- IBM’s cloud crisis deepens: 54 services disrupted in latest outage
- Proton VPN vs. Private Internet Access: Which VPN should you choose?
- Moderna’s HR-IT merger: Trend or exception to the rule?
- I tested Google's Veo 2 video generator on an Android phone - the results left me very conflicted
- AMD acquires Brium to loosen Nvidia’s grip on AI software
Scammers exploiting Kaseya ransomware attack to deploy malware

A new phishing campaign claims to offer a security update for Kaseya’s VSA software but actually tries to install malware, says Malwarebytes.
Image: danijelala, Getty Images/iStockPhoto
Cybercriminals are already taking advantage of the ransomware attack against IT firm Kaseya to deploy spam designed to infect computers with Cobalt Strike-delivered malware. In a July 6 update to an ongoing blog and a tweet about the Kaseya incident, security firm Malwarebytes said that its Threat Intelligence team has detected a malicious spam campaign exploiting the Kaseya VSA attack.
SEE: Ransomware: What IT pros need to know (free PDF) (TechRepublic)
The phishing email sent out in this campaign claims to offer a fix for the Kaseya security flaw, telling the recipient: “Please install the update from microsoft to protect against ransomware as soon as possible. This is fixing a vulnerability in Kaseya.”
The email carries a file attachment named SecurityUpdates.exe. But anyone who attempts to run the attached file will instead be treated to a dose of malware courtesy of penetrating testing tool Cobalt Strike.
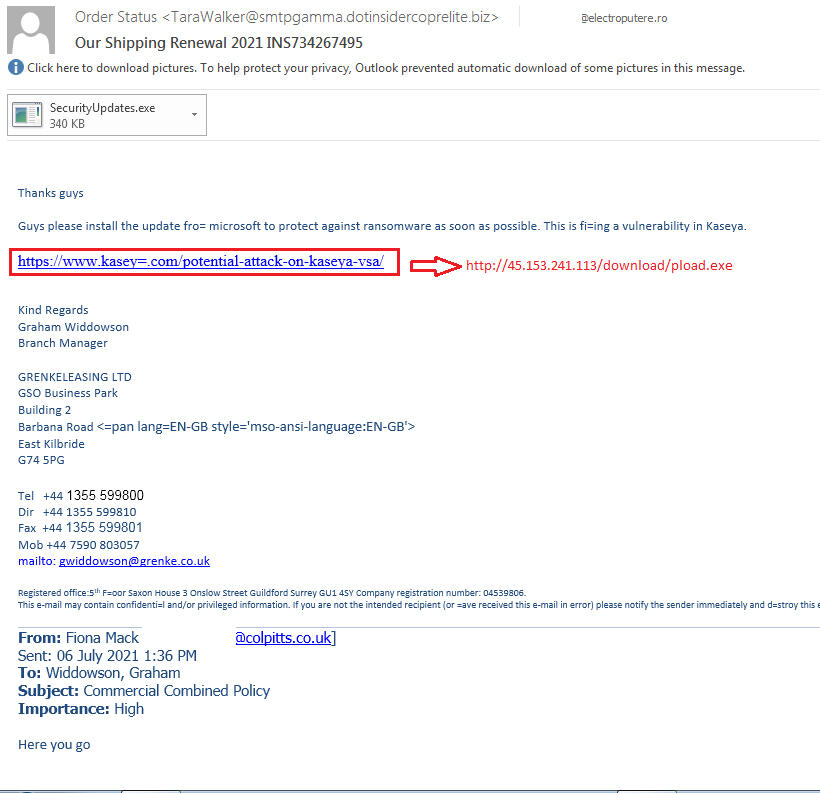
Image: Malwarebytes
Designed and intended as a legitimate security program, Cobalt Strike is used by organizations to test their internal security to look for weak spots. But the tool has increasingly been co-opted by cybercriminals to deploy malicious payloads onto victimized computers. The program has been popular among major cybercrime groups and advanced persistent threat groups but has recently gained greater traction among general commodity criminals.
Typically, attackers download Cobalt Strike as a second stage after the initial compromise. But lately there’s been an increase in campaigns pushing Cobalt Strike as a first payload to set the stage for the attack.
This Kaseaya fake update is hosted on the same IP address used for a past campaign pushing the Dridex banking trojan, according to Jerome Segura, lead malware intelligence analyst for Malwarebytes. Segura said Malwarebytes has seen the same threat actor behind Dridex using Cobalt Strike but couldn’t confirm the group behind this new campaign.
On July 3, Kaseya revealed that its VSA product had been the victim of a ransomware attack. Used by Managed Service Providers, the software allows users to remotely monitor and administer IT services for their customers. The ransomware exploits a zero-day vulnerability in the VSA software, delivering the malicious payload through a fake VSA update.
SEE: How to manage passwords: Best practices and security tips (free PDF) (TechRepublic)
The attack directly infected less than 60 Kaseya customers, all of whom were running the VSA on-premises product. However, a ripple effect throughout the Kaseya supply chain meant that those infected systems then infected the systems of around 1,500 customers, according to Kaseya.
Proudly taking responsibility for the attack was ransomware group REvil. In its own “Happy Blog,” the group claimed that more than 1 million systems were infected, according to security firm Sophos. REvil also devised a captivating offer for all victims of the attack. In exchange for $70 million worth of bitcoin, the group would post a universal decryptor that would allow all affected companies to recover their files.
Kaseya has been working on a patch to fix the vulnerability in its VSA software. But the company has apparently run into glitches. Late Tuesday, Kaseya revealed that an issue was discovered that blocked the launch of the patch during deployment, pushing back the timeline for its release. In an update to its blog, the company said it would announce the new planned availability of the patch by 5 p.m. Eastern time on Wednesday.
“Cybercriminals routinely capitalize on panic stemming from newsworthy events,” said Chris Clements, VP of solutions architecture for Cerberus Sentinel. “We saw it with COVID stimulus checks, vaccine availability and now with the Kaseya supply chain attack.”
To help organizations protect themselves against these types of scams, Clements said that it’s important for users to vet any sources of information to make sure they’re accurate before they open attachments or share sensitive information. Phishing emails are a numbers game before one bypasses a security filter and arrives in a user’s mailbox, Clements added.
“Even the best anti-malware solutions can be deceived by clever binary obfuscation techniques,” Clements said. “As such, it’s critical to have layers of controls that anticipate failures of other controls. This is where continuous monitoring and proactive threat hunting really shine by providing the capability to identify potentially suspicious activities that manage to evade primary defenses.”


