- Google Gemini will let you schedule recurring tasks now, like ChatGPT - here's how
- iOS 26 isn't just about a rebrand and Solarium - here's what else is coming
- Connect with the Mid-Market and SMB Team at Cisco Live US
- AWS cuts prices of some EC2 Nvidia GPU-accelerated instances
- Energy Management in the AI Era: Cisco's Digital Transformation Advantage
SAP Flaw Exploited by Ransomware Groups and Chinese-Backed Hackers

Cybersecurity researchers are piling up evidence that a critical vulnerability affecting German software company SAP’s NetWeaver Visual Composer development server is being exploited in the wild by a range of threat actors.
These include ransomware groups BianLian and RansomwEXX, as well as at least one Chinese nation-state actor known as Chaya_004.
Strong Evidence of Exploitation
The flaw, tracked as CVE-2025-31324, is an unauthenticated file upload vulnerability in the Metadata Uploader component of the SAP NetWeaver Visual Composer Framework version 7.50. It has been allocated the highest severity score by SAP, 10.0 (CVSS v3.1).
When exploited, it allows an unauthenticated attacker to upload potentially malicious executable binaries that could severely harm the host system.
First detected by ReliaQuest on April 22, the vulnerability was publicly disclosed by SAP two days later in a security advisory in which the software maker also released a patch. The advisory is only available to SAP customers.
Evidence of exploitation began to appear quickly. Notably, the Shadowserver Foundation found that over 400 NetWeaver servers were openly exposed to the internet.
Other private security companies, including Onapsis and WatchTowr, have found further proof of in-the-wild exploitation of CVE-2025-31324, stating that the attackers were uploading web shell backdoors on unpatched instances exposed online.
On April 27, Onapsis, in collaboration with Google Cloud-owned Mandiant, released an open-source tool to identify indicators of compromise on potentially affected SAP systems.
On April 29, the US Cybersecurity and Infrastructure Security Agency (CISA) added CVE-2025-31324 to its Known Exploited Vulnerabilities (KEV) catalog.
SAP also publicly disclosed another flaw, CVE-2025-42999, on May 13. This critical flaw (CVSS v3.1 base score of 9.1) is linked to CVE-2025-31324 and affects SAP NetWeaver Visual Composer.
Private vulnerability intelligence firm VulnCheck had previously added CVE-2025-42999 to its own KEV list.
Chinese Nation-State Exploit CVE-2025-31324
Researchers from Forescout’s Federe Labs published a report on May 8 stating that they had uncovered evidence indicating that a Chinese nation-state threat actor was likely involved in malicious campaigns exploiting CVE-2025-31324.
“We uncovered malicious infrastructure likely belonging to a Chinese threat actor, which we are currently tracking as Chaya_004. The infrastructure includes a network of servers hosting Supershell backdoors, often deployed on Chinese cloud providers, and various pen testing tools, many of Chinese origin,” said the report.
Attacks detected by Federe Labs were launched from IP addresses that utilized anomalous self-signed certificates impersonating Cloudflare. Many of these IP addresses belonged to Chinese cloud providers, including Alibaba, Shenzhen Tencent, Huawei Cloud Service and China Unicom.
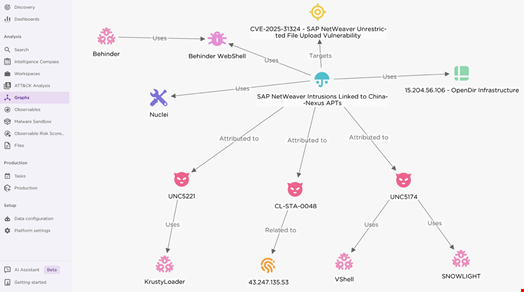
Another company, EclectiIQ, confirmed in a May 13 report that its analysts have assessed “with high confidence” that some observed SAP NetWeaver intrusions are linked to Chinese cyber-espionage units, including UNC5221, UNC5174 and CL-STA-0048, based on threat actor tradecraft patterns.
According to Mandiant and Palo Alto, these groups are associated with China’s Ministry of State Security (MSS) or affiliated private entities.
Ransomware Groups Exploit CVE-2025-31324
Alongside the Chinese threat actor, ReliaQuest stated in a May 14 update that it had observed two ransomware groups associated with malicious exploitation campaigns.
ReliaQuest researchers assessed “with moderate confidence” that BianLian was involved in at least one incident where CVE-2025-31324 exploitation was evident.
“We identified a server at 184[.]174[.]96[.]74 hosting reverse proxy services initiated by the rs64.exe executable. This server is related to another IP, 184[.]174[.]96[.]70, operated by the same hosting provider. The second IP had previously been flagged as a command-and-control (C2) server associated with BianLian, sharing identical certificates and ports,” the researchers explained.
Additionally, they observed a separate incident in which attackers exploited the SAP NetWeaver vulnerability and deployed ‘PipeMagic,’ a modular backdoor linked to RansomEXX (tracked by Microsoft as Storm-2460).
“Delivered through MSBuild abuse, PipeMagic uses the EnumCalendarA API callback methodology, with sandbox analysis confirming beaconing to aaaaabbbbbbb[.]eastus[.]cloudapp[.]azure[.]com, a domain tied to both PipeMagic and RansomEXX,” said the ReliaQuest report.
The involvement of groups like BianLian and RansomEXX reflects the growing interest in weaponizing high-profile vulnerabilities for financial gain.
These developments emphasize the urgent need for organizations to immediately apply patches, monitor suspicious activity and strengthen defenses.
Photo credits: Kittyfly/Shutterstock

