RSA Conference

RSAC is a time for cybersecurity leaders to come together and share best practices within the community.
Security magazine highlights products being showcased at this year’s RSA Conference.
ARCTIC WOLF
Manage Company Vulnerabilities
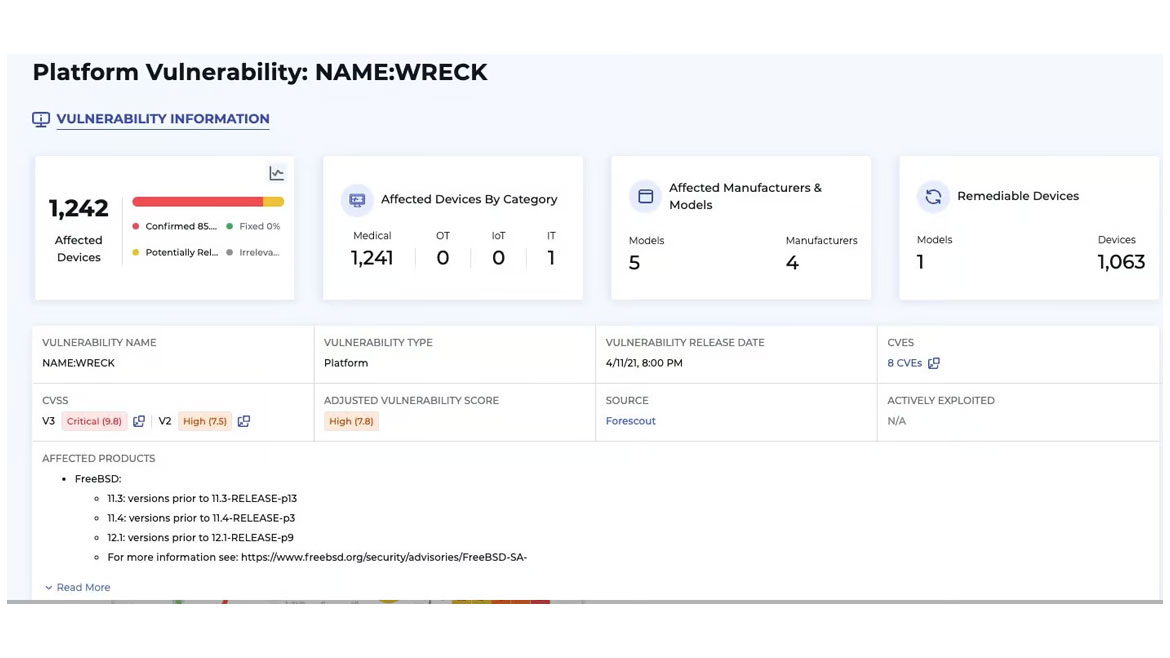
Arctic Wolf OEM Solutions is a suite of security scanning and threat intelligence capabilities designed to meet the needs of original equipment manufacturers (OEMs), independent software vendors (ISVs) and large enterprises looking to add critical security operations capabilities to their solutions. By leveraging Arctic Wolf OEM Solutions, OEMs, ISVs and other similarly situated organizations can add vulnerability management, threat intelligence and additional security operations capabilities. Image courtesy of Arctic Wolf
FIND OUT MORE AT ARCTICWOLF.COM
CLAROTY
Detect and Manage Threats
Claroty’s Advanced Anomaly Threat Detection (ATD) Module allows healthcare to strengthen their cybersecurity postures and achieve regulatory compliance. Signature-based detection enhances threat detection, analysis and response based on known signatures and Indicators of Compromise (IoCs). Signature content can be viewed for investigation purposes and enabled or disabled as needed to tune the system. Custom communication alerts understand and alert on device communication patterns across the network to identify abnormal behavior and traffic across connected devices, such as a BMS communicating with a guest network or an IoMT device using an unsecured protocol. Image courtesy of Claroty
FIND OUT MORE AT CLAROTY.COM
FORTINET
Integrate Security and Wi-Fi
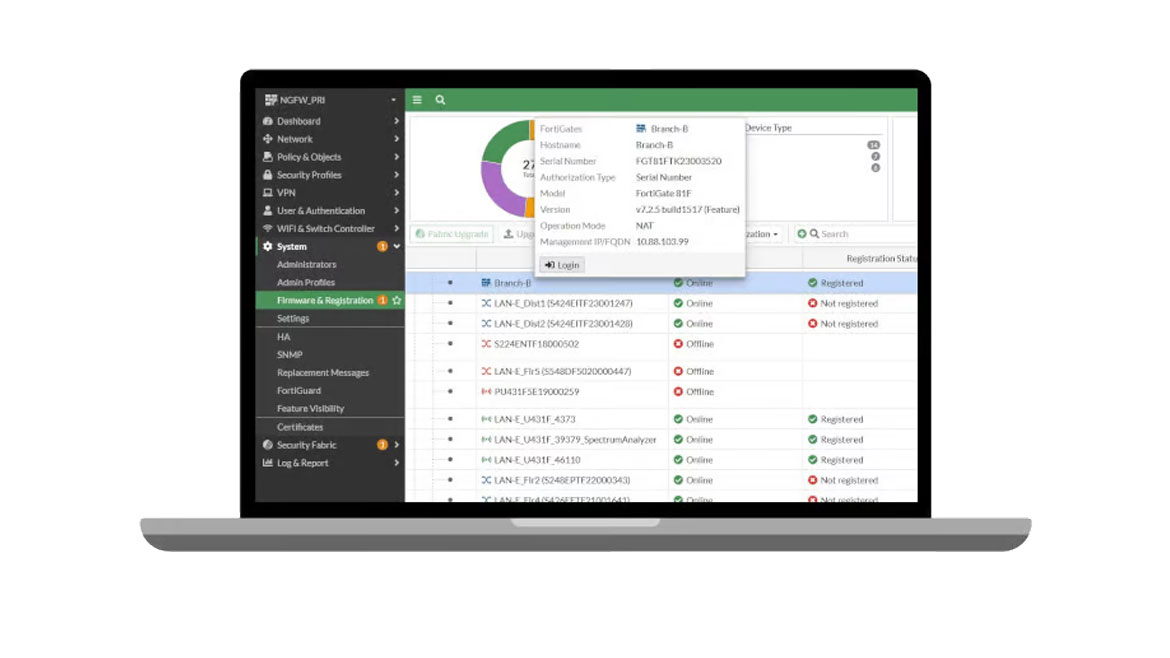
Fortinet announced a comprehensive secure networking solution integrated with Wi-Fi 7. FortiAP 441K delivers increased speed and capacity, and the new FORTISWITCH T1024 is purpose-built with 10 Gigabit Ethernet (GE) access and 90W Power over Ethernet (PoE) technology to support Wi-Fi 7 bandwidth requirements. Image courtesy of Fortinet
FIND OUT MORE AT FORTINET.COM
HIVE PRO
Manage Workflow and Conduct Assessments
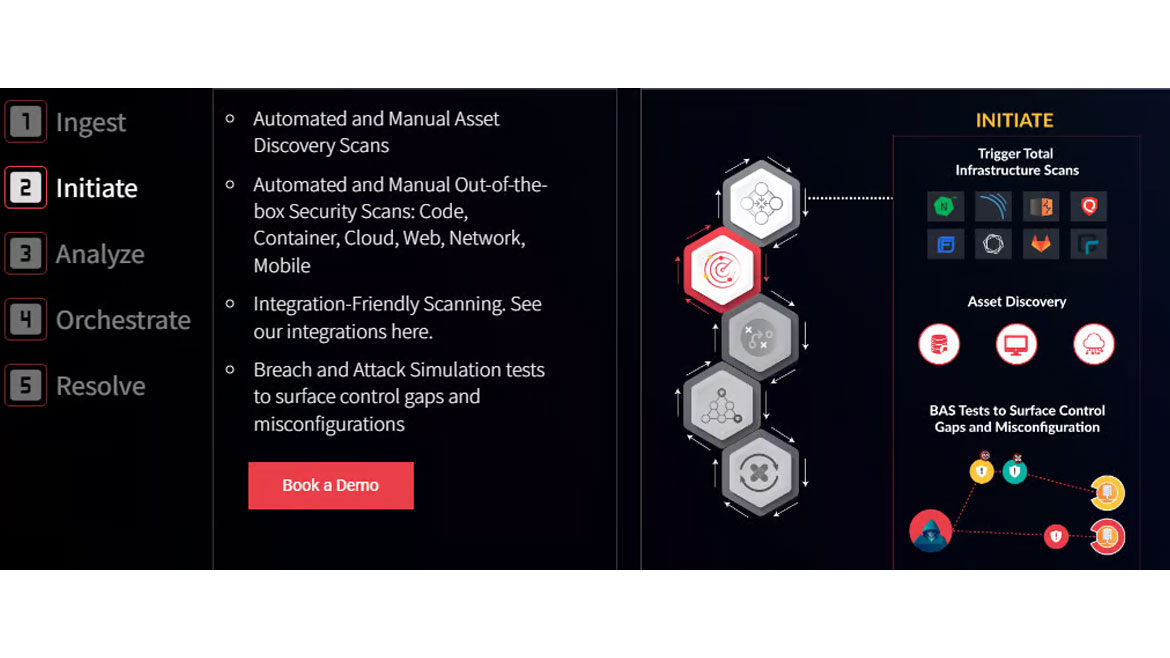
Hive Pro announced their new platform Uni5 Xposure. Uni5 Xposure includes asset discovery, infrastructure scanning, security assessments, workflow management and collaboration. The platform integrates previous system benefits while adding new systems. Image courtesy of Hive Pro
FIND OUT MORE AT HIVEPRO.COM

SWISSBIT
Protecting Digital Identities
The iShield Key Pro by Swissbit transcends the capabilities of a standard FIDO stick by incorporating an array of enhanced features and various security protocols to ensure the versatile protection of digital identities. It integrates Personal Identity Verification (PIV) functionality, facilitating tasks like digital document signing and encryption. The iShield Key Pro is also compatible with legacy systems, including HOTP and TOTP. Its capability to double as a physical access control tool sets it apart in the market. The impending adoption of FIPS 140-3 standards provides a maximum level of cryptographic security. Available with USB-A and USB-C interface. Image courtesy of Swissbit
FIND OUT MORE AT SWISSBIT.COM
ZEROFOX
Detects and Prevents Phishing Attacks
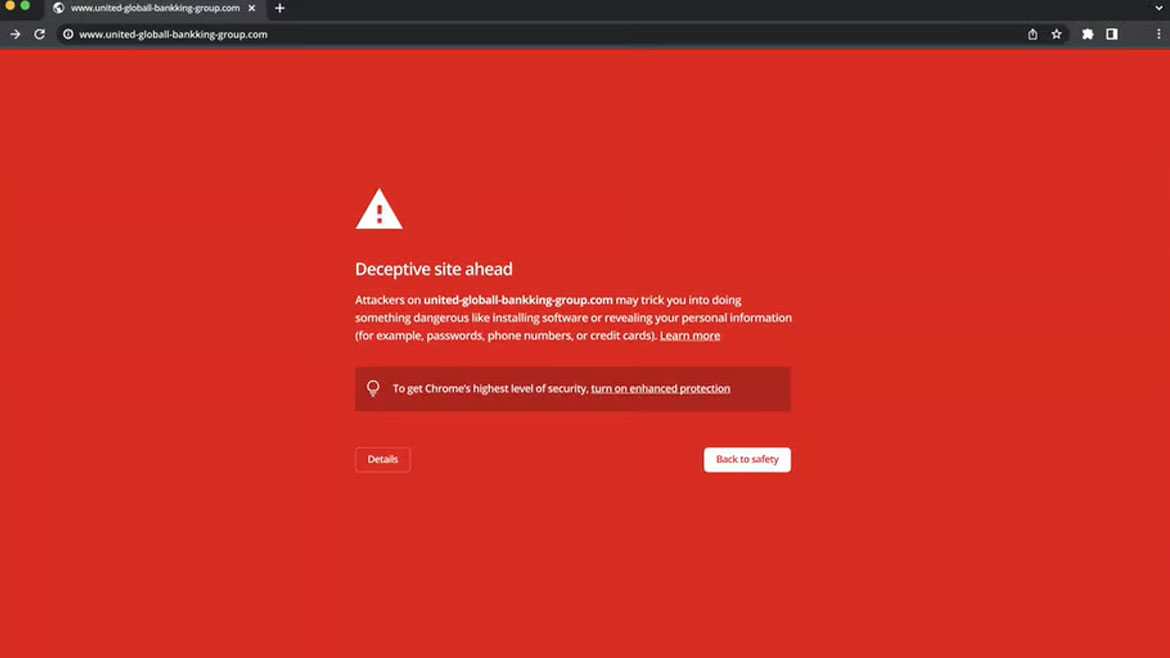
ZeroFox’s anti-phishing software will focus on identifying, disrupting and taking down the domain(s) required to stand up a phishing campaign. The program thwarts typosquats, homoglyphs, subdomain spoofs and other malicious domain and URL threats. SSL monitoring ensures only secured and verified certificates are in use. The system also scans and alerts to fraudulent use of a company’s imagery. Image courtesy of ZeroFox
FIND OUT MORE AT ZEROFOX.COM

