- I ditched my daily driver Bose headphones for the XM6 - and I'm hesitant to go back
- This Lenovo ThinkPad is my top pick for remote work - and it's nearly 50% off now
- I invested in this 3-in-1 robot vacuum, and it's paying off for my home
- I've tested the Meta Ray-Bans for months, and these 5 features still amaze me
- My new favorite iPhone portable charger has a magnetic superpower - and it's cheap
Ransomware as a Service 101

Risk Management
To help you enhance your defense against ransomware, Trend Micro Research shares key insights on how ransomware as a service (RaaS) operators work.
Read time: ( words)
Individuals looking to launch costly attacks on large organizations don’t need to be skilled hackers. Thanks to ransomware as a service (RaaS), prospective attackers can easily equip themselves with the necessary tools and techniques. To help, Trend Micro Research takes a deeper look at most common ransomware families and techniques associated with this growing “business model,” enabling CISOs like yourself to fine-tune your security strategy for a more effective defense.
What is Ransomware as a Service (RaaS)?
Credited as one of the reasons causing ransomware attacks to grow, RaaS, based on the SaaS model, involves selling or renting ransomware capabilities to buyers (called affiliates). Among the key players in this ecosystem are the operators, those who develop and sell the ransomware. They are usually part of a larger group with designated roles.
Unlike in the past where ransomware operators launched the attack themselves, they’re putting their ransomware up for sale to attackers who want to initiate an attack. The more people that purchase the ransomware, the more attacks, and victims.
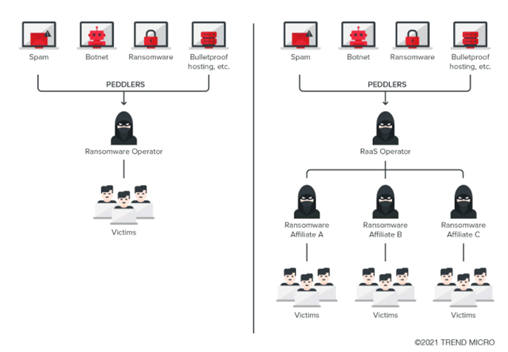
However, this isn’t a free-for-all. To increase the chances of a big payout, RaaS operators or affiliates are very selective when choosing a target. For example, Trend Micro Research observed many public and private group discussions about avoiding specific countries like Taiwan, due to strict anti-money laundering policies that make it difficult to purchase cryptocurrency to pay the ransom.
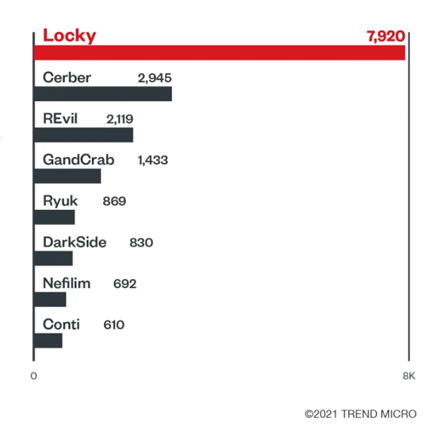
Ransomware families used by RaaS operators and affiliates
The RaaS model has been adopted by most modern ransomware families. In fact, our midyear cybersecurity report determined that 8 of the top 10 most detected ransomware families have been used by RaaS operators and affiliates at some point.
Defending against ransomware
Now that you know what to look for, how do you create an effective ransomware defense strategy?
1. Leverage cybersecurity frameworks from the Center of Internet Security (CIS) and the National Institute of Standards and Technology (NIST) for thorough guidance on prioritization and resource management, as well as filling any gaps that could be exposed by attackers. Some of the best practices from these frameworks are:
a. Audit events and take inventory
b. Configure and monitor
c. Patch and update
d. Protect systems and recover data
2. Create multiple layers of defense by continuously monitoring for early signs of an attack and using advanced detection techniques such as AI-powered technologies and machine learning.
3. Train and test your defense strategy by conducting regular security skills assessment and training, as well as red team exercises and penetration tests.
To continue improving your security strategy against RaaS operators and the most commonly used modern ransomware families and techniques, check out Ransomware as a Service: Enabler of Widespread Attacks
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk

