- This video doorbell camera has just as many features are my Ring - and no subscription required
- LG is giving away free 27-inch gaming monitors, but this is the last day to grab one
- I tested this Eufy security camera and can't go back to grainy night vision
- I replaced my iPhone with a premium dumbphone - here's my verdict after a month
- Build your toolkit with the 10 DIY gadgets every dad should have
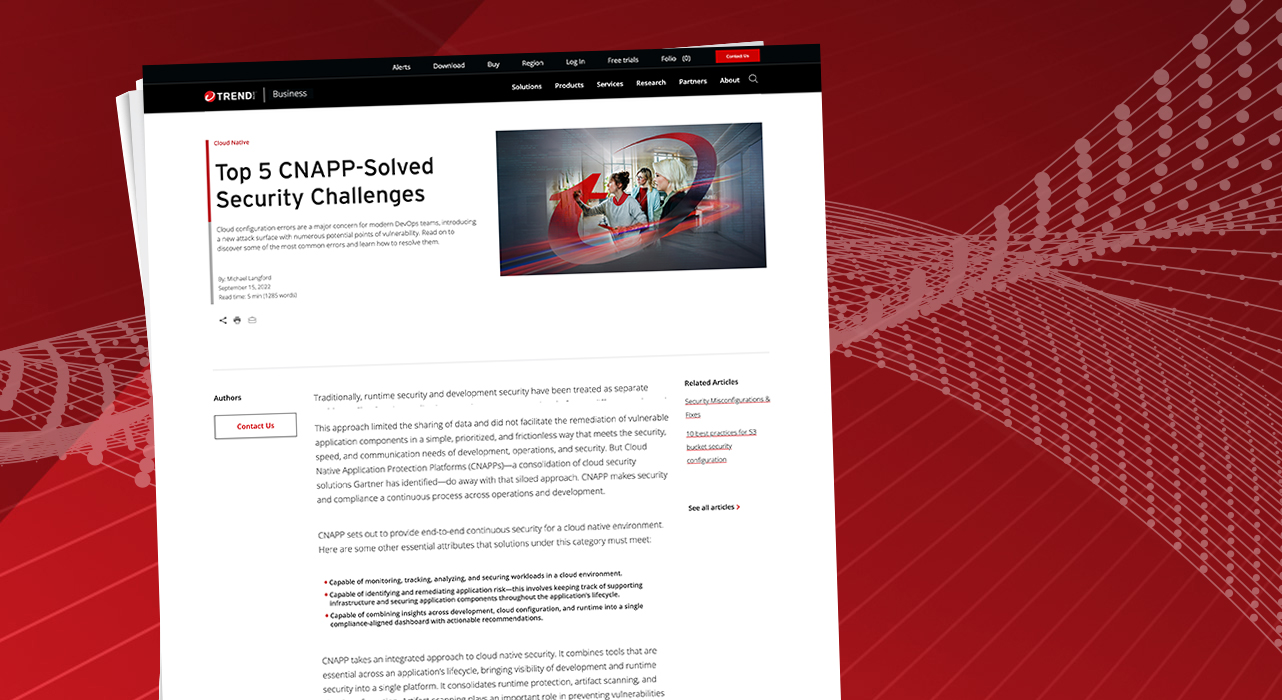
Top 5 CNAPP-Solved Security Challenges
Traditionally, runtime security and development security have been treated as separate problems. Cloud-native application security programs consisted of many different tools, each with its own objective, control panel, and view of risk. These tools were mainly event-driven—they would only initiate scans when alerts were raised. This approach limited the sharing of data and did not facilitate the remediation of vulnerable application components in a simple, prioritized, and frictionless way that meets the security, speed, and…
Read More