- I recommend the Pixel 9 to most people looking to upgrade - especially while it's $250 off
- Google's viral research assistant just got its own app - here's how it can help you
- Sony will give you a free 55-inch 4K TV right now - but this is the last day to qualify
- I've used virtually every Linux distro, but this one has a fresh perspective
- The 7 gadgets I never travel without (and why they make such a big difference)
Protecting Against Attacks on NTLM Authentication

When it comes to cyberattacks, March has come in like a lion for Microsoft. Last week, Microsoft said in an SEC filing that that information stolen in a hack of senior leaders’ email accounts is now being used to “gain or attempt to gain access” to company source code repositories and other internal systems. The fallout remains unknown. Just a few days earlier, threat researchers at Proofpoint reported a phishing campaign by the well-known threat group TA577 that targets Windows NT LAN Manager (NTLM) authentication information. Attackers sent thousands of tailored emails designed to steal employees’ NTLM “hashes” (or challenge/response values) from hundreds of organizations around the globe. These “hashes” can be cracked with far-reaching consequences, depending on an organization’s security measures.
Why Is NTLM Authentication Vulnerable
A still widely used protocol in Windows environments, NTLM provides a natively implemented and easy to use method for authenticating into applications on enterprise servers. At more than thirty years old, it’s also a perennial attack target.
Weaker cryptographic algorithms, unsalted password hashes stored on the client and server / domain controller, and a lack of server authentication by default, leave the NTLM protocol susceptible to a variety of attacks, either in the first NTLMv1 or the newer NTLMv2 version. These include interception, man-in-the-middle, relay and pass-the-hash attacks, as well as straightforward brute force and password cracking — eight-character NTLM password hashes can be brute-forced using rainbow tables and other techniques within three minutes. NTLM does not support modern authentication methods like biometrics, multi-factor authentication, or phishing-resistant FIDO keys.
What’s Different About the TA577 NTLM Authentication Campaign?
The abuse of the NTLM protocol for gathering victim’s information and potentially stealing NTLM challenge/response material is not a new technique, and has been observed in the past in different ways. One notable example was the compromise of the San Francisco airport website and several other organizations across the world, where threat actors used the compromised sites to serve malicious code that triggered SMB connections to attacker-controlled servers.
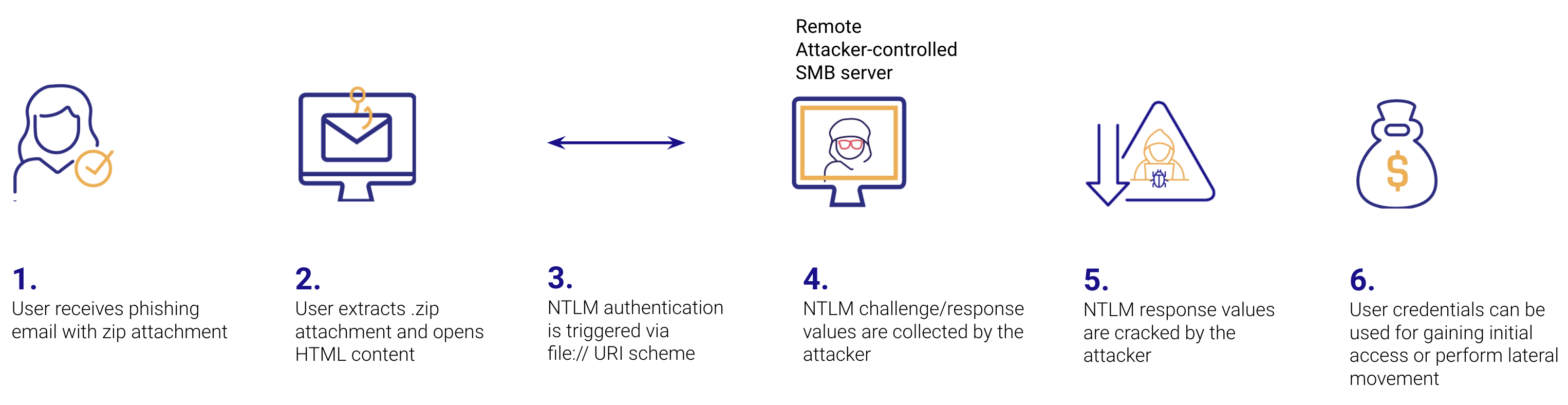
The newest campaign takes a new twist by using phishing thread-jacking techniques to deliver zipped HTML attachments customized for each individual target.
How the Attack Works
The malicious emails appear to be replies to a legitimate message thread. Upon opening, the HTML file triggers a meta refresh attempt to connect to a text file set up by the attacker on a rogue Server Message Block (SMB) server. The attacker-controlled server can then steal the NTLM authentication values when the protocol performs its standard challenge/response exchange. Those values change according to the version of the protocol, and whether it is a NTLMv1 or NTLMv2 exchange, but consist of a nonce (a random value of a single use) that’s encrypted using the user’ passwords as the key.
A very common technique used to make it easier to then crack the obtained challenge/response values, is to leverage a well known and fixed server challenge. The protocol requires the server to include a challenge, consisting of a 16-byte random number, on every connection. By making the server challenge a fixed one, it’s possible to use pre-calculated hash tables and reduce the time and processing required to crack the user’s passwords.
The following diagram shows the steps of the attack:
NTLM Phishing
Consequences of a Successful NTLM Attack
Stolen NTLM challenge/response values can be used to obtain victim’s credentials and hijack accounts, access sensitive information and potentially elevate privileges. Attackers can then move laterally within the network and compromise additional systems in the case they’ve already obtained a foothold into the victim’s organization network.
How HYPR Protects Against the TA577 NTLM Attacks
Microsoft has long provided mitigations and mechanisms to disable the use of the NTLM protocol, including migrating to more secure replacements like Kerberos. However, organizations have been slow to implement these recommendations due to the complexity and dependency of multiple products and legacy systems on these protocols.
When the legacy NTLM authentication protocols cannot be disabled and are still part of the organization’s environment, the resistance to NTLM attacks comes from the strength of the user’s passwords. In these environments, leveraging HYPR’s passwordless approach with certificate-based authentication allows organizations to enforce smart-card usage for passwordless, and remove the dependency of users having to login with their passwords. This provides opportunities to implement mitigation strategies to some of the NTLM weaknesses, such as the use of IT or programmatically-managed strong passwords.
HYPR reduces the risk to organizations from attacks on NTLM authentication by TA577 and other threat actors. HYPR’s phishing-resistant Enterprise Passkeys were built to protect Microsoft Entra ID environments from credential-based attacks while making login easier for users. Microsoft approved and validated, Enterprise Passkeys use highly secure FIDO2 authentication protocols instead of passwords or other types of shared secrets. With HYPR in place, there is no password for an attacker to steal.
Conclusion
As the NTLM authentication protocol relies on passwords, those — indeed all passwords — are a prime target for bad actors. It’s much easier to login with valid credentials than to find a new vulnerability to exploit. Moreover, attackers constantly come up with inventive ways to breach security controls. Organizations need to eliminate the source of insecurity. As a Microsoft partner and member of MISA, HYPR integrates tightly with Microsoft environments and products. Working seamlessly with Microsoft Entra ID, the HYPR Identity Assurance platform combines passkey-based authentication with continuous risk monitoring and automated identity verification to provide the highest level of identity security.
To learn how HYPR helps secure your networks and users against NTLM attacks, talk to our team.
![]()
*** This is a Security Bloggers Network syndicated blog from HYPR Blog authored by Martin Gallo, Sr. Product Manager, HYPR. Read the original post at: https://blog.hypr.com/protecting-against-ntlm-attacks


