- Your Samsung Galaxy Watch is about to get a big upgrade for free - try 4 cool new features now
- Cisco Customer Achievement Award Winners Recognized at Cisco Live San Diego 2025
- Your TV's USB port is criminally underrated: 5 features you're not using enough
- T-Mobile will give you a Samsung Galaxy S25 Plus for free - how to qualify for the deal
- AI-Ready Optics Transceivers Partner Enablement Campaign
Stealth Backdoor “Android/Xamalicious” Actively Infecting Devices | McAfee Blog
Authored by Fernando Ruiz
McAfee Mobile Research Team identified an Android backdoor implemented with Xamarin, an open-source framework that allows building Android and iOS apps with .NET and C#. Dubbed Android/Xamalicious it tries to gain accessibility privileges with social engineering and then it communicates with the command-and-control server to evaluate whether or not to download a second-stage payload that’s dynamically injected as an assembly DLL at runtime level to take full control of the device and potentially perform fraudulent actions such as clicking on ads, installing apps among other actions financially motivated without user consent.
The second stage payload can take full control of the infected device due to the powerful accessibility services that were already granted during the first stage which also contains functions to self-update the main APK which means that it has the potential to perform any type of activity like a spyware or banking trojan without user interaction. However, we identified a link between Xamalicious and the ad-fraud app “Cash Magnet” which automatically clicks ads, installs apps, and other actions to fraudulently generate revenue while users that installed it may earn points that are supposed to be redeemable as a retail gift card. This means that the developers behind these threats are financially motivated and drive ad-fraud therefore this might be one of the main payloads of Xamalicious.
The usage of the Xamarin framework allowed malware authors to stay active and without detection for a long time, taking advantage of the build process for APK files that worked as a packer to hide the malicious code. In addition, malware authors also implemented different obfuscation techniques and custom encryption to exfiltrate data and communicate with the command-and-control server.
We’ve identified about 25 different malicious apps that carry this threat. Some variants have been distributed on Google Play since mid-2020. The apps identified in this report were proactively removed by Google from Google Play ahead of our reporting. McAfee is a member of the App Defense Alliance and an active partner in the malware mitigation program, which aims to quickly find Potentially Harmful Applications (PHAs) and stop them before they ever make it onto Google Play. Android users are protected by Google Play Protect, which can warn users of identified malicious apps on Android devices. McAfee Mobile Security detects this threat as Android/Xamalicious.
Based on the number of installations these apps may have compromised at least 327,000 devices from Google Play plus the installations coming from third-party markets that continually produce new infections based on the detection telemetry of McAfee clients around the world. This threat remains very active.
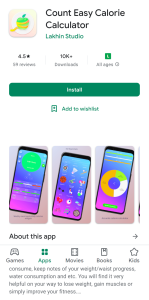
Figure 1. “Count Easy Calorie Calculator” was available on Google Play on August 2022 and carries Android/Xamalicious
Android/Xamalicious trojans are apps related to health, games, horoscope, and productivity. Most of these apps are still available for download in third-party marketplaces.
Previously we detected malware abusing Xamarin framework such as the open-sourced AndroSpy and forked versions of it, but Xamalicious is implemented differently. Technical details about Xamarin architecture are well documented and detail how .NET code is interpreted by Android using Mono.
Obtaining Accessibility Services
Let’s use the app “Numerology: Personal horoscope & Number predictions” as an example. Once started it immediately requests the victim to enable accessibility services for “correct work” and provides directions to activate this permission:
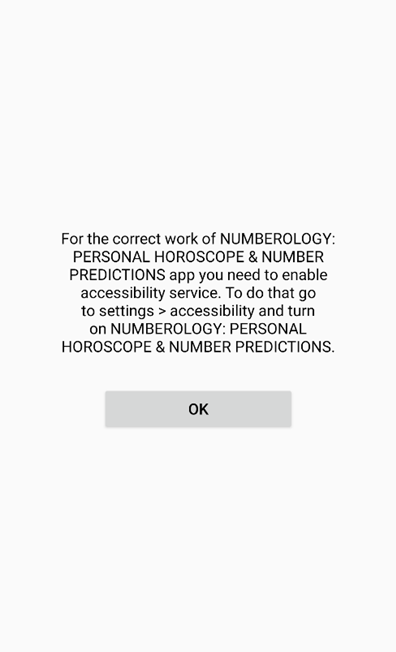
Figure 2. Tricking users into granting accessibility services permission
Users need to manually activate the accessibility services after several OS warnings such as the following on the accessibility options:
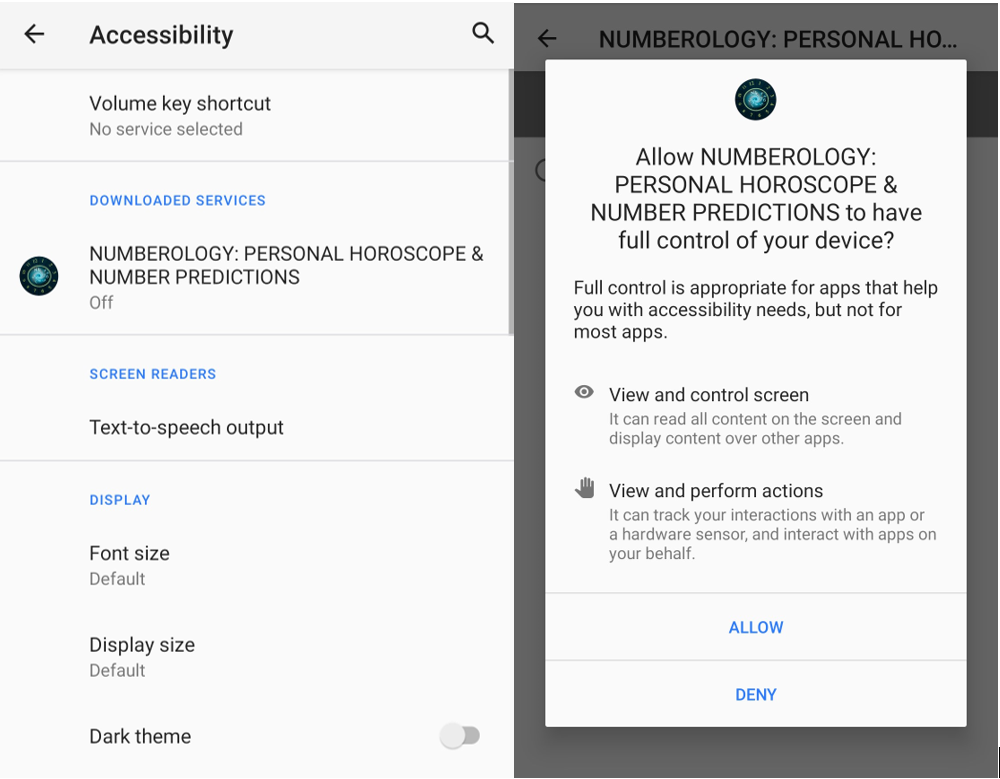
Figure 3. Accessibility services configuration prompt highlights the risks of this permission.
Where is the malicious code?
This is not the traditional Java code or native ELF Android application, the malware module was written originally in .NET and compiled into a dynamic link library (DLL). Then it is LZ4 compressed, and it might be embedded into a BLOB file, or directly available in the /assemblies directory on the APK structure. This code is loaded then by a native library (ELF) or by the DEX file at runtime level. In simple words, this means that in some samples the reversing of the DLL assemblies is straightforward while in others it requires extra steps to unpack them.
The malicious code is usually available in two different assembly files in the /assemblies directory on the apk. Usually, file names are core.dll and a <package-specific>.dll.
Some malware variants has obfuscated the DLL assemblies to avoid analysis and reversing of the malicious code while others keep the original code available.
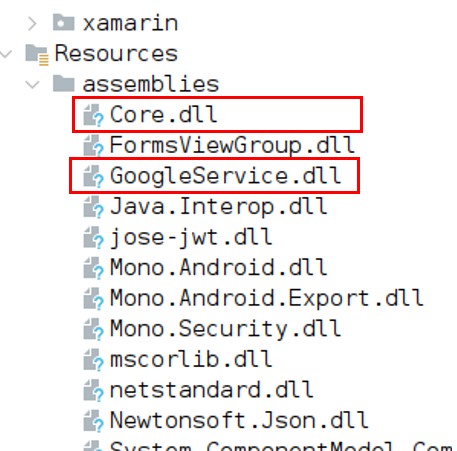
Figure 4. Core.dll and GoogleService.dll contain malicious code.
Communication with the command-and-control server
Once accessibility permissions are granted the malware initiates communication with the malicious server to dynamically load a second-stage payload.
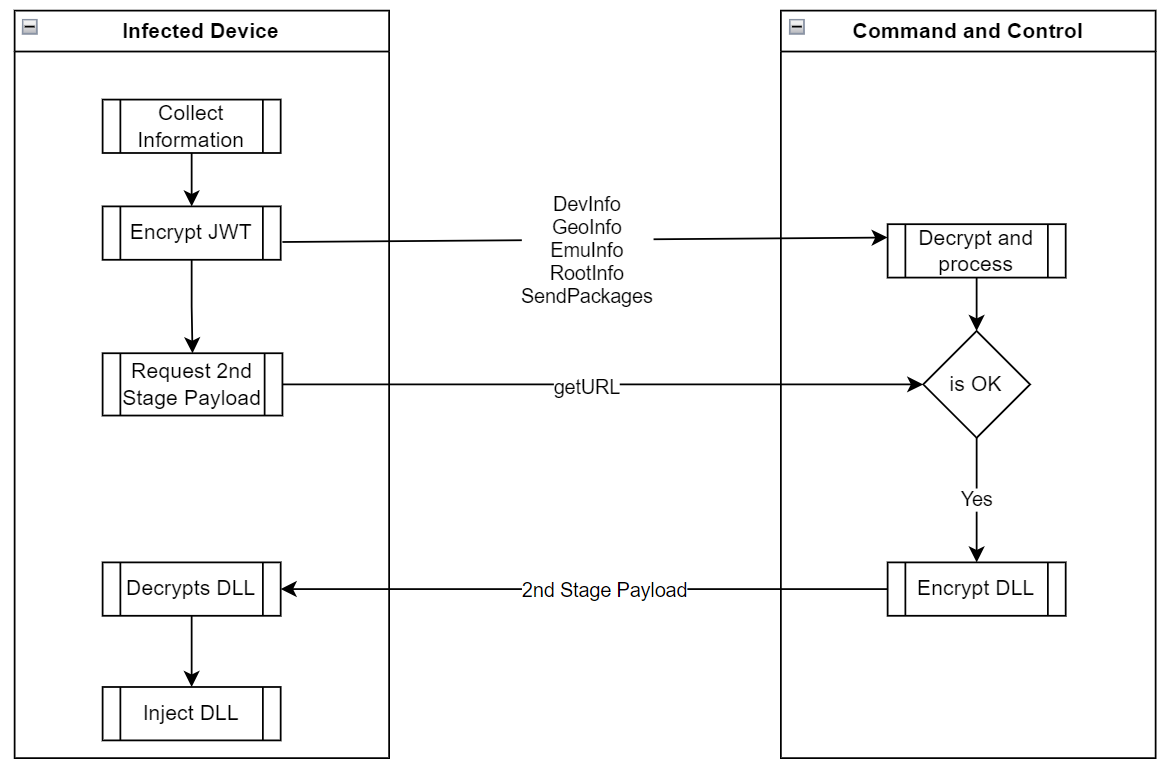
Figure 5. App execution and communication with the malicious server
Collect Device Information
Android/Xamalicious collects multiple device data including the list of installed applications obtained via system commands to determine if the infected victim is a good target for the second stage payload. The malware can collect location, carrier, and network information among device rooting status, adb connectivity configuration, for instance, if the device is connected via ADB or is rooted, the C2 will not provide a second-stage payload DLL for download.
| Method/Command | Description |
| DevInfo | Hardware and device information that includes:
|
| GeoInfo | Location of the device based on IP address, the malware contacts services such as api.myip.com to verify the device location and ISP data.
FraudScore: Self-protection to identify if the device is not a real user |
| EmuInfo | It lists all adbProperties that in a real device are around 640 properties. This list is encoded as a string param in URL encoded format.
This data may be used to determinate if the affected client is a real device or emulator since it contains params such as:
|
| RootInfo | After trying to identify if the device is rooted or not with multiple techniques the output is consolidated in this command |
| Packages | It uses the system commands “pm list packages -s” and “pm list packages -3” to list system and installed apps on the device. |
| Accessibility | It provides the status if accessibility services permissions are granted or not |
| GetURL | This command only provides the Android Id and it’s a request for the second-stage payload. The C2 evaluates the provided client request and returns a status and an encrypted assembly DLL. |
Data Encryption in JWT
To evade analysis and detection, malware authors encrypted all communication and data transmitted between the C2 and the infected device, not only protected by HTTPS, it’s encrypted as a JSON Web Encryption (JWE) token using RSA-OAEP with a 128CBC-HS256 algorithm however the RSA key values used by the Xamalicious are hardcoded in the decompiled malicious DLL so decryption of transmitted information is possible if C2 infrastructure is available during the analysis.
In the Send() function Android/Xamalicious first prepares the received object, usually a JSON structure calling the function encrypt() which creates the JWT using a hardcoded RSA key. So the data is exfiltrated fully encrypted to the malware host pointing to the path “/Updater” via HTTP POST method.
Then it waits for the C2 response and passes it to the decrypt() function which has a hardcoded RSA private key to properly decrypt the received command which might contain a second stage payload for the “getURL” command.
Encrypt Method:
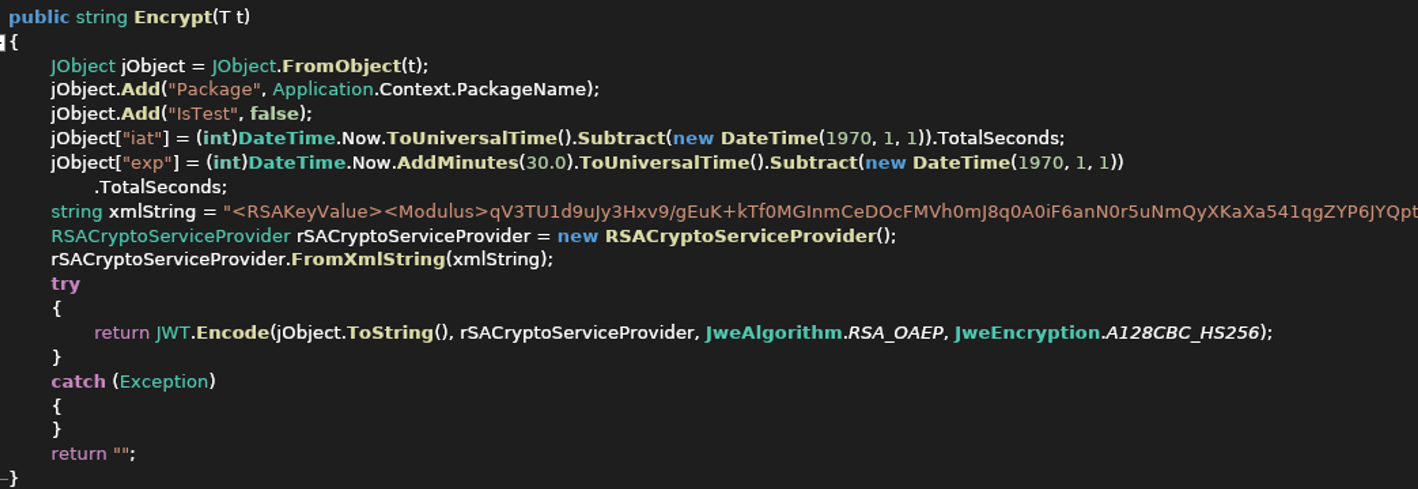
Figure 6. Encrypt function with hardcoded RSA Key values as XML string
The decryption method is also hardcoded into malware which allowed the research team to intercept and decrypt the communication from the C2 using the RSA key values provided as XML string it’s possible to build a certificate with the parameters to decrypt the JWE tokens content.
C2 evaluation
Collected data is transmitted to the C&C to determine if the device is a proper target to download a second-stage payload. The self-protection mechanism of the malware authors goes beyond traditional emulation detection and country code operator limitations because in this case, the command-and-control server will not deliver the second stage payload if the device is rooted or connected as ADB via USB or does not have a SIM card among multiple other environment validations.
DLL Custom Encryption
With the getURL command, the infected client requests the malicious payload, if the C&C Server determines that the device is “Ok” to receive the malicious library it will encrypt a DLL with Advanced encryption standard (AES) in Cipher block chaining (CBC) using a custom key for the client that requested it based on the device id and other parameters explained below to decrypt the code since it’s a symmetric encryption method, the same key works for encryption and decryption of the payload.
Delivers the Payload in JWT
The encrypted DLL is inserted as part of the HTTP response in the encrypted JSON Web Token “JWT”. Then the client will receive the token, decrypt it, and then decrypt the ‘url’ parm with AES CBC and a custom key.
The AES key used to decrypt the assembly is unique per infected device and its string of 32 chars of length contains appended the device ID, brand, model, and a hardcoded padding of “1” up to 32 chars of length.
For instance, if the device ID is 0123456ABCDEF010 and the affected device is a Pixel 5, then the AES key is: “0123456ABCDEF010googlePixel 5111”
This means that the DLL has multiple layers of encryption.
- It’s a HTTPS protected.
- It’s encrypted as a JWE Token using RSA-OAEP with a 128CBC-HS256 algorithm.
- URL parameter that contains the DLL is encrypted with AES and encoded as base64
All these efforts are related to hiding the payload and trying to stay under the radar where this threat had relative success since some variants might have been active years ago without AV detections.
DLL Injected
Xamalicious will name this DLL “cache.bin” and store it in the local system to finally dynamically load it using the Assembly.Load method.
Once the second stage payload has been loaded the device can be fully compromised because once accessibility permissions are granted, it can obverse and interact with any activity opening a backdoor to any type of malicious activity.
During the analysis, the downloaded second stage payload contained a DLL with the class “MegaSDKXE” which was obfuscated and incomplete probably because the C2 didn’t receive the expected params to provide the complete malicious second stage that might be limited to a specific carrier, language, app installed, location, time zone or unknown conditions of the affected device, however, we can assure that this is a high-risk backdoor that leaves the possibility to dynamically execute any command on the affected device not limited to spying, impersonation or as a financially motivated malware.
Cash Magnet Ad-Fraud and Xamalicious
One of the Xamalicious samples detected by McAfee Mobile generic signatures was “LetterLink” (com.regaliusgames.llinkgame) which was available on Google Play at the end of 2020, with a book icon. It was poorly described as a hidden version of “Cash Magnet”: An app that performs ad-fraud with automated clicker activity, apps downloads, and other tasks that lead to monetization for affiliate marketing. This application offers users points that are supposed to be redeemable by retail gift cards or cryptocurrency.
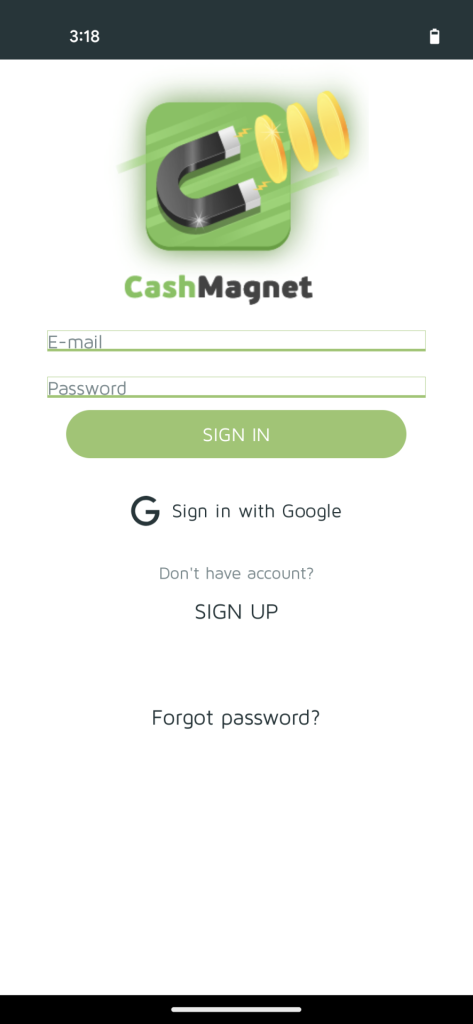
Figure 8a. LetterLink login page after running the app for the first time.
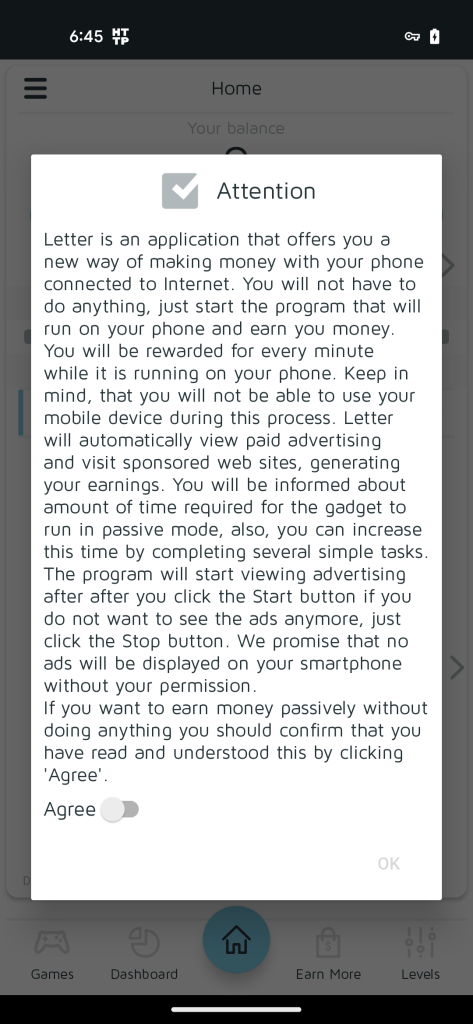
Figure 8b. LetterLink agreement for Cash Magnet
Originally published in 2019 on Google Play, “Cash Magnet” (com.uicashmagnet) was described as a passive income application offering users to earn up to $30 USD per month running automated ads. Since it was removed by Google the authors then infiltrated LetterLink and more recently “Dots: One Line Connector” (com.orlovst.dots) which are hidden versions of the same ad-fraud scheme.

Figure 9. LetterLink Icon that hides Cash Magnet
“LetterLink” performs multiple Xamalicious activities since it contains the “core.dll” library, it connects to the same C2 server, and it uses the same hardcoded private RSA certificate to build the JWE encrypted tokens which provide a non-repudiation proof that the developers of Cash Magnet are behind Xamalicious.
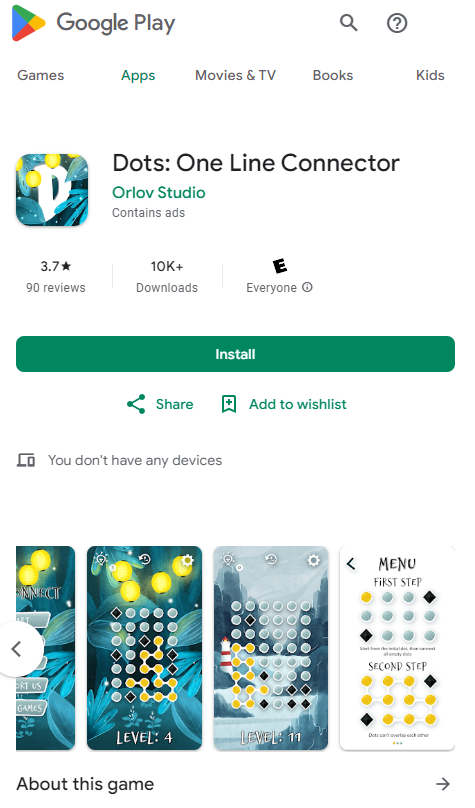
Figure 10. Cash Magnet infiltrated the app as a Game, available until the end of 2023
“Dots: One Line Connector” app is not a game, the screenshot published by Google Play does not correspond to the application behavior because once it is started it just asks for authentication credentials without any logo or reference to Cash Magnet. “Dots” does not contain the same DLLs as its predecessor, however the communication with the C2 is similar using the same RSA key parameters.
Affected Users
Based on our telemetry we observed that more affected users are in the American continent with the most activity in the USA, Brazil, and Argentina. In Europe, clients also reported the infection, especially in the UK, Spain, and Germany.
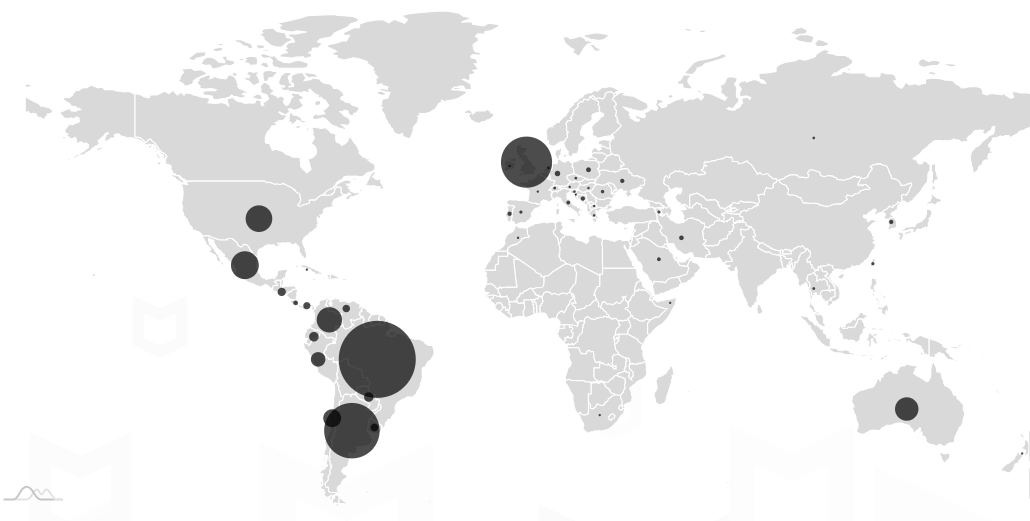
Figure 8. McAfee detections Android/Xamalicious around the world
Conclusion
Android applications written in non-java code with frameworks such as Flutter, react native and Xamarin can provide an additional layer of obfuscation to malware authors that intentionally pick these tools to avoid detection and try to stay under the radar of security vendors and keep their presence on apps markets.
Avoid using apps that require accessibility services unless there is a genuine need for use. If a new app tries to convince you to activate accessibility services claiming that it’s required without a real and reasonable reason and requesting to ignore the operative system warning, then it’s a red flag.
The second stage payload might take control of the device because accessibility permissions are granted so any other permission or action can then be performed by the malware if these instructions are provided in the injected code.
Because it is difficult for users to actively deal with all these threats, we strongly recommend that users install security software on their devices and always keep up to date. By using McAfee Mobile Security products, users can further safeguard their devices and mitigate the risks linked with these kinds of malware, providing a safer and more secure experience.
Android/Xamalicious Samples Distributed on Google Play:
| Package Name | App Name | Installs |
| com.anomenforyou.essentialhoroscope | Essential Horoscope for Android | 100,000 |
| com.littleray.skineditorforpeminecraft | 3D Skin Editor for PE Minecraft | 100,000 |
| com.vyblystudio.dotslinkpuzzles | Logo Maker Pro | 100,000 |
| com.autoclickrepeater.free | Auto Click Repeater | 10,000 |
| com.lakhinstudio.counteasycaloriecalculator | Count Easy Calorie Calculator | 10,000 |
| com.muranogames.easyworkoutsathome | Sound Volume Extender | 5,000 |
| com.regaliusgames.llinkgame | LetterLink | 1,000 |
| com.Ushak.NPHOROSCOPENUMBER | NUMEROLOGY: PERSONAL HOROSCOPE &NUMBER PREDICTIONS | 1,000 |
| com.browgames.stepkeepereasymeter | Step Keeper: Easy Pedometer | 500 |
| com.shvetsStudio.trackYourSleep | Track Your Sleep | 500 |
| com.devapps.soundvolumebooster | Sound Volume Booster | 100 |
| com.Osinko.HoroscopeTaro | Astrological Navigator: Daily Horoscope & Tarot | 100 |
| com.Potap64.universalcalculator | Universal Calculator | 100 |
Indicator of compromise
| SHA256 | Package Name |
| 63cb930ab83afe80d40ba620a0f2ed5e8a55cceec23bdad919bf9dfa3d8c6e5b | com.android.accessibility.service |
| 7149acb072fe3dcf4dcc6524be68bd76a9a2896e125ff2dddefb32a4357f47f6 | com.android.accessibility.service |
| a5de2dc4e6005e75450a0df0ea83816996092261f7dac30b5cf909bf6daaced0 | com.android.accessibility.service |
| 22803693c21ee17667d764dd226177160bfc2a5d315e66dc355b7366b01df89b | com.android.callllogbacup |
| efbb63f9fa17802f3f9b3a0f4236df268787e3d8b7d2409d1584d316dabc0cf9 | com.android.dreammusic |
| e801844333031b7fd4bd7bb56d9fb095f0d89eb89d5a3cc594a4bed24f837351 | com.android.statementsandservices |
| 6316edebe5995fc3e2715a44b78dcb2ec4f0409234851ee5dbb20c0fb60d1bf0 | com.android.tvresources |
| d3833f608e476ed24382bf3991cec503ebc7124481758bdb5e46390b367c1210 | com.android.ui.clock |
| 5fffb10487e718634924552b46e717bbcbb6a4f9b1fed02483a6517f9acd2f61 | com.android.ui.clock |
| 81a9a6c86b5343a7170ae5abd15f9d2370c8282a4ed54d8d28a3e1ab7c8ae88e | com.android.ui.clock |
| ac9bb11cf71b11d3d50620660b56f1612e10e4ee9f7fc5637c0c281a688ef978 | com.android.venting |
| 9c646516dd189cab1b6ced59bf98ade42e19c56fc075e42b85d597449bc9708b | com.android.version.shared |
| a4e7279daf2261d74e108be9ea46373777adb209de06d229cee1f77f7196bfdf | com.android.version.shared |
| 177ff9e281f96bf08ff9724e0c92cecc7538692cadc217cc2770c668b451f2dc | com.android.version.shared |
| 488942923780887114471dd0114ffb144deb8054773351b2b2aac3c974c569d8 | com.android.wall.lifetick |
| dfdca848aecb3439b8c93fd83f1fd4036fc671e3a2dcae9875b4648fd26f1d63 | com.anomenforyou.essentialhoroscope |
| e7ffcf1db4fb13b5cb1e9939b3a966c4a5a894f7b1c1978ce6235886776c961e | com.autoclickrepeater.free |
| 8927ff14529f03cbb2ebf617c298f291c2d69be44a8efa4e0406dea16e53e6f9 | com.autoclickrepeater.free |
| 117fded1dc51eff3788f1a3ec2b941058ce32760acf61a35152be6307f6e2052 | com.browgames.stepkeepereasymeter |
| 28a4ae5c699a7d96e963ca5ceec304aa9c4e55bc661e16c194bdba9a8ad847b7 | com.devapps.soundvolumebooster |
| b0b9a8e9ec3d0857b70464617c09ffffce55671b227a9fdbb178be3dbfebe8ed | com.kolomia.mineskineditor |
| 899b0f186c20fdbfe445b4722f4741a5481cd3cbcb44e107b8e01367cccfdda3 | com.lakhinstudio.counteasycaloriecalculator |
| e52b65fdcb77ed4f5989a69d57f1f53ead58af43fa4623021a12bc11cebe29ce | com.lakhinstudio.counteasycaloriecalculator |
| e694f9f7289677adaf2c2e93ba0ac24ae38ab9879a34b86c613dd3c60a56992d | com.littleray.skineditorforpeminecraft |
| 19ffe895b0d1be65847e01d0e3064805732c2867ce485dfccc604432faadc443 | com.muranogames.easyworkoutsathome |
| 6a3455ff881338e9337a75c9f2857c33814b7eb4060c06c72839b641b347ed36 | com.Osinko.HoroscopeTaro |
| e6668c32b04d48209d5c71ea96cb45a9641e87fb075c8a7697a0ae28929913a6 | com.Potap64.universalcalculator |
| 6953ba04233f5cf15ab538ae191a66cb36e9e0753fcaeeb388e3c03260a64483 | com.regaliusgames.llinkgame |
| f52917321b1010c0b145f699531947c84b26d63e91a5a67bf5131ba8904e1326 | com.shvetsstudio.newmapsforminecraftpe |
| cb8d4ae27b64c56831a4e9bb5f1d53a3a72eaea369ab7b40851009ed577d2b14 | com.shvetsStudio.trackYourSleep |
| 01c56911c7843098777ec375bb5b0029379b0457a9675f149f339b7db823e996 | com.shvetsStudio.trackYourSleep |
| f42e79c4dc6b1573731610a1135cb0a71152e869c598215f0db09958f2d761f5 | com.skladainc.phonedetectiveclaptofind |
| e55408ef4f10715e7a521e95df038114a75f865f5b2ac3c1dcfee2261724b5df | com.skladainc.phonedetectiveclaptofind |
| cc439631c09763003b92b80bbea2ff0f5d764694575ed7a9be155fbc420753db | com.skladainc.phonedetectiveclaptofind |
| 3201785a7de8e37e5d12e8499377cfa3a5b0fead6667e6d9079d8e99304ce815 | com.turovskyi.magicofnumbers |
| acb5de2ed2c064e46f8d42ee82feabe380364a6ef0fbfeb73cf01ffc5e0ded6b | com.Ushak.NPHOROSCOPENUMBER |
| 9b4dc1e80a4f4c798d0d87a52f52e28700b5b38b38a532994f70830f24f867ba | com.Ushak.NPHOROSCOPENUMBER |
| 1bfc02c985478b21c6713311ca9108f6c432052ea568458c8bd7582f0a825a48 | com.vyblystudio.dotslinkpuzzles |


