- I recommend the Pixel 9 to most people looking to upgrade - especially while it's $250 off
- Google's viral research assistant just got its own app - here's how it can help you
- Sony will give you a free 55-inch 4K TV right now - but this is the last day to qualify
- I've used virtually every Linux distro, but this one has a fresh perspective
- The 7 gadgets I never travel without (and why they make such a big difference)
TangleBot Campaign Underscores SMS Threat
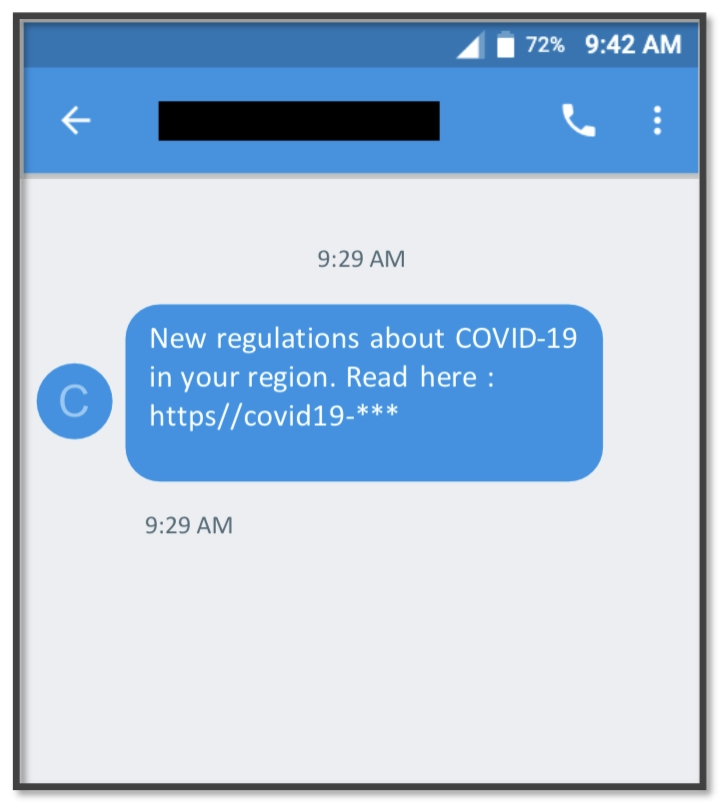
A malware campaign targeting Android devices in the United States and Canada with convincing text messages and links that lead to a downloader has highlighted the danger from SMS spam and phishing, security experts report.
The campaign, dubbed TangleBot, uses coronavirus-themed messages to convince users to click a link, which leads to websites that attempt to collect sensitive information from the victim, according to researchers from email and messaging security firm Cloudmark in a September 23 analysis. The campaign follows attempts by attackers to use SMS phishing, also known as smishing, to perpetrate unemployment insurance fraud in the US.
Remote work has made SMS attacks easier for fraudsters in many ways, says Jacinta Tobin, vice president of global sales and operations at the Cloudmark division of Proofpoint.
“Many people are now working from home, and that, combined with the fact that it is relatively easy to find employees’ cell phone numbers, means that mobile messaging attacks and smishing are emerging as a major threat to enterprises,” she says. “With TangleBot, even if just one employee’s device gets infected, an attacker can launch either a widespread or spear smishing attack.”
TangleBot was named for its “many levels of obfuscation and control over a myriad of entangled device functions, including contacts, SMS and phone capabilities, call logs, internet access, and camera and microphone,” Cloudmark stated in its analysis. The threat allows attackers to make and block calls, send and receive text messages, place overlays on the screen, and record audio and video.
The phishing campaign is just one in a burgeoning trend of SMS phishing, which jumped 256% in the second half of 2020 compared with the first half of that year, the latest numbers available, according to Tobin.
The attacks have also grown more personalized. SMS phishing increasingly uses personal information about a cellphone number’s owner to tailor attacks and make them more convincing. Fake Amazon raffle announcements, sham AT&T refunds, and fraudulent FedEx package delivery notifications are all hitting phones worldwide.
In early August, for example, the US Federal Trade Commission warned Americans that fraudsters had embarked on massive campaigns using unemployment insurance notifications and requests for citizens to correct or verify their information. The US government will not send text messages asking for personal information, stated Seena Gressin, an attorney with the FTC’s Division of Consumer and Business Education, in an August 4 blog post.
“Identity thieves are targeting millions of people nationwide with scam phishing texts aimed at stealing personal information, unemployment benefits, or both,” she wrote.
A Tangled Web of Malicious Functions
In the TangleBot case, once the malware compromises a machine, the attacker can monitor many user activities — such as websites they have visited and passwords they have entered — as well as record audio from the microphone and video from the camera. TangleBot also uses many levels of obfuscation to make analysis difficult, such as placing code in hidden files, bulking up files with unused code, and removing the spaces from the code — a technique known as minification.
“The capabilities also enable the theft of considerable personal information directly from the device and through the camera and microphone, spying on the victim,” Cloudmark’s analysis stated. “Harvesting of personal information and credentials in this manner is extremely troublesome for mobile users because there is a growing market on the dark web for detailed personal and account data.”
TangleBot does not exploit flaws in the Android system, but it socially engineers users to click through multiple dialogue boxes. Depending on how the Android device is configured, as many as nine different dialogue boxes and security alerts would have to be clicked to complete the installation of the software. While on its face such a chain of notifications would appear sufficient, experience has shown users have become accustomed to clicking through warnings.
“Based on what we’ve seen with similar mobile malware attacks recently, such as FluBot attacks that have been active in the UK and Europe, users tend to disregard the multiple warning and permissions and still download and install software from untrusted sources,” Proofpoint’s Tobin says.
Not all attacks on messaging apps require so many steps. Other attackers have found ways to use vulnerabilities in messaging apps, on both Apple and Android phones, to conduct zero-click or one-click attacks, in which just receiving a malicious message or clicking a link in a message is enough to compromise the device.
Cloudmark recommends users question every text message, especially those from an unknown number or claiming to be a known company. In addition, users should not click on the link in the message — instead, they should go directly to the purported company’s site.
So far, the TangleBot attack has not led to other malware, such as ransomware, or account fraud, but Proofpoint expects the attackers to add functionality. While the increase in SMS spam and phishing may seem significant in the US, the UK and European Union have a worse problem, says Tobin. A UK subscriber is 15 times more likely to get a smishing message than a US subscriber, she says.
“While we are seeing growth in all regions globally, the good news is that the US operators have been much faster to secure their networks with technology to block these attacks,” she says.

