- I recommend the Pixel 9 to most people looking to upgrade - especially while it's $250 off
- Google's viral research assistant just got its own app - here's how it can help you
- Sony will give you a free 55-inch 4K TV right now - but this is the last day to qualify
- I've used virtually every Linux distro, but this one has a fresh perspective
- The 7 gadgets I never travel without (and why they make such a big difference)
Researchers Warn of 674% Surge in Deadbolt Ransomware
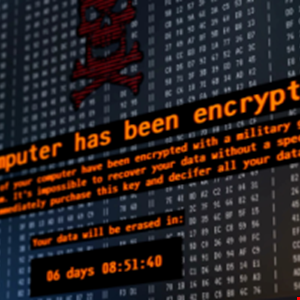
Security experts have flagged a spectacular surge in network-attached storage (NAS) devices around the world infected with the Deadbolt ransomware variant.
Devices made by Taiwanese company QNAP have been targeted by the group since the start of the year. It appears that the hackers took advantage of a vulnerability in the products to compromise them, causing major problems for the consumers and small businesses that are typical QNAP customers.
However, attack surface management vendor Censys has warned that the attacks have kept on coming over the summer.
It recorded a global infection count of 2459 on June 27, rising to 7783 on July 15, then 9091 on July 30, and finally a high of 19,029 devices on September 4. That’s a 674% increase in just over two months.
A majority of these infections were found in the US, with 2472 hosts showing signs of Deadbolt, followed by Germany (1778), and Italy (1383).
A spike in infections noted between September 1 and the following day, when the number of affected devices jumped from 7748 to 13,802, may have been caused by a newly exploited zero-day bug, which QNAP described in a notice on September 3.
The recent spike is way higher than the normal cadence of new infections recorded by Censys, explained senior security researcher Mark Ellzey.
The firm was able to track infected devices due to the way Deadbolt ransomware works, he explained.
“Instead of encrypting the entire device, which effectively takes the device offline (and out of the purview of Censys), the ransomware only targets specific backup directories for encryption and vandalizes the web administration interface with an informational message explaining how to remove the infection,” said Ellzey.
“Due to how this ransomware communicates with the victim, Censys could easily find infected devices exposed on the public internet via this simple search query. Besides broad information about which hosts were infected with Deadbolt, we could also obtain and track every unique bitcoin wallet address used as a ransom since the BTC address used for ransom drops is embedded within the HTML body.”
QNAP users are urged to upgrade to the latest version to fix the latest vulnerability, tracked as CVE-2022-27593.

