- The Growing Threat of AI-powered Cyberattacks in 2025
- I test tablets for a living and this is the Samsung tablet I recommend the most
- The Cost of Ignoring Patches: How State and Local Governments Can Mitigate Damaging Security Breaches
- I turned this 98-inch TV into an immersive at-home theater system (and it's $1,500 off)
- You can save $30 on the Apple Pencil Pro right now
Get an Extra 20% Off a Lifetime of Powerful VPN Protection Through 4/7
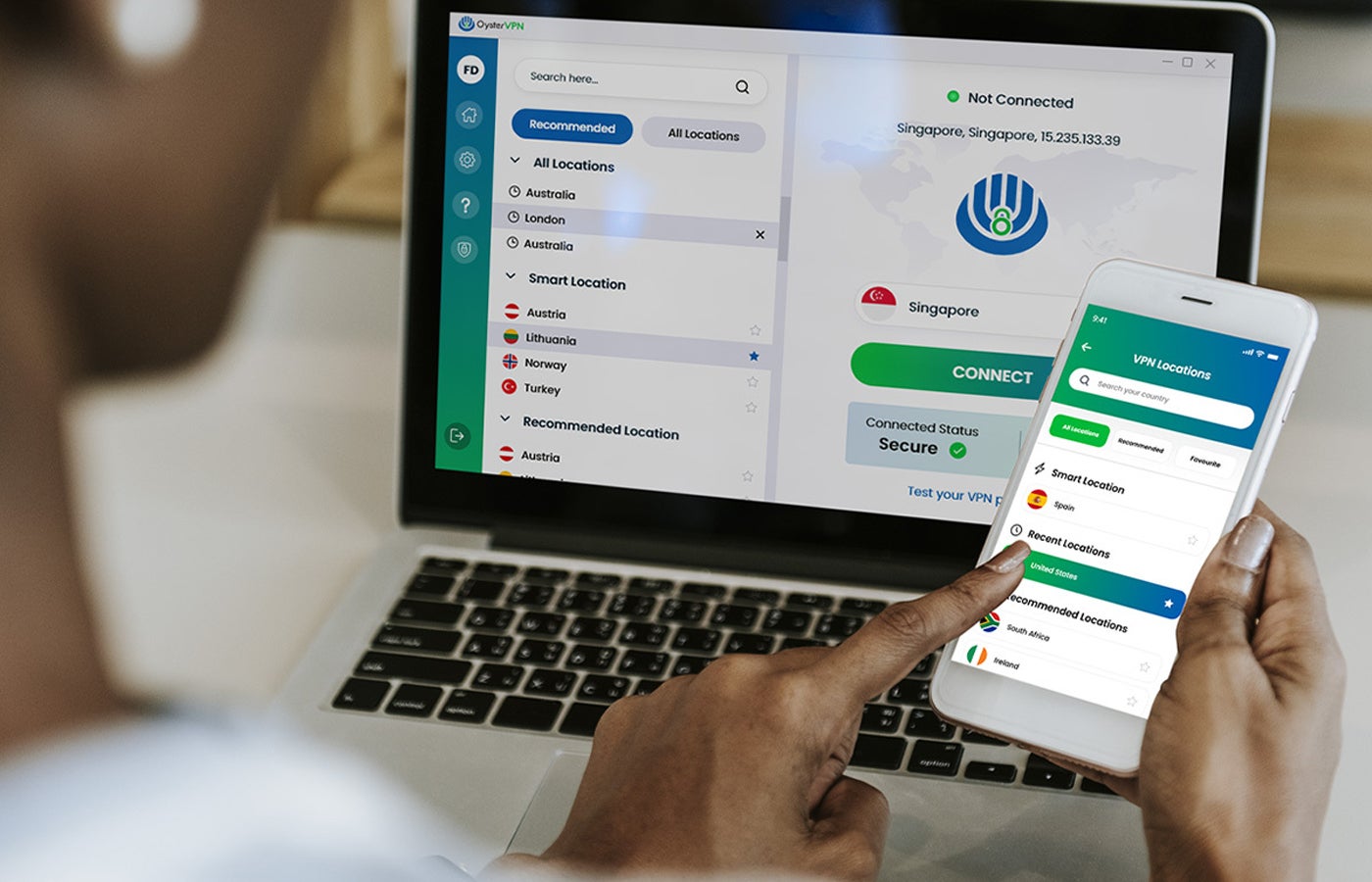
TL;DR: Protect your business’s data and privacy with a lifetime subscription to OysterVPN. It’s currently available to new users for the best-on-web price of just $32 with coupon code SECURE20 through April 7. There are three important reasons for businesses to use a VPN: to keep your work data safe from hackers, to protect your privacy by preserving anonymity online and to consume content that is inaccessible wherever you happen to be. However, not all…
Read More