- I've used virtually every Linux distro, but this one has a fresh perspective
- I replaced my JBL speaker with this surprise alternative. Here's why it's my new top pick
- I replaced my JBL speaker with this surprise alternative. Here's why it's my new top pick
- Every dad should build their toolkit with theses 10 DIY gadgets
- Broadcom grows revenues by 20% following VMware purchase, as customers fume about subscription costs
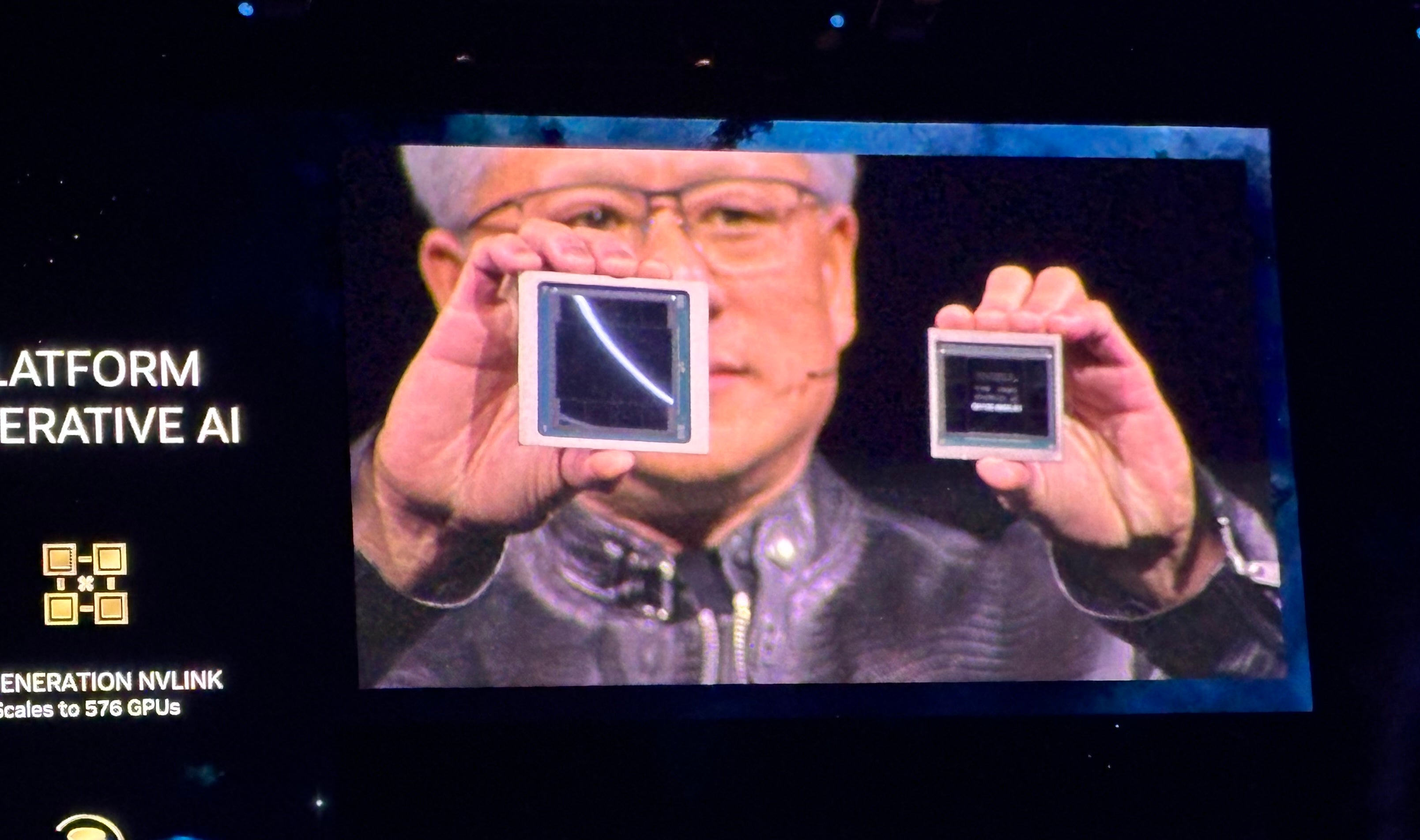
NVIDIA GTC Keynote: Blackwell Architecture Will Accelerate AI Products in Late 2024
NVIDIA’s newest GPU platform is the Blackwell (Figure A), which companies including AWS, Microsoft and Google plan to adopt for generative AI and other modern computing tasks, NVIDIA CEO Jensen Huang announced during the keynote at the NVIDIA GTC conference on March 18 in San Jose, California. Figure A The NVIDIA Blackwell architecture. Image: NVIDIA Blackwell-based products will enter the market from NVIDIA partners worldwide in late 2024. Huang announced a long lineup of additional…
Read More