- I tested Hisense's flagship QLED TV and didn't miss my OLED set (especially when it's $700 off)
- Next-gen AI chips will draw 15,000W each, redefining power, cooling, and data center design
- Amazon extends July Prime Day to four day event, confirms 2025 dates
- Edge reality check: What we've learned about scaling secure, smart infrastructure
- Salesforce study warns against rushing LLMs into CRM workflows without guardrails
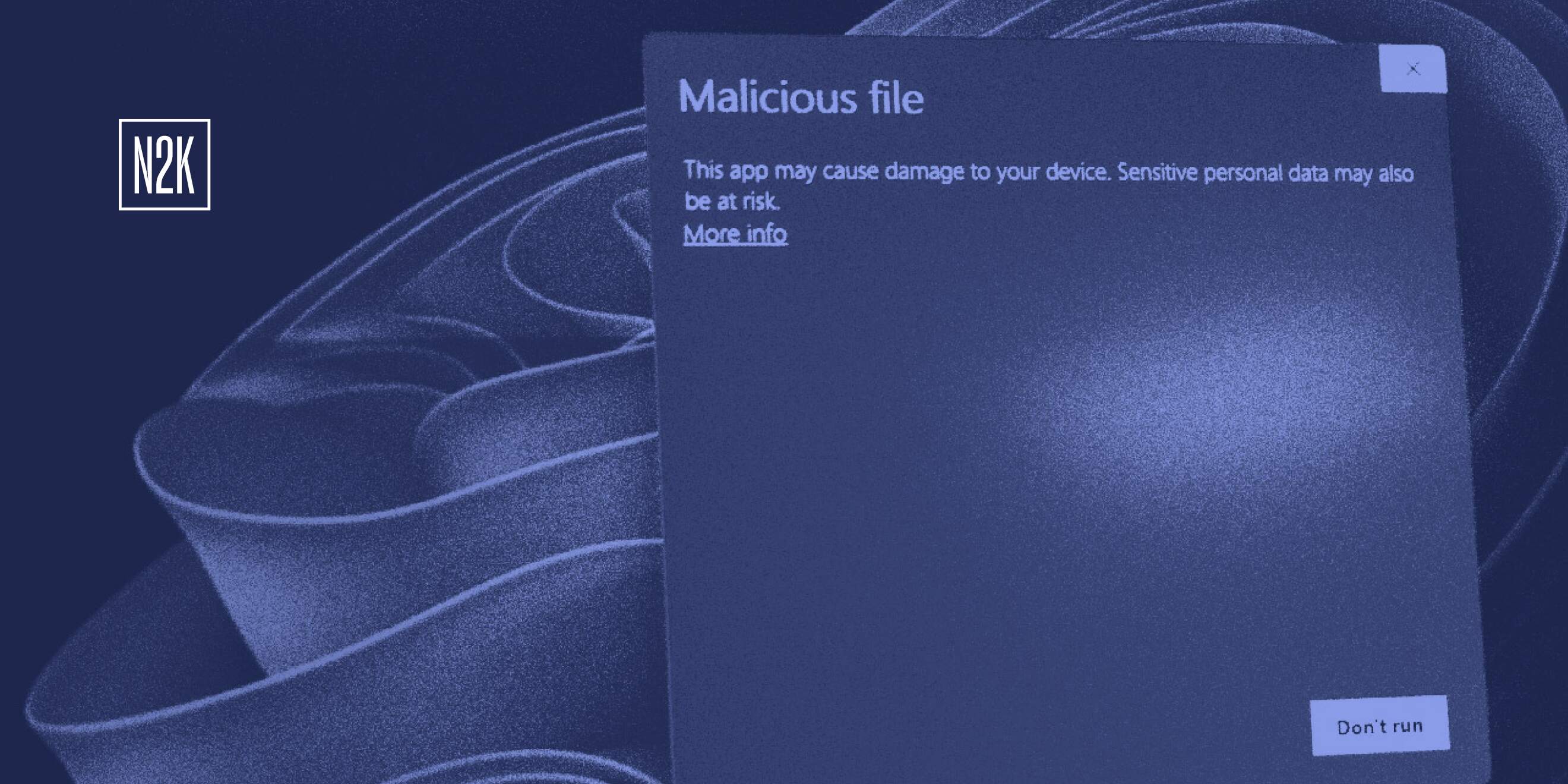
How to guard against the holiday cyberattack surge
Historical trends indicate a marked increase in cyberattacks during the holiday season. Cybercriminals take advantage of heightened online activity and digital transactions, using this busy period to target consumers with precision. However, it’s not just individual shoppers who are at risk — enterprises are equally vulnerable. In fact, recent research shows a staggering 550% surge in unique threats during this time of year. Organizations become prime targets for a wide array of cyberattacks as the…
Read More



.jpg?height=635&t=1714668895&width=1200)