- The iPad I recommend to most users is only $299 right now
- One of the most versatile action cameras I've tested isn't from GoPro - and it's on sale
- Small Manufacturers, Big Target: The Growing Cyber Threat and How to Defend Against It
- Why I pick this JBL speaker over competing models for outdoor listening
- Testing a smart cooler proved I can never go back to toting ice (and it's on sale)
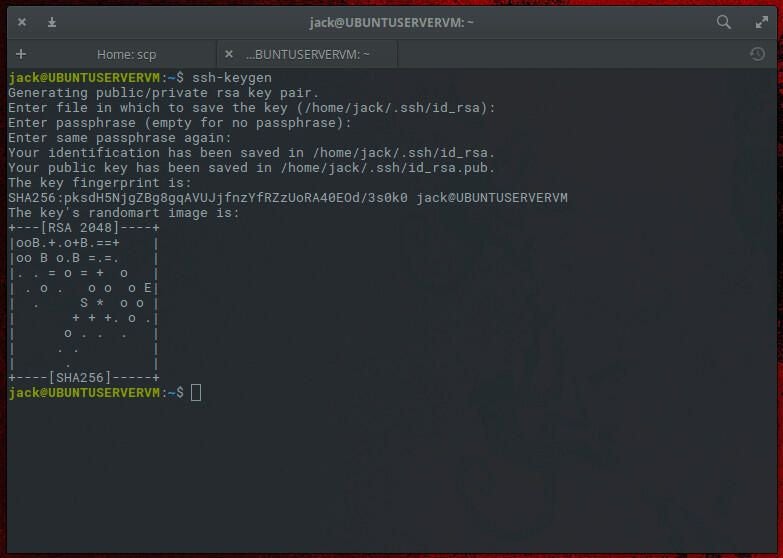
How To Use SCP (Secure Copy) With SSH Key Authentication
Anyone who administers Linux machines knows secure shell. Without this tool, administering those servers remotely would be quite challenging. It would also become harder to move files back and forth, at least with a modicum of security. That’s where secure copy comes into play. With the SCP command, you can copy files to and from a remote Linux server through an encrypted SSH tunnel. SEE: How to View Your SSH Keys in Linux, macOS, and…
Read More