- What to Do If You Book a Hotel or Airbnb and It Turns Out to Be a Scam | McAfee Blog
- Cómo evitar la fuga de cerebros en TI
- Is ChatGPT Plus still worth $20 when the free version packs so many premium features?
- How this 'FinOps for AI' certification can help you tackle surging AI costs
- ChatGPT can record, transcribe, and analyze your meetings now
Security Advisory: CVE-2022-42889 “Text4Shell” — Docker

What is it?
CVE-2022-42889, aka “Text4Shell”, is a vulnerability in the popular Java library “Apache Commons Text” which can result in arbitrary code execution when processing malicious input. More information can be found at GitHub advisory or this Apache thread.
What can an attacker do?
If you’re vulnerable, an attacker can inject malicious input containing keywords which can trigger:
- a DNS request
- a call to a remote URL
- an inline script to execute
These three mechanisms will be executed on the server and can trigger arbitrary code to execute, pulling code from external sources or embedding arbitrary scripts.
This makes this vulnerability highly serious, although, in many cases, consumers of this library won’t be vulnerable due to not using the StringSubstitutor class (as below) and/or not passing in untrusted input into vulnerable functions.
Security researchers are also reporting that increased and significant activity to exploit this vulnerability is being recorded.
Am I vulnerable?
To be vulnerable, you must:
- Use Apache Commons Text version 1.5-1.9 inclusive
- Have code using the
StringSubstitutorclass with variable interpolation - Have a mechanism of accepting input and passing it into the StringSubstitutor class
Docker vulnerability scanning tools including the docker scan CLI and Docker Hub Vulnerability Scanning, powered by Snyk, will detect the presence of the vulnerable versions of the library and flag your image as vulnerable (see below).
Note that you may not be vulnerable even if you’re using these versions, as your code paths may already mitigate this by either not using the vulnerable methods, or by not passing in user input into them (see the Mitigations section below). This may be difficult to validate, however, without understanding all the code paths in detail and where they may get input from. So the easiest fix is simply to upgrade all applications depending on vulnerable versions.
You can use docker scan to check if the image has the vulnerability. If Text4Shell is present you will see a message in the output log like this:
Upgrade org.apache.commons:[email protected] to org.apache.commons:[email protected] to fix
✗ Arbitrary Code Execution (new) [High Severity][https://security.snyk.io/vuln/SNYK-JAVA-ORGAPACHECOMMONS-3043138] in org.apache.commons:[email protected]
introduced by org.apache.commons:[email protected]To test this, you can check a vulnerable image, for example this neo4j image contains a vulnerable version of commons-text at /var/lib/neo4j/lib/commons-text-1.9.jar:
docker scan neo4j:[email protected]:17334cbc668d852ca8a3d8590f66c4fda64d9c7de7d93cc62803f534ae7dbce6Docker Hub scans
As of 12:00 UTC 21 October 2022, Docker Hub now identifies the Text4Shell vulnerability and will badge any image it finds vulnerable. This badge will be publicly visible for Docker Official Images and Docker Verified Publisher images, and privately visible for any other images with vulnerability scanning enabled.
Scans before this date may not reflect this vulnerability, however, we will continue to scan older Docker Official and Docker Verified Publisher images and will update the badges as the results are checked.
If an image has been scanned and is found to be affected by the Text4Shell vulnerability, then you’ll see the below badging and information next to the image:
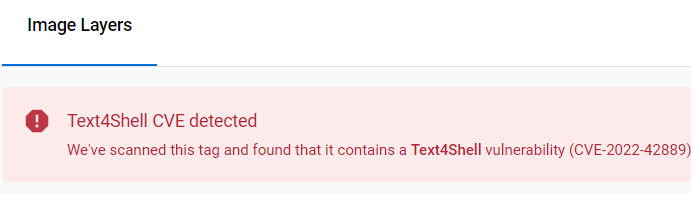
Mitigations
The safest mitigation to execute is to update to version 1.10 of Apache Commons Text.
If updating to this version isn’t possible, the secondary mitigation is to check usage closely across your codebase and ensure untrusted user input isn’t being passed to the vulnerable functions.
Docker Official Images
A number of the Docker Official images do contain the vulnerable versions of Apache Commons Text. These will be publicly labeled in the Docker Hub user interface. For more detailed information on the current status of Docker Official Images please see https://docs.docker.com/security/.
Other images
We’re working with the Docker Verified Publishers to identify and update their affected images. We’re also looking at ways to highlight images that are affected, and we’ll continue to update this post as we have more information.
Is Docker infrastructure affected?
Docker Desktop and Docker Hub are not affected by the Text4Shell vulnerability. Docker largely uses Go code to build our applications, not Java. Although we do use some Java applications, we have confirmed we aren’t vulnerable to CVE-2022-42889.

