- The Growing Threat of AI-powered Cyberattacks in 2025
- I test tablets for a living and this is the Samsung tablet I recommend the most
- The Cost of Ignoring Patches: How State and Local Governments Can Mitigate Damaging Security Breaches
- I turned this 98-inch TV into an immersive at-home theater system (and it's $1,500 off)
- You can save $30 on the Apple Pencil Pro right now
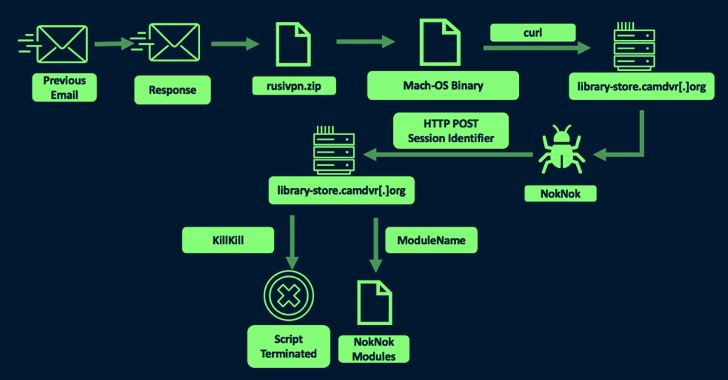
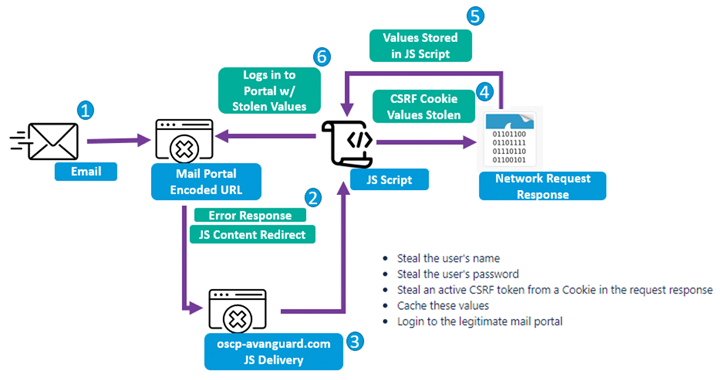
Cybercriminals Renting WikiLoader to Target Italian Organizations with Banking Trojan
Aug 01, 2023THNCyber Attack / Malware Organizations in Italy are the target of a new phishing campaign that leverages a new strain of malware called WikiLoader with an ultimate aim to install a banking trojan, stealer, and spyware referred to as Ursnif (aka Gozi). “It is a sophisticated downloader with the objective of installing a second malware payload,” Proofpoint said in a technical report. “The malware uses multiple mechanisms to evade detection and was likely…
Read More