- I found a Bluetooth tracker for Android users that works better than AirTags (and is cheaper)
- Learn with Cisco at Cisco Live 2025 in San Diego
- This Eufy robot vacuum has a built-in handheld vac - and just hit its lowest price
- I highly recommend this Lenovo laptop, and it's nearly 50% off
- Disney+ and Hulu now offer prizes, freebies, and other perks to keep you subscribed
Product spotlight on risk and threat monitoring

With rapidly-evolving threats and staffing shortages, it’s becoming harder for security leaders to monitor their organizations for potential threats. Security magazine highlights a few products that help keep critical systems safe from attack.
CROWDSTRIKE
Proactively Searches for Threats
Falcon Adversary OverWatch is a 24/7 threat hunting service that spans endpoint, identity and cloud to disrupt adversaries. The software is powered by threat intelligence and artificial intelligence (AI). The software is designed to help analysts locate threats and respond accordingly. The program includes additional information on the common threat actors to an industry or region, helping an organization prepare for an incident before it occurs. Image courtesy of Crowdstrike
FIND OUT MORE AT CROWDSTRIKE.COM
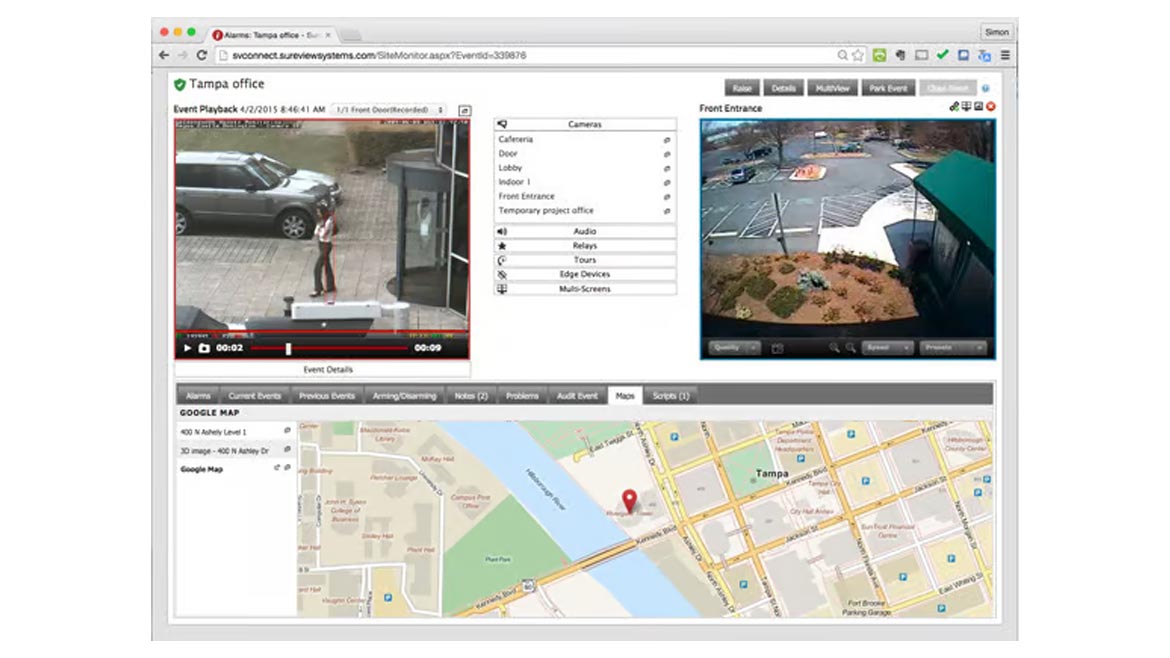
IMMIX
Detect Threats Via Video
AutoPatrol works by enabling scheduled video patrols to be automatically performed via the embedded AI technology. If the AutoPatrol detects an anomaly, such as a change in scene, tamper, presence of an unauthorized person/vehicle/object, as well as a number of additional conditions that can be selected, it will raise the event to be manually confirmed and processed by a human operator to determine the next step. Once raised into the patrol queue, AutoPatrols resemble regular scheduled patrols. Image courtesy of Immix
FIND OUT MORE AT IMMIXPROTECT.COM

KASPERSKY
Automatically Neutralizes Threats
Kaspersky Next EDR Foundations provides endpoint protection that identifies and neutralizes threats before they can harm business processes. Flexible, straightforward security controls and built-in IT scenarios allow hands-off operation and let companies customize their security policies. Image courtesy of Kaspersky
FIND OUT MORE AT USA.KASPERSKY.COM
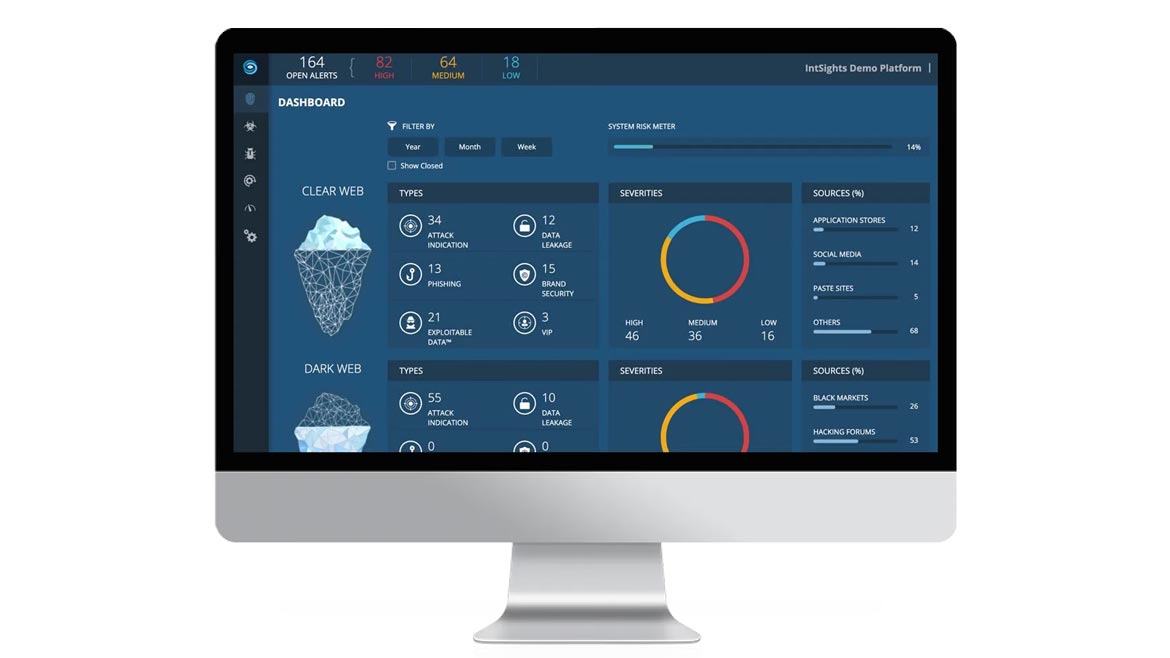
RAPID7
Using Radio For Threat Detection
Rapid7 detection and response includes through plug-and-play integrations with existing technologies for SIEM, SOAR, EDR, firewall, etc. The software includes investigation and mapping capabilities to provide contextualized alerts with low signal-to-noise ratio. Unlimited 24x7x365 access to analysts shortens investigation times as well as accelerates alert triage and response. Image courtesy of Rapid7
FIND OUT MORE AT RAPID7.COM
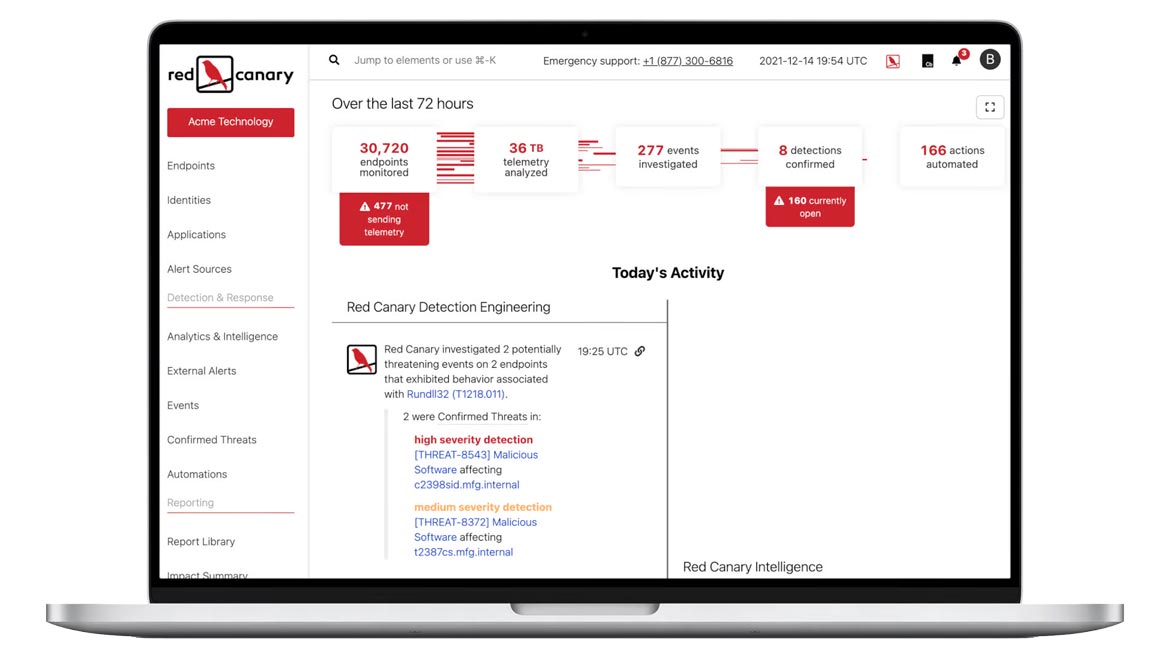
RED CANARY
Track Threat Actors’ Habits
Red Canary detects threats by applying analytics to security telemetry in the places where adversaries operate. The software investigates threats and alerts detected by Red Canary and existing security investments 24/7/365. Playbooks allow security leaders to notify the right people, contain threats and begin remediation. Image courtesy of Red Canary
FIND OUT MORE AT REDCANARY.COM
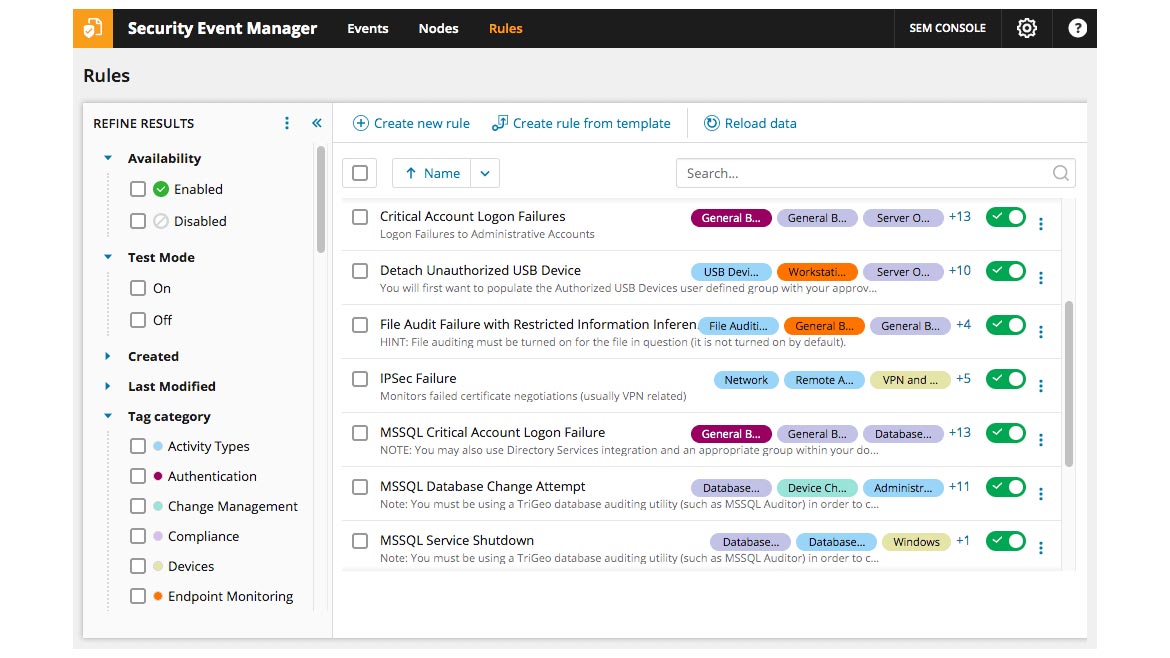
SOLARWINDS
Detect On-Premise Threats
SolarWinds Security Event Manager (SEM) is a security tool designed to simplify threat management for lean IT operations and security teams. It’s built to deploy quickly via virtual appliance and can start detecting threats from across on-premises infrastructure fast using the correlation rules and filters. Image courtesy of SolarWinds
FIND OUT MORE AT SOLARWINDS.COM
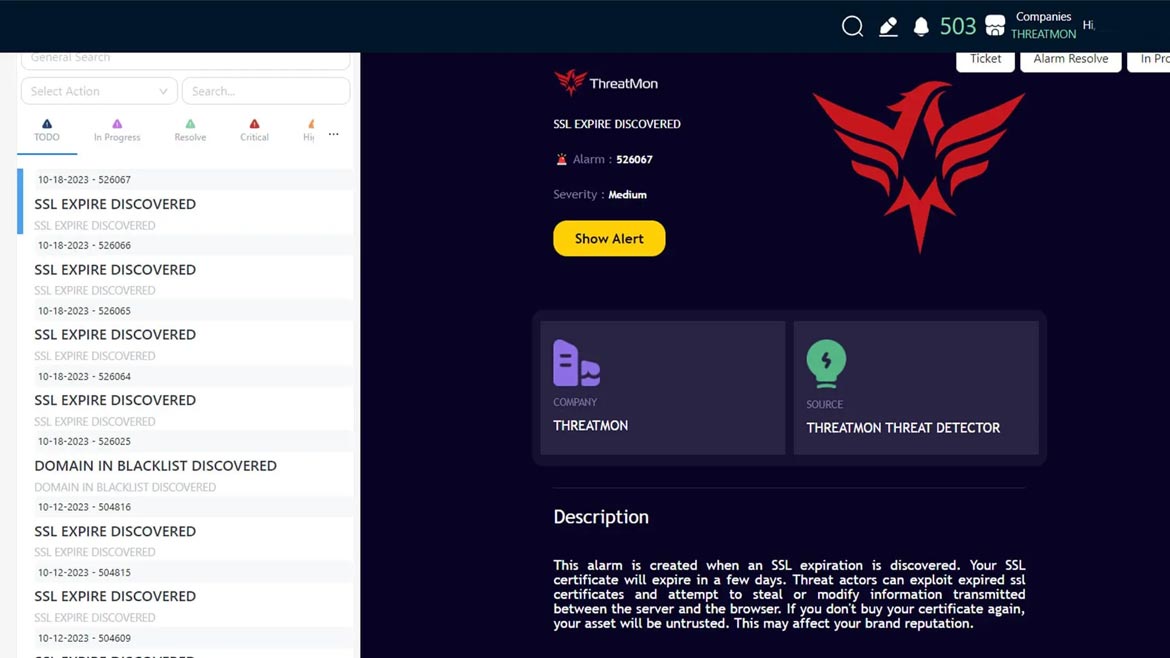
THREATMON
Using Intelligence to Detect Threats
ThreatMon helps organizations prepare against security threats by leveraging a large security database with centralized vulnerability intelligence. The software calculates an organization’s security risk score by taking into account all security issues detected in the external attack surface. In addition, the software aggregates, displays and tracks all activities, findings and security statuses related to its customers’ digital assets in real-time dashboards. Image courtesy of ThreatMon
FIND OUT MORE AT THREATMON.IO

