- 中 수곤-하이곤 합병··· 분석가 “글로벌 HPC 생태계 재편 가능성”
- The best Chromebooks for students in 2025: Expert tested and reviewed
- The top-selling smartphone in 2025 so far might surprise you - here's why
- Apple Intelligence hasn't lived up to my expectations, but these 3 upgrades could win me back
- Samsung launches One UI 8 beta - what's new and how to join
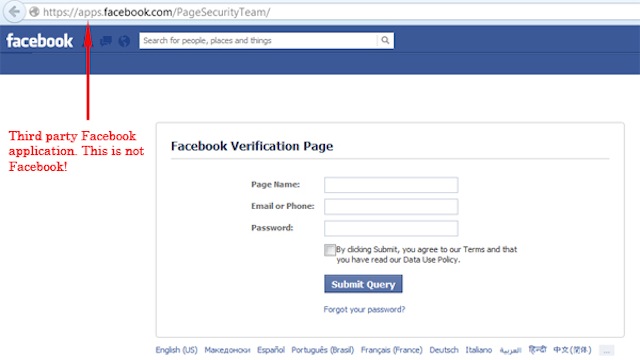
Android Malware Exploits a Microsoft-Related Security Blind Spot to Avoid Detection
This Motorola Moto G Power 5G shows the midnight blue color option. Image: Amazon New Android malware is using Microsoft’s .NET MAUI to fly under the radar in a new cybersecurity dust-up this week. Disguised as actual services such as banking and social media apps targeting Indian and Chinese-speaking users, the malware is designed to gain access to sensitive information. Cybersecurity experts with McAfee’s Mobile Research Team say that, while the threat is currently aimed…
Read More