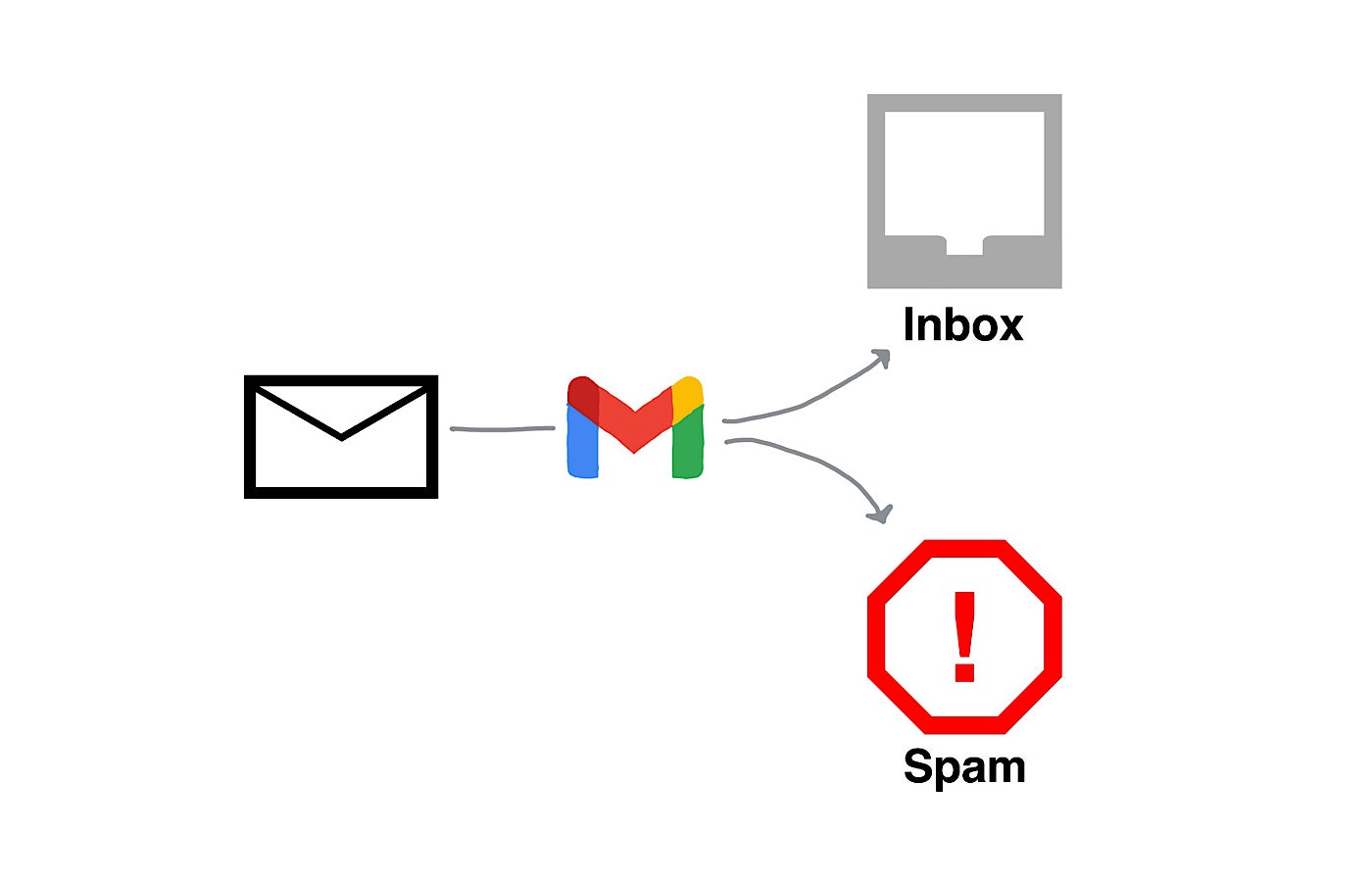
- This Week in Scams: $16.6 Billion Lost, Deepfakes Rise, and Google Email Scams Emerge | McAfee Blog
- Proof-of-concept bypass shows weakness in Linux security tools, claims Israeli vendor
- SAP NetWeaver customers urged to deploy patch for critical zero-day vulnerability
- Lenovo targets AI workloads with massive storage update
- Girls Power Tech Inspires the Next Generation of Tech Leaders
RSA: Google Enhances its Enterprise SecOps Offerings With Gemini AI
The RSA Conference, held in San Francisco from May 6-9, brings together cybersecurity professionals from across the world. This year’s conference is buzzing with conversation about generative AI: how to use generative AI to protect against attacks and how to secure generative AI itself. We’re rounding up the enterprise business tech news from RSA that is most relevant for IT and tech decision-makers. This article will be updated throughout RSA with more tech news highlights….
Read More