- I recommend the Pixel 9 to most people looking to upgrade - especially while it's $250 off
- Google's viral research assistant just got its own app - here's how it can help you
- Sony will give you a free 55-inch 4K TV right now - but this is the last day to qualify
- I've used virtually every Linux distro, but this one has a fresh perspective
- The 7 gadgets I never travel without (and why they make such a big difference)
The Basics of Digital Forensics

By Milica D. Djekic
The digital forensics is a field that assists us to find the clues within a cyberspace regarding some cybercrime or computer breach. The majority of tools used for a digital forensics serve to extract data from a memory, hard drive, removable storage or even websites and transfer them further to a skillful investigator for an analysis. Following all of these, we can conclude that digital forensics investigators may get specialized to some fields. Through this book’s chapter, we would also recommend how forensic staffs could get trained to their tasks.
Why digital forensics matters?
So often, the practice would bring us many cybercrime cases or data breach scenarios which would need a skillful investigation to get proved in a reality. When some cyber incident occurs, the first step being taken would include a good incident response. Next, we should deal with the digital forensics trying to assure the evidence of what happened.
All the staffs working on digital forensic tasks should get prepared to respond to a certain situation which is possible only through regular training, education and exercises. The next phase with a digital forensics would cover data collection using an adequate data acquisition tools and software. Also, those collected information must get analyzed and such a produced finding should get put in a skillfully created report.
Researching this area of cyber defense, we would notice that a digital forensics marketplace is very well-controlled and in the majority of cases – you need to leave your personal details before you get a permission to download any application. In addition, we would mention that this sort of tools is quite expensive, so we would recommend to some beginners or low-budget organizations to try to download some software for free.
Many web locations would offer some freeware or open-source versions of forensic tools and we would like to highlight the Forensic Control website as one of the best forensics tools marketplace offering you a wide spectrum of free applications. Also, in order to gain some experience and knowledge in dealing with digital forensics – we would advise you to take advantage over web resources including learning materials, tutorials and video sessions.
Some commonly used forensic tools
The forensics tools may get used for many different purposes such as disk and memory capture, removable storage history, website data acquisition, operating system registries and much more. Through this book’s chapter, we plan to provide only some basic examples of forensic tools usage and discuss why those matter in a practice. In a Figure 1, we would demonstrate how to use a RAM memory capture forensics tool being suitable for a RAM data collection.
Figure 1. The Magnet RAM Capture
The purpose of tool illustrated in a Figure above would be to capture the RAM memory segment and transfer it to a certain destination for an analysis. That task would require a well-trained investigator that would analyze data and provide an expert’s report to some trusted organization. Many defense and justice systems would rely on these findings taking them into a consideration in a case of deciding on someone’s legal status. The Figure 2 would illustrate Forensic Acquisition of Website software.
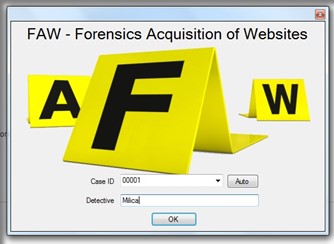
Figure 2. The Forensics Acquisition of Website
As it’s represented through the previous picture, the Forensic Acquisition of Website tool is quite easy to handle for the reason it would need a case ID and detective details at its beginning. The next step with this application would get provided through a Figure 3 illustrating how such a software may capture the entire website and gather all the data.
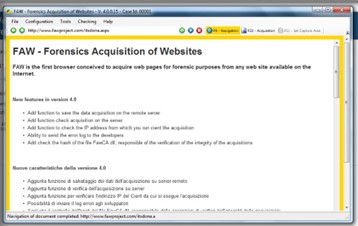
Figure 3. The FAW tool perspectives
The FAW software would capture the entire website offering you navigation, acquisition and setting of capture area. We would highly recommend to everyone to try testing tools being given at the Forensics Control website. Also, some developing societies could attempt to select some of these free tools for their digital forensics investigations. We believe some comparative analyses and researchers could offer the answer to a question if these freeware tools may replace the commercial ones in some sense.
The goals of such a conducted investigation
The primary goal of digital forensic investigation would be to find the evidence about a cyber breach that occurred. Also, the reporting as such an important step with the investigation should offer us a better understanding how such an incident happened and who the key players of that campaign could be. Also, as this sort of investigation is so important to a court process, we would advise the investigators to prepare as good reports as they could – giving lots of information and examples to justice sector staffs.
Some developing countries would still struggle – not having enough skillful staff with policing and justice system that could deal with this modern time and its technological advancements. For such a purpose, we would strongly recommend to those societies to pay more attention to education and training of their employees making them qualified to cope with these new challenges.
The finishing talk
The role of this book’s chapter would be to get a closer look at all the concerns and challenges of digital forensics. This practical part of the book would guide us through some basic concepts and could also get used as a training material trying to demonstrate some of the tools being available through the Forensics Control webpage. For more advanced courses, we would suggest much deeper research being conducted in order to contribute with a better insight in an analysis and reporting within a digital forensics.
About The Author
 Milica D. Djekic is an Independent Researcher from Subotica, the Republic of Serbia. She received her engineering background from the Faculty of Mechanical Engineering, University of Belgrade. She writes for some domestic and overseas presses and she is also the author of the books“The Internet of Things: Concept, Applications and Security”and “The Insider’s Threats: Operational, Tactical and Strategic Perspective”being published in 2017 and 2021 respectively with the Lambert Academic Publishing. Milica is also a speaker with the BrightTALK expert’s channel. She is the member of an ASIS International since 2017 and contributor to the Australian Cyber Security Magazine since 2018. Milica’s research efforts are recognized with Computer Emergency Response Team for the European Union (CERT-EU), Censys Press, BU-CERT UK and EASA European Centre for Cybersecurity in Aviation (ECCSA). Her fields of interests are cyber defense, technology and business. Milica is a person with a disability.
Milica D. Djekic is an Independent Researcher from Subotica, the Republic of Serbia. She received her engineering background from the Faculty of Mechanical Engineering, University of Belgrade. She writes for some domestic and overseas presses and she is also the author of the books“The Internet of Things: Concept, Applications and Security”and “The Insider’s Threats: Operational, Tactical and Strategic Perspective”being published in 2017 and 2021 respectively with the Lambert Academic Publishing. Milica is also a speaker with the BrightTALK expert’s channel. She is the member of an ASIS International since 2017 and contributor to the Australian Cyber Security Magazine since 2018. Milica’s research efforts are recognized with Computer Emergency Response Team for the European Union (CERT-EU), Censys Press, BU-CERT UK and EASA European Centre for Cybersecurity in Aviation (ECCSA). Her fields of interests are cyber defense, technology and business. Milica is a person with a disability.

