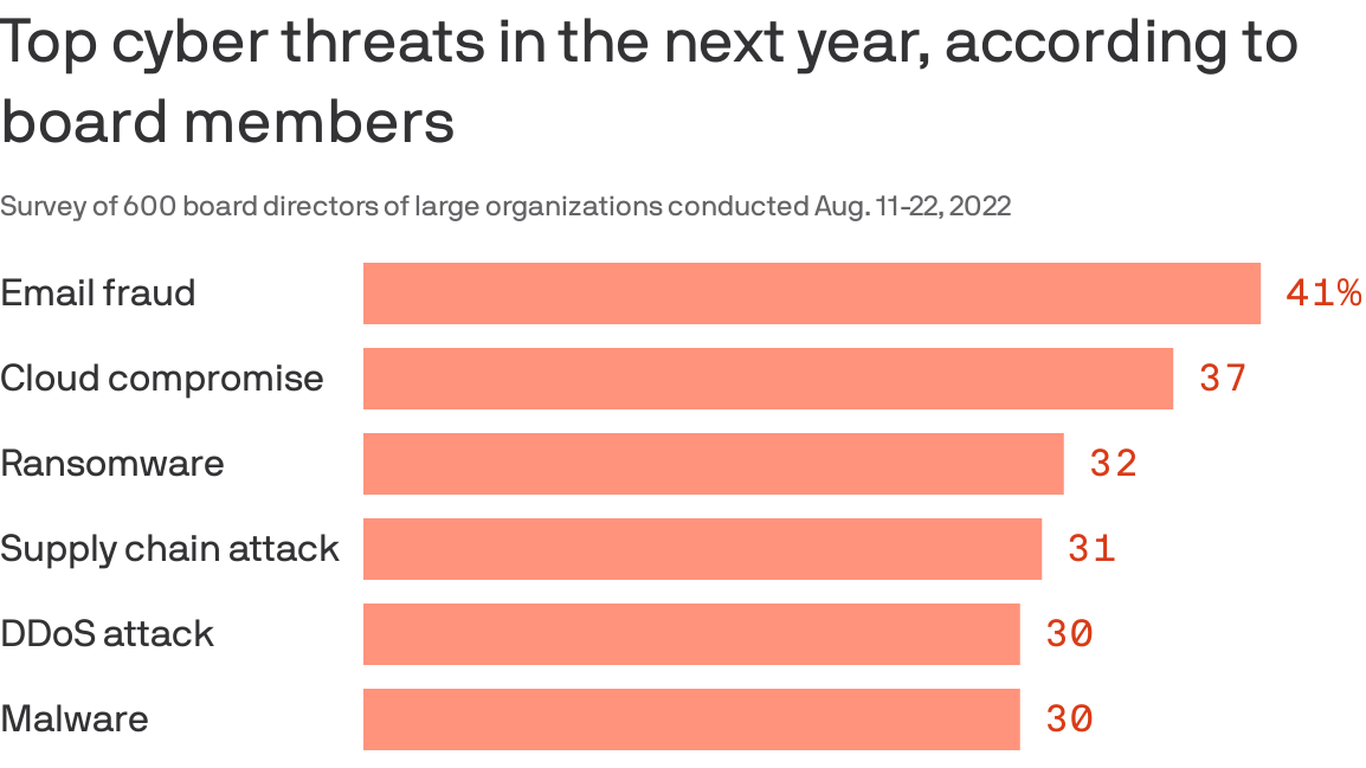
- Better Together: How MFA and Strong Password Practices Can Help Bolster Security
- “美 CISO 평균 연봉 6억,상위 1%는 60억원 넘어···보안 예산은 여전히 부족” IANS 설문조사
- 아웃시스템즈, 매출 5억 유로 돌파 및 신임 CEO 선임 발표
- 정철환 칼럼 | 변화의 바람에 맞설 것인가? 따를 것인가?
- Best home automation systems 2025: I'm a smart home reviewer and these are the top ones
The 5 pillars of cloud security for data storage
The 5 pillars of cloud security for data storage | Security Magazine This website requires certain cookies to work and uses other cookies to help you have the best experience. By visiting this website, certain cookies have already been set, which you may delete and block. By closing this message or continuing to use our site, you agree to the use of cookies. Visit our updated privacy and cookie policy to learn more. This…
Read More