- I replaced my Ring with this outdoor security camera - and it has no subscription
- If you're ready to pull the plug on Windows, I found an ideal Linux distro for new users
- This handy USB meter tells you what's actually going on with your ports - and it's only $20
- This budget Lenovo ThinkPad has no business being this good - especially for hybrid workers
- Déjà Vu: What Cloud Adoption Can Teach Us About AI in Cybersecurity
Publisher’s Spotlight: Cycode: Secure Code to Cloud – Application Security Posture Management (ASPM) at Scale
Cycode’s modern approach to application security enables organizations to effectively secure their cloud-native applications with cost-efficient use of tooling and staff across the SDLC. The Cycode platform makes AppSec tools better through its Knowledge Graph, which provides complete context of the SDLC to improve accuracy and reduce mean-time-to-remediation (MTTR). Cycode merges the top eight AppSec tools into the industry’s most advanced and comprehensive AppSec platform. By correlating data across these tools, Cycode offers new capabilities such as Pipeline Composition Analysis, which identifies vulnerable dependencies and security issues missed by legacy tools like SCA and SAST across the entire SDLC; pinpoints vulnerable dependency locations; and prioritizes threats by exploitability.
“We chose Cycode because of its broad coverage of programming languages and its ease of deployment. With Cycode, minimal time is needed from developers to implement. Teams can realize value from Cycode within hours of setting it up,” said Dr. Jasyn Voshell, Director Product and Solutions Security at Zebra Technologies.
“Without the visibility that Cycode gives us, many of the biggest companies in the world would not do business with us. To provide financial services to large companies, you have to follow the rules. Cycode has provided that pillar for us and has allowed us to pursue those largest companies and do business with them to expand our business,” said Zachary Padilla, Lead Cyber Security Engineer at Kyriba.
“Over the last year, tool consolidation and saving money has become more important. With Cycode, we can do a lot on one platform,” said Erez Mor, Director of Security Engineering at Rapyd.
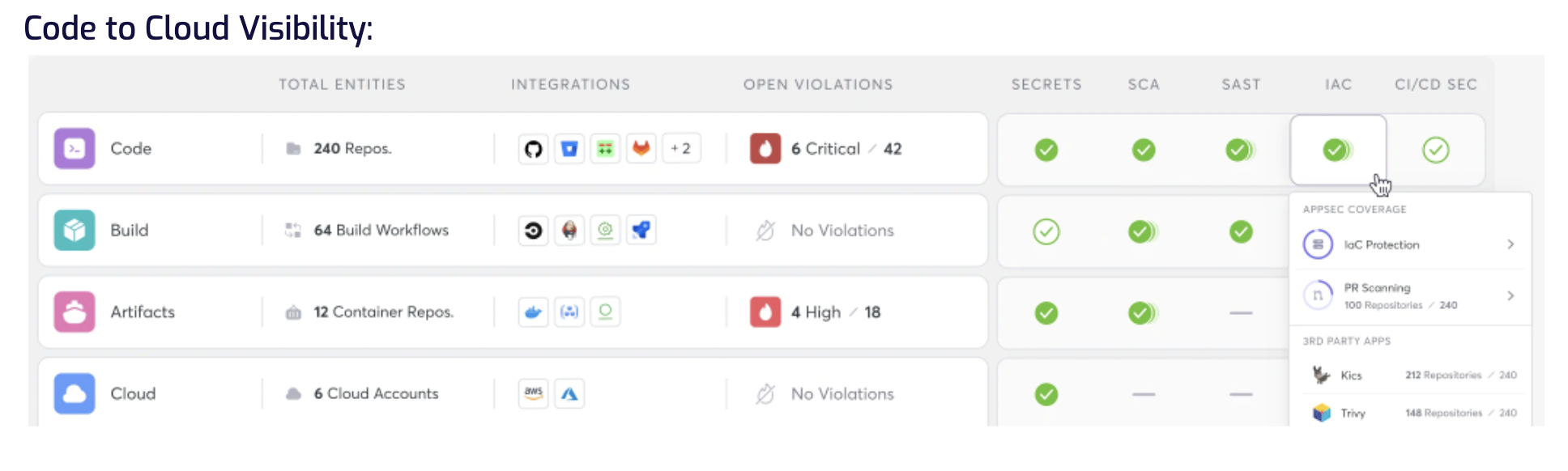
“Traditional AppSec is broken. The world runs on apps and organizations still struggle to gain complete visibility and control over their applications, dependencies and risks. AppSec tools generate too much noise while, at the same time, attack surfaces continue to expand, creating huge gaps in coverage that leave pipelines exposed.
For organizations to accurately assess their security risk, they need AppSec, Supply Chain and Cloud security to converge. ASPM addresses these problems while also taming the proliferation of security tools by consolidating all alerts and risk intelligence onto one central platform. There isn’t a more critical time to bring peace to all the chaos,” said Ronen Slavin, co-founder and CTO of Cycode.
An eBPF-based tool for code monitoring provides new visibility into the software pipeline, aiming to forestall further SolarWinds- or Codecov-style attacks.
Cycode’s new Cimon monitoring tool for continuous integration and continuous delivery is designed to offer a new level of visibility into the CI/CD process, securing code against data exfiltration and other malicious activity.
According to the company’s announcement, Cimon — short for CI Monitor — is a runtime security agent that uses the enhanced Berkeley Packet Filter (eBPF) system to look directly into the CI pipeline, develop a baseline understanding of what normal behavior looks like and monitor for abnormalities.
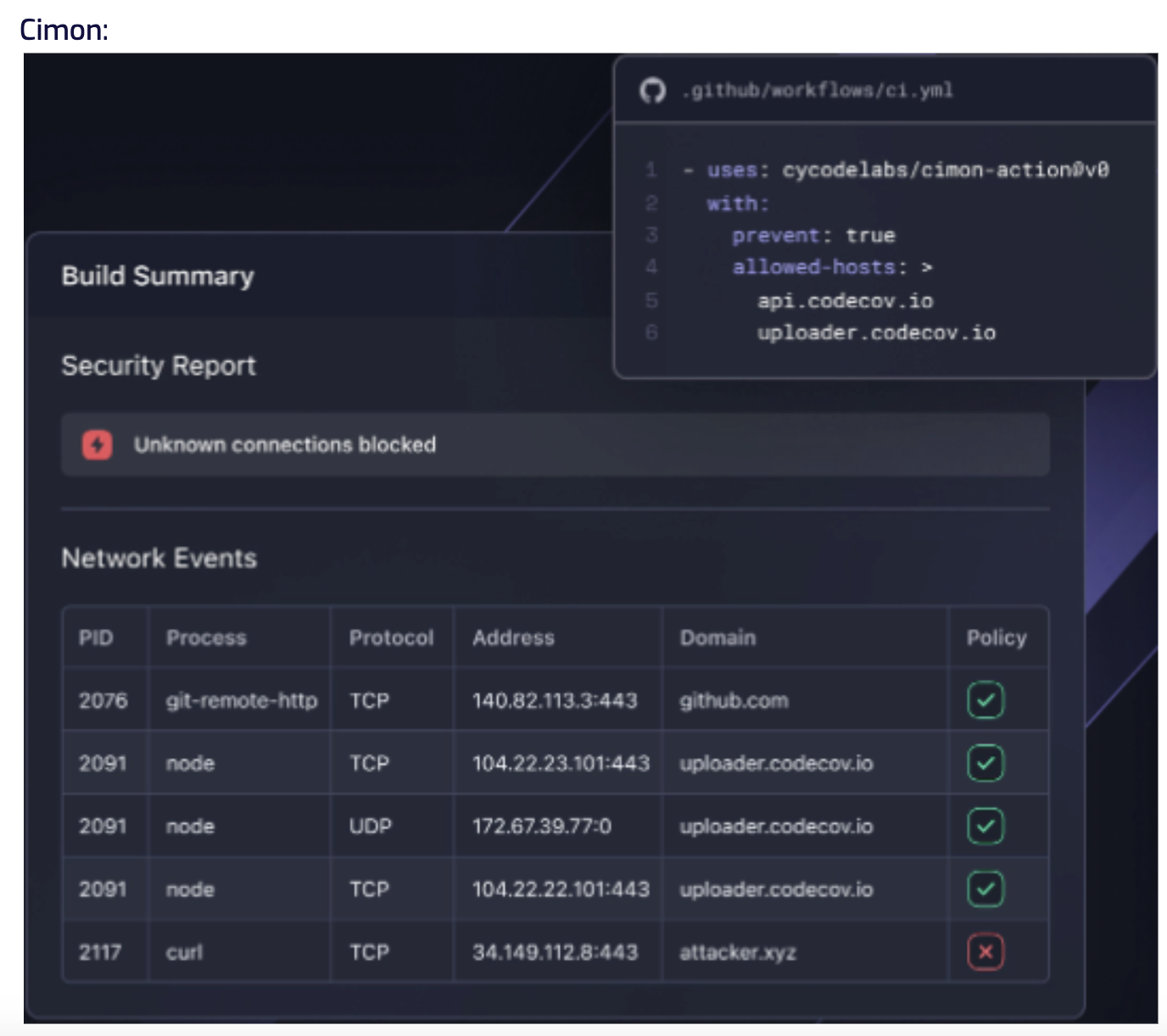
According to Cycode head of security research Alex Ilgayev, the use of eBPF provides for flexibility and visibility into the operating system.
“Whether it’s a hosted runner on GitHub or a hosted runner on CircleCI or some self-hosted runner-based on containers, once you install the agent, it sees everything,” he said, “The idea is to prevent cyberattacks against software code bases.” Attacks on build systems, dependency attacks and typosquatting — where a bad actor publishes malicious software under a similar name to a widely used open source component — are on the rise. Cimon would prevent those by monitoring CI/CD for expected execution outcomes at the kernel level, as well as network and file system events.
For more information, visit them online at https://cycode.com/.
About the Author
 Gary Miliefsky is an internationally recognized cybersecurity expert, bestselling author and keynote speaker. He is a Founding Member of the US Department of Homeland Security, served on the National Information Security Group and served on the OVAL advisory board of MITRE responsible for the CVE Program. He founded and is the Publisher of Cyber Defense Magazine since 2012. Visit Gary online at: https://www.cyberdefensemagazine.com/
Gary Miliefsky is an internationally recognized cybersecurity expert, bestselling author and keynote speaker. He is a Founding Member of the US Department of Homeland Security, served on the National Information Security Group and served on the OVAL advisory board of MITRE responsible for the CVE Program. He founded and is the Publisher of Cyber Defense Magazine since 2012. Visit Gary online at: https://www.cyberdefensemagazine.com/

