- ITDM 2025 전망 | 금융 플랫폼 성패, 지속가능한 사업 가치 창출에 달렸다” KB국민카드 이호준 그룹장
- “고객경험 개선하고 비용은 절감, AI 기반까지 마련” · · · AIA생명의 CCM 프로젝트 사례
- 2025年、CIOはAIに意欲的に投資する - そしてその先も
- The best robot vacuums for pet hair of 2024: Expert tested and reviewed
- These Sony headphones eased my XM5 envy with all-day comfort and plenty of bass
Publisher’s Spotlight: CrowdSec: Real-time & Crowdsourced Protection
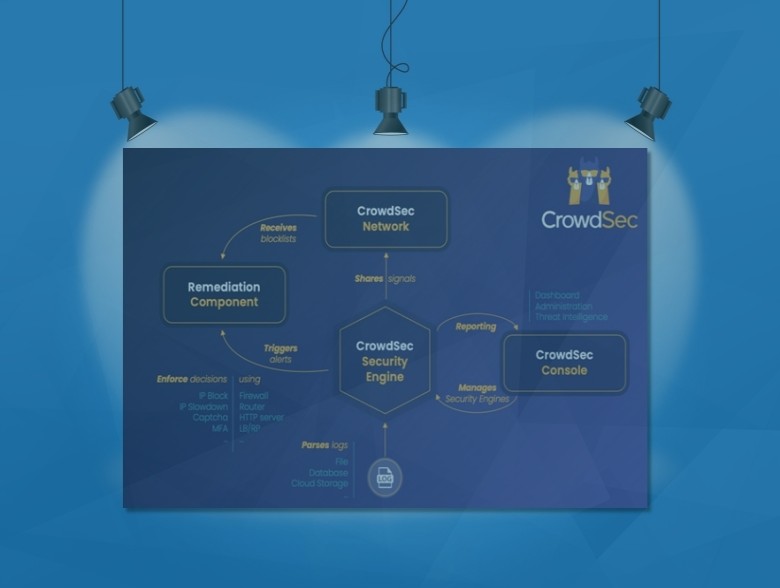
CrowdSec is a modern, collaborative cybersecurity company committed to proactively safeguarding digital assets. With a growing community of 65,000+ active installations contributing to a robust, constantly-updated global IP reputation database as well as its open source software developed for the SOC and DevSecOps community, CrowdSec is revolutionizing cybersecurity by capitalizing on collective intelligence to detect and mitigate emerging and targeted threats in real time.
The efficiency of CrowdSec lies in its simplicity and scale, transforming individual experiences into collective knowledge. As an adaptive behavior detection and remediation system, it operates by analyzing user behavior in OS, servers, and applications logs, identifying malicious patterns, and responding accordingly.
Regardless of where your logs live — the cloud, on-prem, in a SIEM, or on a Windows, BSD, or Linux environment — they can be ingested. When CrowdSec detects a threat from a specific IP, it swiftly applies remedial measures, such as blocking the IP, sending a CAPTCHA, activating Cloudflare attack mode, alerting you, slowing down the traffic, etc.
These actions not only safeguard the local environment but, through the power of collective intelligence, also benefit the wider CrowdSec community. The identified IP is shared with the CrowdSec consensus system, and included in a global blocklist if validated, enhancing security posture for all users.
CrowdSec continuously evolves with each new attack pattern detected, making its threat intelligence even more robust. This creates a proactive and scalable defense mechanism, making CrowdSec a game-changer in today’s dynamic cybersecurity landscape. To this day, CrowdSec has the largest real-time cybercrime IP map in the world, accessible to all its users.
CrowdSec Stats
- 190+ countries represented by the CrowdSec Community
- 65,000+ active users
- 50 Million malicious IPs flagged
- 100 Million weekly attack signals reported
CrowdSec Q2 Majority Report Stats (Full Report Linked Here)
- Only 5% of reported IPs are flagged as VPN or proxy users. VPN’s rise to popularity over the past few years sounded the alarm for many organizations. However, contrary to popular belief, data collected by the CrowdSec network indicates that VPNs and proxies play a far less significant role in cybercriminal activities.
- IPv6 represents 20% of reported malicious IPs. With such high adoption, it was inevitable that IPv6 eventually started registering on cybersecurity radars. For October 2022–June 2023, the CrowdSec network detected increased new threats linked to IPv6 addresses.
- Malevolent Duration (MD) is a more accurate metric for evaluating an Autonomous System (AS) than the number of compromised assets. This refers to the number of days for which users report a malicious IP to the operator. The average MD of all the IPs in the same AS indicates the operator’s due diligence when it comes to identifying and dealing with compromised assets. Meanwhile, the size of operators varies greatly, creating a discrepancy when comparing big operators to small. Though big operators inevitably receive a greater number of reports related to malicious IPs, smaller operators with fewer affiliated IPs — therefore receiving fewer reports — may be hosting riskier services.
- Third-party reports of infected machines play a significant role. The ability to quickly deal with infected machines reported by third parties within a network, as well as proactively identifying infected machines based on behavioral patterns, significantly impacts how long a machine stays infected.
- Low MD translates to a lower risk for a business to inherit a machine that has been flagged as malevolent. By extension, this also minimizes the risk of a legitimate business asset being preemptively blocked by partners, prospects, or potential customers.
“The Majority Report serves as a testimony to the power of crowdsourced data. We created this report to provide the industry with much-needed threat intelligence in detecting malicious behavior and preventing imminent cyberattacks. In the Majority Report, you will find evidence of the effectiveness of the CrowdSec network in spotting and blocking malicious IPs before they get a chance to breach your system.” – Philippe Humeau, CrowdSec CEO and co-founder, CrowdSec
“Since the implementation of CrowdSec on our entire information system at Crédit Mutuel Arkea in 2021, the solution has helped us block countless waves of brute force attacks on the group’s subsidiaries. Today, we use it to build business-oriented models with detection approaches specific to different applications. We also plan to use the solution to detect cross-functional attacks within our information system.” – Guillaume Roussel, Operations Manager in charge of IS security at Crédit Mutuel Arkea.
“We know that each partner brings local strengths and expertise to the table, and we are committed to fostering an environment that encourages collaboration and knowledge sharing. By expanding our partner network, we will create trusted relationships allowing us to access new markets, extending the reach of our unique approach to cybersecurity globally.” – Courtney Austin, Chief Marketing Officer, CrowdSec
Checkout the CrowdSec Academy: This is the place to learn the fundamentals of cybersecurity and master CrowdSec’s open source Security Engine with our free hands-on learning materials. Earn awards to show off your progress and raise your profile in the world of cybersecurity! When you succeed, we all succeed. Free courses at https://academy.crowdsec.net.
About the Author
 Gary Miliefsky is an internationally recognized cybersecurity expert, bestselling author and keynote speaker. He is a Founding Member of the US Department of Homeland Security, served on the National Information Security Group and served on the OVAL advisory board of MITRE responsible for the CVE Program. He founded and is the Publisher of Cyber Defense Magazine since 2012. Visit Gary online at: https://www.cyberdefensemagazine.com/
Gary Miliefsky is an internationally recognized cybersecurity expert, bestselling author and keynote speaker. He is a Founding Member of the US Department of Homeland Security, served on the National Information Security Group and served on the OVAL advisory board of MITRE responsible for the CVE Program. He founded and is the Publisher of Cyber Defense Magazine since 2012. Visit Gary online at: https://www.cyberdefensemagazine.com/


