Research Eyes Misconfiguration Issues At Google, Amazon and Microsoft Cloud

Qualys report looks at how misconfiguration issues on cloud service providers help attackers gain access.
Cloud misconfiguration — incorrect control settings applied to both hardware and software elements in the cloud — are threat vectors that amplify the risk of data breaches. A new report from cloud security vendor Qualys, authored by Travis Smith, vice president of the company’s Threat Research Unit lifts the lid on risk factors for three major cloud service providers.
About the report
Smith wrote that Qualys researchers, analyzing misconfiguration issues at Amazon Web Services, Microsoft Azure and Google Cloud Platform, found that within Azure, 99% of the disks are either not encrypted or aren’t using customer-managed keys that give users control of encryption keys that protect data in software as a service applications.
The study, which reviewed encryption, identity and access management and failures to monitor external-facing assets examined risks to unauthorized access due to:
- The complexity of cloud environments
- Lack of expertise in keeping up with evolving technologies
- Insecure settings and permissions caused by human errors
- Rapid deployment compromising security implementation measures
- Lack of control and visibility of cloud-resident unencrypted or sensitive data due to the dynamic nature of cloud environments
Smith wrote that the company’s reachers found that 85% of the keys aren’t rotated, meaning automatic key rotation isn’t enabled. Amazon offers automatic key rotation — generating new cryptographic material — on a 365 day cycle for keys.
Qualys also reported that in GCP environments, 97.5% of virtual machine disks for critical virtual machines lack encryption using customer-supplied encryption keys.
Jump to:
Identity and Access Management
Qualys found poor implementation levels of IAM in all three major providers:
- Multifactor authentication: AWS isn’t enabled for 44% of IAM users with console passwords. IAM Access Analyzer isn’t enabled in 96% of the accounts scanned by Qualys.
- In Azure, scans for enabling authentication and configuring client certificates within Azure App Service fail 97% of the time.
Exposure of external-facing assets from leaky S3 buckets
Qualys noted that a common mistake by users across the three platforms is public exposure of data:
- Qualys reported 31% of S3 buckets are publicly accessible.
- The misconfiguration of leaving public network access enabled was seen in 75% of the Azure databases.
Center for Internet Security work offers insights to remediation
Recommendations by the firm included reviewing research by the Center for Internet Security including work Qualys participated in: mapping of individual controls to the MITRE ATT&CK tactics and techniques.
Qualys contributed to developing these CIS benchmarks for AWS, Azure and GCP. The benchmarks will help offer some valuable insight and context for defenders to better prioritize the hundreds of hardening controls available in cloud environments.
Qualys also looked at how firms are deploying controls to harden their cloud postures across the three major platforms, noting that privilege escalation (96.03%), initial access (84.97%) and discovery (84.97%) are passing at the highest rates.
Efforts to control attacks early are helping to ameliorate more harmful consequences further along the the kill chain:
- Impact passed at only 13.67%
- Exfiltration at only 3.70%.
- Exploitation of public facing apps passed at only 28.54%.
- Exploitation of remote services, at only 17.92%, are failing at high rates.
- Resource hijacking is passing at just 22.83%.
Smith wrote that since crypto mining malware is a threat to cloud environments, organizations should consider mitigating such controls to reduce their organizational risk in the cloud.
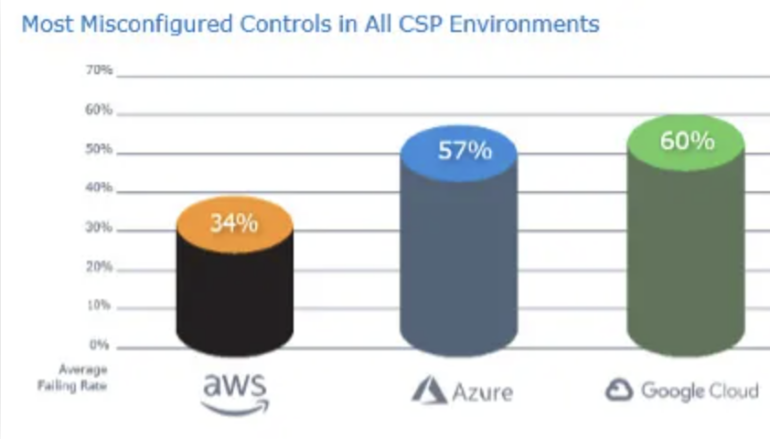
“The lesson from these data points is that almost every organization needs to better monitor cloud configurations,” said Smith, adding that scans for CIS controls failed 34% of the time for AWS, 57% for Microsoft Azure and 60% for GCP (Figure A).
Figure A
“Even if you believe your cloud configurations are in order, the data tells us that not regularly confirming status is a risky bet. Scan the configurations often and make sure the settings are correct. It takes just one slip-up to accidentally open your organization’s cloud to attackers,” wrote Smith.

