- The top-selling smartphone in 2025 so far might surprise you - here's why
- Apple Intelligence hasn't lived up to my expectations, but these 3 upgrades could win me back
- Samsung launches One UI 8 beta - what's new and how to join
- This 230-piece Craftsman toolset is still just $99 at Lowe's
- Grab this 85-inch Samung TV and home audio bundle for $2,500 off
Researchers find threat group that has been active for 5 years

Yuri_Arcurs/Getty Images
Researchers on Tuesday revealed a new threat actor that over the past five years has blasted thousands of organizations with an almost endless stream of malicious messages designed to infect systems with data-stealing malware.
TA2541, as security firm Proofpoint has named the hacking group, has been active since at least 2017, when company researchers started tracking it. The group uses relatively crude tactics, techniques, and procedures, or TTPs, to target organizations in the aviation, aerospace, transportation, manufacturing, and defense industries. These TTPs include the use of malicious Google Drive links that attempt to trick targets into installing off-the-shelf trojans.
Tenacity and persistence
But what the group lacks in sophistication, it makes up for with a tenacity and persistence that allows it to nonetheless thrive. Since Proofpoint began tracking the group five years ago, it has waged an almost unending series of malware campaigns that typically deliver hundreds to thousands of messages at a time. A single campaign can impact hundreds of organizations all over the world, with an emphasis on North America, Europe, and the Middle East.
“Often, campaigns contained several hundred to several thousand email messages to dozens of different organizations,” company researchers Selena Larson and Joe Wise wrote in a report published on Tuesday. “Although Proofpoint has observed TA2541 targeting thousands of organizations, multiple entities across aviation, aerospace, transportation, manufacturing, and defense industries appear regularly as targets of its campaigns.”
Researchers from other companies—including Cisco’s Talos Group, Morphisec, Microsoft, Mandiant, and others—have also published data on similar activities.
In Tuesday’s report, Proofpoint described the group’s TTPs in detail. Company researchers wrote:
In recent campaigns, Proofpoint observed this group using Google Drive URLs in emails that lead to an obfuscated Visual Basic Script (VBS) file. If executed, PowerShell pulls an executable from a text file hosted on various platforms such as Pastetext, Sharetext, and GitHub. The threat actor executes PowerShell into various Windows processes and queries Windows Management Instrumentation (WMI) for security products such as antivirus and firewall software, and attempts to disable built-in security protections. The threat actor will collect system information before downloading the RAT on the host.
The attack chain looks like this:
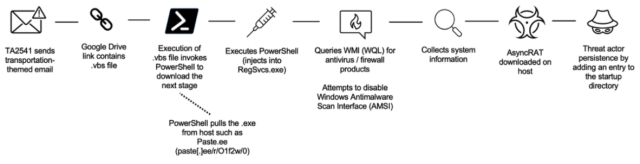
Proofpoint
Occasionally, the group uses Microsoft OneDrive to host the trojans, which over the years have included more than a dozen malware families available for sale in underground crime forums or for free in repositories. Families include AsyncRAT, NetWire, WSH RAT, and Parallax. The malware allows the group to gather information from infected networks and gain remote access to infected machines. More recently, TA2541 has used DiscordApp URLs and email attachments to distribute malicious code.
The group gets the trojans to achieve persistence—meaning the ability to automatically run each time a machine is turned on—using one of two methods. The first is by adding the VBS file to a computer’s startup folder. The second is by creating scheduled tasks and adding entries in the Windows directory. VBS scripts look similar to this one.
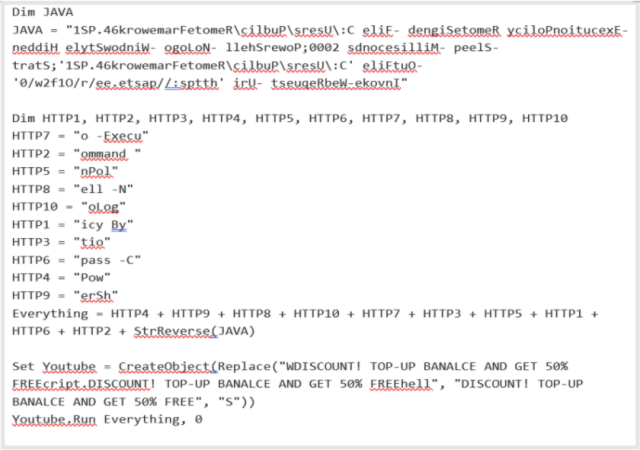
Proofpoint
When deobfuscated, the file points to the URL https://paste[.]ee/r/01f2w/0. A sample of the PowerShell code used in a recent campaign is depicted below:
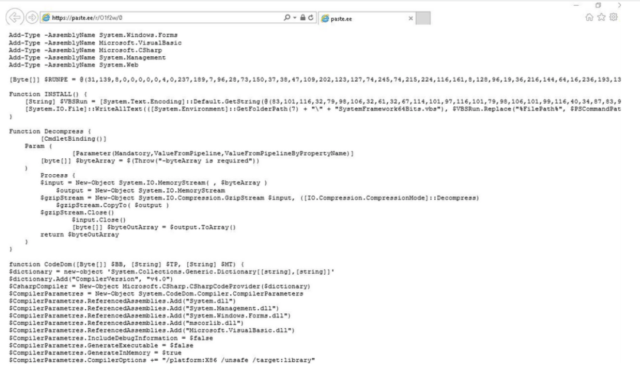
Proofpoint
Despite the lack of sophistication, the group should be taken seriously. Tuesday’s report lists a host of malicious domains, malware hashes, and other indicators that can be used to detect attempted or successful network incursions by the group. Admins working for companies in one of the targeted industries should check their networks for signs of infection, since Proofpoint sees no signs that the group plans to stop.
“TA2541 remains a consistent, active cybercrime threat, especially to entities in its most frequently targeted sectors,” the company researchers wrote. “Proofpoint assesses with high confidence this threat actor will continue using the same TTPs observed in historic activity with minimal change to its lure themes, delivery, and installation. It is likely TA2541 will continue using AsyncRAT and vjw0rm in future campaigns and will likely use other commodity malware to support its objectives.”

