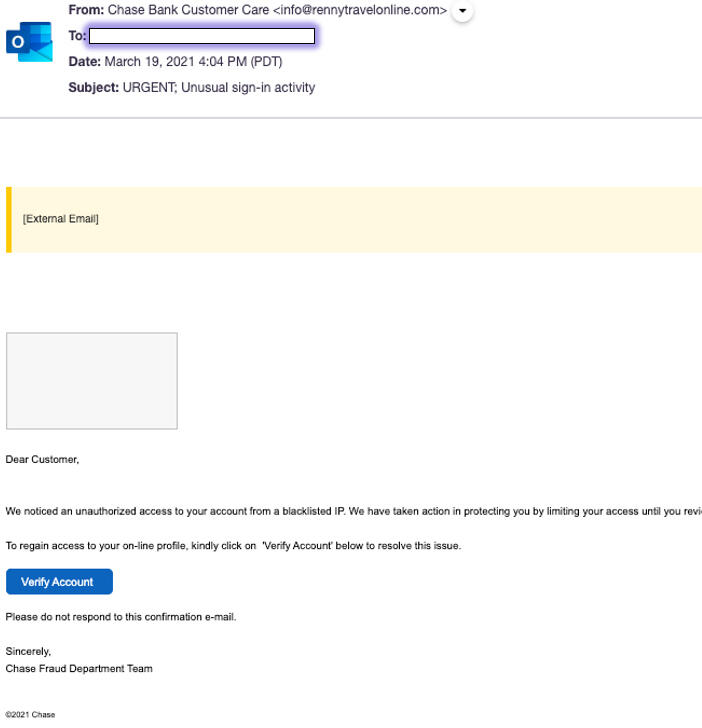
Image: Armorblox
This email also earned a Spam Confidence Level of -1 from Microsoft Exchange Online Protection and Microsoft Defender for Office 365, so it was able to reach the inboxes of users without any warning signs.
In these types of campaigns, cybercriminals employ a variety of tricks and tactics to fool unsuspecting victims.
Social engineering is key to a successful attack as smart cybercriminals know how to push the right buttons. The email subject lines, sender names and content all convey a sense of trust as well as a sense of urgency, prompting recipients to take quick action. Brand impersonation is another key factor. These types of emails adopt the same branding, style and layout found in legitimate messages and webpages from Chase.
How to protect yourself from these scams
To protect yourself and your organization from these types of phishing attacks, Armorblox offers a few tips.
- Strengthen native email security with additional controls. Both emails slipped past Microsoft’s own security tools, indicating that another level of protection is needed. Organizations should enhance their native email security with layers that take a different approach to threat detection. Gartner’s Market Guide for Email Security covers new security methods that surfaced in 2020.
- Look for for social engineering cues. We receive so many messages from service providers that we tend to act without carefully scrutinizing the message. The goal is to scan these emails in a more methodical and detailed way. Inspect the sender name, the sender email address and the language within the email. Look for inconsistencies in the email that trigger such questions as “Why is my bank sending emails to my work account” and “Why is the URL’s parent domain different from chase.com?”
- Follow best practices for passwords and multi-factor authentication. Consider the following practices if you haven’t already established them: 1) Use multi-factor authentication on all business and personal accounts where available; 2) Don’t use the same password across multiple sites or accounts; 3) Use a password manager to handle your passwords; 4) Don’t use passwords associated with your date of birth, anniversary date or other public information; and 5) Don’t repeat passwords across accounts or use generic passwords such as “password,” “qwerty” or “12345.”


