- Sony will give you a free 55-inch 4K TV right now - but this is the last day to qualify
- I've used virtually every Linux distro, but this one has a fresh perspective
- I replaced my JBL speaker with this surprise alternative. Here's why it's my new top pick
- I replaced my JBL speaker with this surprise alternative. Here's why it's my new top pick
- Every dad should build their toolkit with theses 10 DIY gadgets
Preventing Ransomware Attacks On Industrial Networks

By Michael Yehoshua, VP Marketing, SCADAfence
Ransomware Works
That’s the simplest way to explain why incidents of ransomware attacks have been growing steadily for the past two years — with no end in sight. The number of ransomware attacks has jumped by 350 percent since 2018, the average ransom payment increased by more than 100 percent, downtime is up by 200 percent and the average cost per incident is on the rise, according to a recent report from PurpleSec.
Threat actor groups with names such as Ryuk, Egregor, Conti, Ragnar Locker, and many others are ruthless, well-funded, and are willing to target anyone; from COVID-19 vaccine manufacturers, automotive manufacturers, critical infrastructure, governments, and hospitals to get their payday. In fact, the first ransomware-related death happened this past September, when a German hospital was infected with ransomware and couldn’t treat patients during the Covid-19 outbreak.
As part of SCADAfence’s mission to protect the lives and safety of civilians, we’ve put together this guide to help you prevent ransomware in your industrial organization.
The Ransomware Encryption Process
Let’s go back to the beginning, and discuss how these attacks encrypt systems in the first place.
From the previous ransomware attacks we’ve researched, we learned that from the minute the attackers get initial access, they can encrypt the entire network in a matter of hours. In other cases, attackers would spend more time in assessing which assets they want to encrypt and they’d make sure they get to key servers such as storage and application servers.
Most of the recent ransomware attacks you’re reading about in the news try to terminate antivirus processes to make sure that their encryption process will go uninterrupted. Recent ransomware variants such as SNAKE, DoppelPaymer, and LockerGoga even went further by terminating OT-related processes like Siemens SIMATIC WinCC, Beckhoff TwinCAT, Kepware KEPServerEX, and the OPC communications protocol. This made sure the industrial process was interrupted, and this increased the chances that the victims paid the ransom. These types of ransomware attacks were seen in the recent attacks of Honda and ExecuPharm.
Diagram #1 – An OT Security Challenge: Industrial Components Exposed to Encryption
From what we’ve seen, ransomware generally encrypts Windows and Linux machines. We still haven’t seen any PLCs being encrypted. However, many industrial services are run on Windows / Linux machines – such as historians, HMIs, storage, application servers, management portals, and OPC client/servers.
In many cases, ransomware operations would not stop in the IT network, and will also attack OT segments. More encrypted devices mean a higher monetary ransom demand from the attackers.
Organizations must be able to monitor & detect threats across the IT/OT boundary to effectively identify risks before reaching process-critical endpoints.
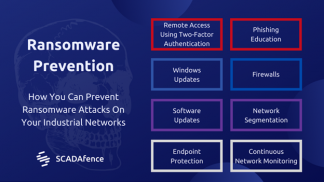
Diagram #2 – Ransomware Prevention: How You Can Prevent Ransomware Attacks On Your Industrial Networks
Some of the tools and techniques that ransomware operators are using are on the same level that nation-state threat actors are using on targeted espionage campaigns.
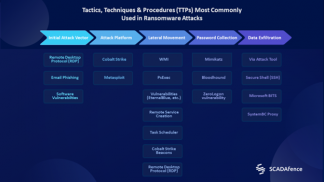
Diagram #3 – Tactics, Techniques & Procedures Most Commonly Used in Ransomware Attacks
We recommend that organizations practice these common security procedures to minimize their risk of ransomware infection on each step of the kill chain:
Initial Access:
- RDP
- If possible, replace RDP with a remote access solution that requires two-factor authentication; many VPNs now support that. This will require attackers to be verified by, for example, a code sent via SMS.
- If you choose to still use RDP, make sure its Windows Update is enabled and is working.
- Email Phishing
- Educate the organization’s employees about phishing attacks. Employees should be suspicious of emails that don’t seem right and not click on suspicious links.
- Install an anti-phishing solution.
- Software Vulnerabilities of Internet-Facing Servers
- Scan your organization’s IP range from outside the network. Verify that all exposed IP/ports are what you expect them to be.
- Make sure that automatic security updates are enabled for your exposed services. If one of your services (such as web servers, for example) does not have that feature, consider changing it to a similar one that has this feature.
Lateral Movement:
- Firewalls & Windows Update
Enable firewalls on all of your workstations and servers.
Make sure that Windows Update is enabled. This will ensure that your machines will be patched for the latest vulnerabilities and will also be less prone to lateral movement techniques. Microsoft constantly updates their security policies and their firewall rules.
One good example is that they disabled the remote creation of processes using the task scheduler ‘at’ command. - Endpoint Protection
Endpoint protection works. Beyond blocking classic hackers’ techniques, some also have defenses against ransomware and will protect your assets from encryption.
- Network Segmentation
Ideally, you would want to minimize the risk of your industrial network being impacted when suffering a ransomware attack.
- To the possible extent, separate the IT network from the OT network segment. Monitor and limit the access between the segments.
- Use different management servers to the OT and IT networks (Windows domains, etc). By doing so, compromising the IT domain will not compromise the OT domain.
- Constant Network Monitoring
- A constant network monitoring platform (we happen to know a really good one), will help you identify threats while analyzing network traffic and will help you see the bigger picture of what’s happening in your network.
- Data Exfiltration
Monitor your network for unusual outbound traffic. Everyday user activity should not generate uplink activity higher than about 200MB/daily per user.
How SCADAfence Helps You
We provide a comprehensive solution – The SCADAfence’s platform which was built to protect industrial organizations like yours from industrial cyber attacks (including ransomware). It also helps you implement better security practices amongst its built-in features. Some of these include:
- Asset Management
- Network Maps
- Traffic Analyzers
These tools will help your organization to implement better network segmentation, to make sure that your firewalls are functioning properly, and that every device in the OT network is communicating only with the ones that they should be communicating with. You will also be able to spot assets that are not where they’re supposed to be, for example, forgotten assets in the DMZ.
The platform, which is also the highest-rated OT & IoT security platform, also monitors the network traffic for any threats, including ones that are found in typical ransomware attacks; such as:
- Security exploits being sent across the network.
- Lateral movement attempts using the latest techniques.
- Network scanning and network reconnaissance.
In an event of a security breach, SCADAfence’s detailed alerts will help you to contain these threats as quickly as possible. Ultimately, we built this tool to help industrial organizations to understand their attack surface, to implement effective segmentation and constant network monitoring for any malicious or anomalous activity.
We’d like to share with you a true story of our recent incident response to an industrial ransomware cyberattack. SCADAfence’s incident response team assists companies in cybersecurity emergencies. In this video, we will review a recent incident response activity in which we took part. This research has been published with the goal of assisting organizations to plan for such events and reduce the impact of targeted industrial ransomware in their networks.
For more detailed information on this story, we prepared a full whitepaper here:
About the Author
 Michael brings 15 years of marketing creativity and out-of-the-box thinking to SCADAfence. Before joining the team, Michael was the Director of Marketing at TrapX Security, where he was famous for thought leadership and for turning a small, declining startup into a successful, profitable world-leading vendor in their vertical. Prior to that, Michael was the VP of Marketing at AMC and rebuilt their entire marketing architecture, bringing in strong revenue figures that the firm has’t seen in decades. Michael studied at Harvard Business School, at Bar Ilan University for his MBA & Lander College for his BS degrees in Marketing and Business Management. Michael can be reached at Michael@scadafence.com and at our company website http:/www.scadafence.com
Michael brings 15 years of marketing creativity and out-of-the-box thinking to SCADAfence. Before joining the team, Michael was the Director of Marketing at TrapX Security, where he was famous for thought leadership and for turning a small, declining startup into a successful, profitable world-leading vendor in their vertical. Prior to that, Michael was the VP of Marketing at AMC and rebuilt their entire marketing architecture, bringing in strong revenue figures that the firm has’t seen in decades. Michael studied at Harvard Business School, at Bar Ilan University for his MBA & Lander College for his BS degrees in Marketing and Business Management. Michael can be reached at Michael@scadafence.com and at our company website http:/www.scadafence.com
FAIR USE NOTICE: Under the “fair use” act, another author may make limited use of the original author’s work without asking permission. Pursuant to 17 U.S. Code § 107, certain uses of copyrighted material “for purposes such as criticism, comment, news reporting, teaching (including multiple copies for classroom use), scholarship, or research, is not an infringement of copyright.” As a matter of policy, fair use is based on the belief that the public is entitled to freely use portions of copyrighted materials for purposes of commentary and criticism. The fair use privilege is perhaps the most significant limitation on a copyright owner’s exclusive rights. Cyber Defense Media Group is a news reporting company, reporting cyber news, events, information and much more at no charge at our website Cyber Defense Magazine. All images and reporting are done exclusively under the Fair Use of the US copyright act.

